Nginx, pronounced like “engine-ex”, is an open-source web server that, since its initial success as a web server, is now also used as a reverse proxy, HTTP cache, and load balancer.
Some high-profile companies using Nginx include Autodesk, Atlassian, Intuit, T-Mobile, GitLab, DuckDuckGo, Microsoft, IBM, Google, Adobe, Salesforce, VMWare, Xerox, LinkedIn, Cisco, Facebook, Target, Citrix Systems, Twitter, Apple, Intel, and many more (source).
Nginx was originally created by Igor Sysoev, with its first public release in October 2004. Igor initially conceived the software as an answer to the C10k problem, which is a problem regarding the performance issue of handling 10,000 concurrent connections.
Because its roots are in performance optimization under scale, Nginx often outperforms other popular web servers in benchmark tests, especially in situations with static content and/or high concurrent requests, which is why Kinsta uses Nginx to power its hosting.
How Does Nginx Work?
Nginx is built to offer low memory usage and high concurrency. Rather than creating new processes for each web request, Nginx uses an asynchronous, event-driven approach where requests are handled in a single thread.
With Nginx, one master process can control multiple worker processes. The master maintains the worker processes, while the workers do the actual processing. Because Nginx is asynchronous, each request can be executed by the worker concurrently without blocking other requests.
Some common features seen in Nginx include:
- Reverse proxy with caching
- IPv6
- Load balancing
- FastCGI support with caching
- WebSockets
- Handling of static files, index files, and auto-indexing
- TLS/SSL with SNI
At Kinsta, you can check out Nginx and all of our other premium add ons.
Nginx vs Apache Usage Stats
Apache is another popular open-source web server. In terms of raw numbers, Apache is the most popular web server in existence and is used by 43.6% (down from 47% in 2018) of all websites with a known web server, according to W3Techs. Nginx comes in a close second at 41.8%.
Netcraft ran a survey across 233 million domains and found Apache usage at 31.54% and Nginx usage at 26.20%.
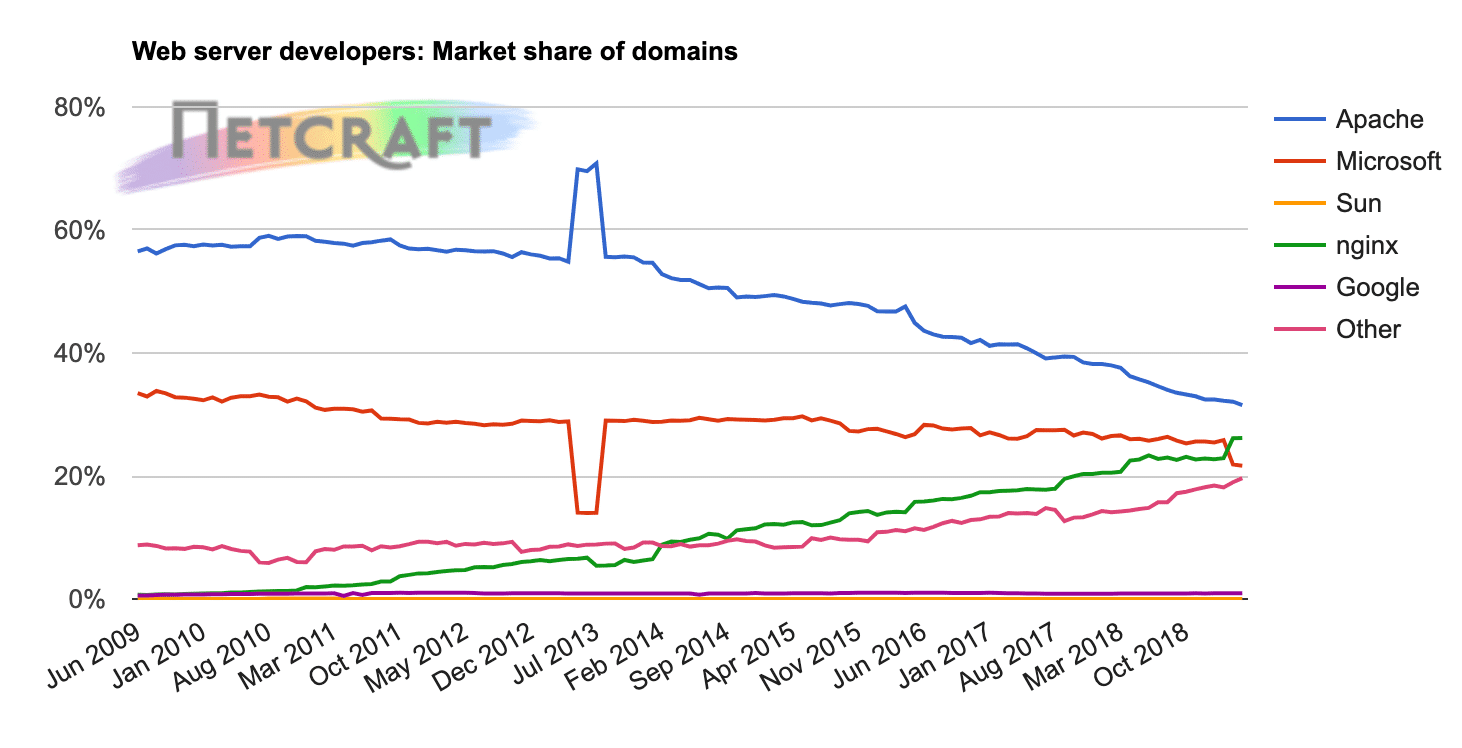
While Apache is the most popular overall option, Nginx is actually the most popular web server among high-traffic websites.
When you break down usage rates by traffic, Nginx powers:
- 60.9% of the 100,000 most popular sites (up from 56.1% in 2018)
- 67.1% of the 10,000 most popular sites (up from 63.2% in 2018)
- 62.1% of the 1,000 most popular sites (up from 57% in 2018)
In fact, Nginx is used by some of the most resource-intensive sites in existence, including Netflix, NASA, and even WordPress.com.
Apache’s usage, on the other hand, moves in the opposite direction as a site’s traffic increases. It powers:
- 24.0% of the 100,000 most popular sites (down from 27.1% in 2018)
- 18.8% of the 10,000 most popular sites (down from 21.5% in 2018)
- 16.6% of the 1,000 most popular sites (up from 16.2% in 2018)
If we take a look at Google Search terms since 2004 we can see that Apache has been on a steady decline, while NGINX has seen slight growth.
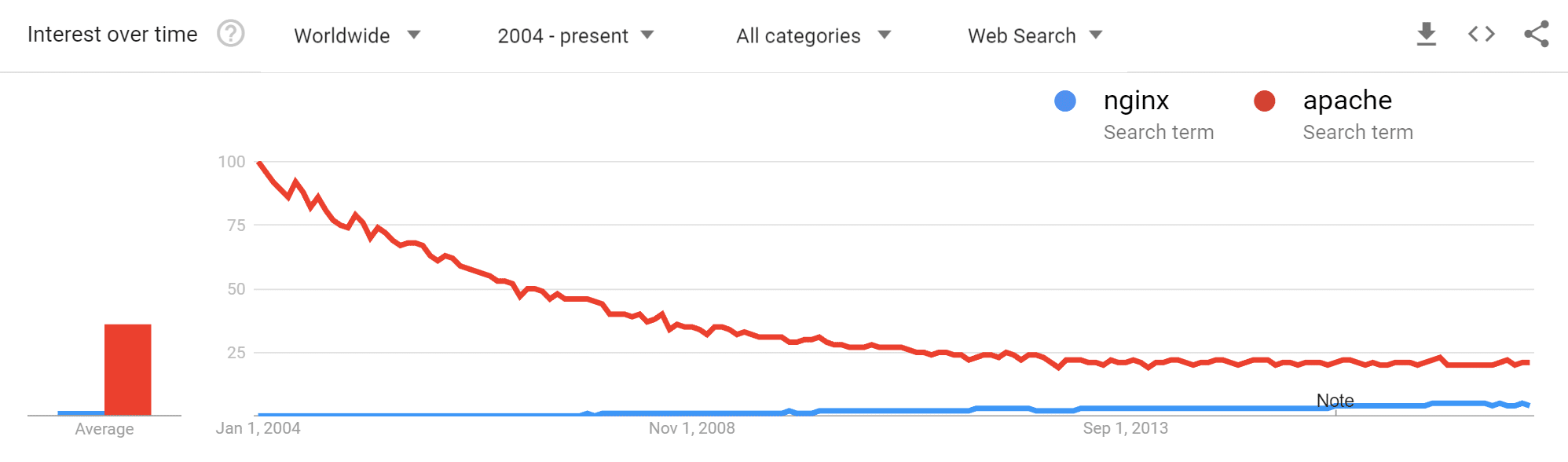
Again, when you consider that NGINX performs better under scale, it’s not surprising that high-traffic websites opt for NGINX over Apache. Check out our more in-depth comparison of Nginx vs Apache.
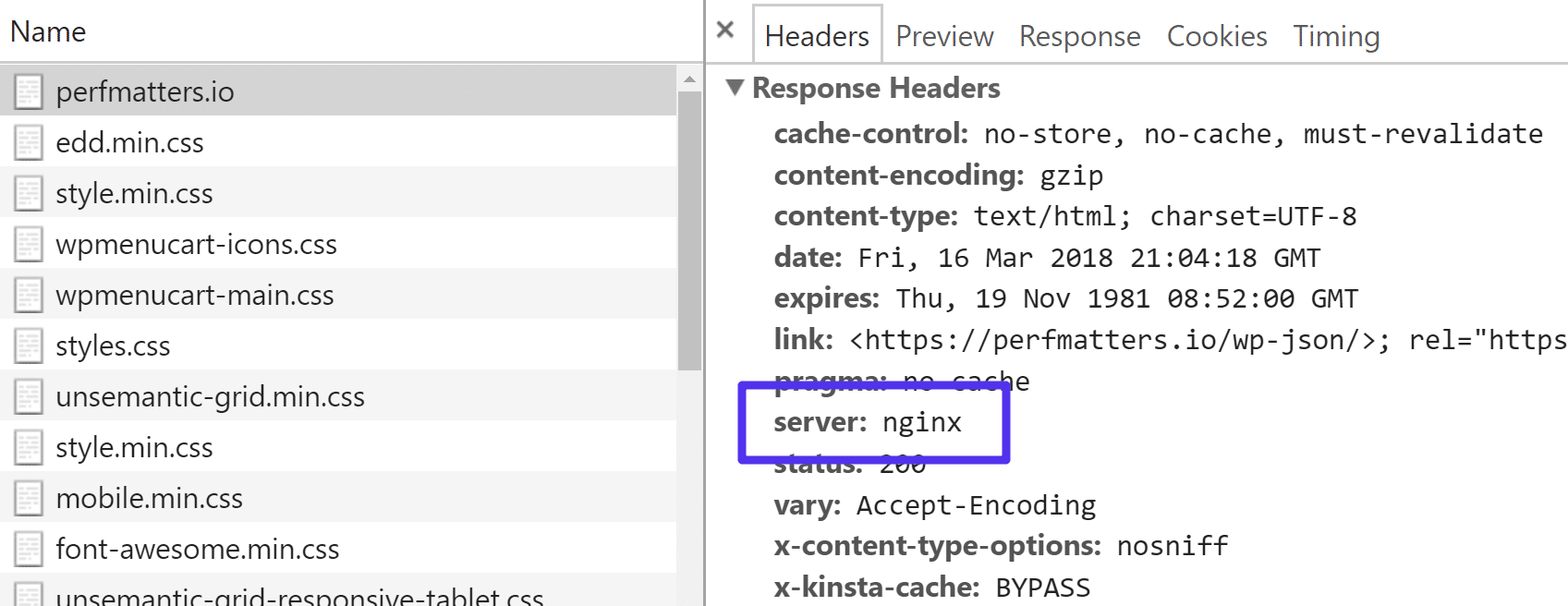
How to Check If You’re Running Nginx or Apache
On most websites, you can simply check the server HTTP header to see if it says Nginx or Apache. You can see HTTP headers by launching the network tab in Chrome Devtools. Or you can check headers in a tool like Pingdom or GTmetrix.
However, the HTTP header might not always reveal the underlying web server. For example, if your WordPress site is behind a proxy service such as Cloudflare, the server HTTP header will then say cloudflare instead.