We’ve enhanced secure file transfer protocol (SFTP) and secure shell (SSH) configuration options within the MyKinsta dashboard to give Managed WordPress Hosting customers more control over site security.
The new features support:
- Disabling SFTP/SSH access (and re-enabling it)
- Auto-expiration of passwords
- Enabling/disabling passwords as an authentication method
- Downloading access configuration information for use in third-party applications
Everything happens on the Site Information page in MyKinsta, found under WordPress Sites > sitename > Info, in the SFTP/SSH panel:
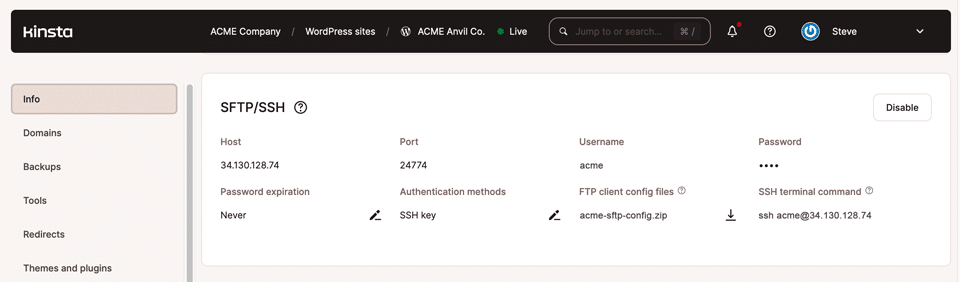
These details are unique to each WordPress environment. So, staged website environments will have access details that vary from those of the related live site.
Let’s look at the new configuration options you’ll find here.
Disabling (and re-enabling) SFTP/SSH access
The most decisive way to secure SFTP/SSH access to your website environment is to turn it off completely. This could be a good move if you rarely use these protocols to work on your website. It’s easy to toggle this setting, so you might even enable SFTP/SSH only when you are using it.
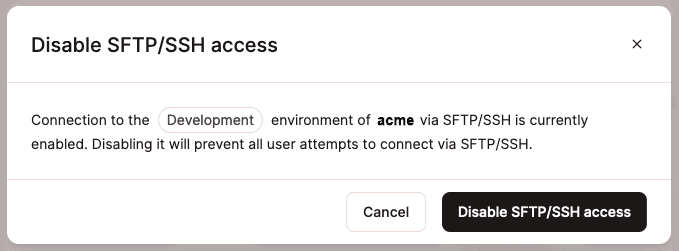
If SFTP/SSH is currently enabled, you’ll see a Disable button in the panel’s upper-right corner. Click the button, and you will be prompted to confirm the action:
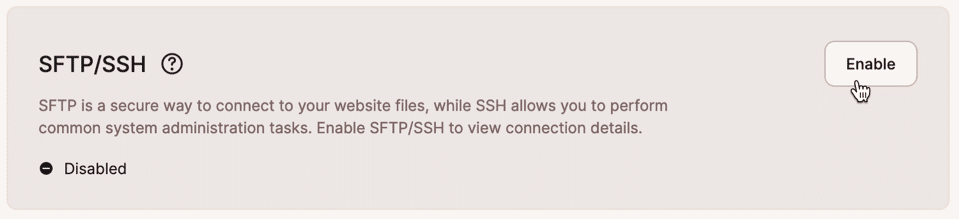
When SFTP/SSH is disabled for a website environment, configuration details are not relevant, so the entire SFTP/SSH panel is grayed out, and an Enable button repaces the Disable button:
Setting a password expiration period
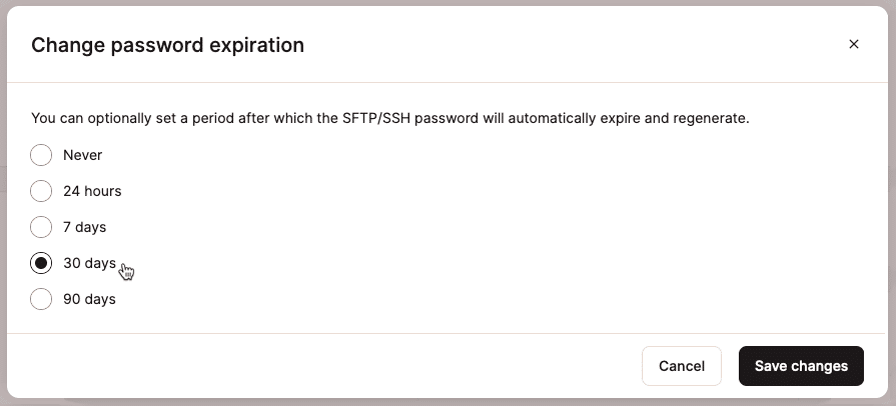
By default, passwords created in MyKinsta for SFTP/SSH access do not expire automatically. Click the edit (pencil) icon beside the Password expiration label to choose an automatic expiry option:
When you enable automatic expiry, Kinsta’s system will generate a new password at the end of your chosen period. You can access the new password by revealing it or copying it on the SFTP/SSH panel.
Changing permitted authentication methods
By default, SFTP/SSH access to WordPress environments at Kinsta can be authenticated by passwords and SSH key pairs. To disable or re-enable password authentication, click the edit (pencil) icon beside the Authentication methods label. You will see this prompt:
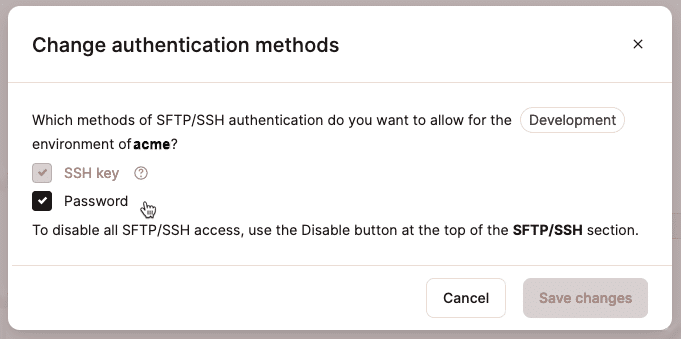
Key-based authentication is always available as long as SFTP/SSH is enabled. You can select or deselect the Password option and then click the Save changes button.
Downloading SFTP/SSH configuration information
Some SFTP and SSH client software can import connection settings from structured configuration files. You can download your environment’s current SFTP/SSH access settings in multiple file formats.
Click the download icon beside the FTP client config files label to download these documents as a ZIP archive. Inside the archive, you’ll find files like these:
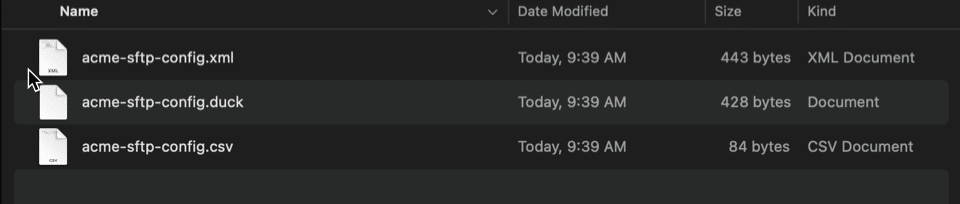
The file formats above and examples of client software that use them are:
- .xml – Supported by FileZilla.
- .csv – Used by Terminus.
- .duck – These files are pretty much exclusive to Cyberduck
Below is an image of the FileZilla Site Manager after importing the acme-sftp-config.xml file shown above:
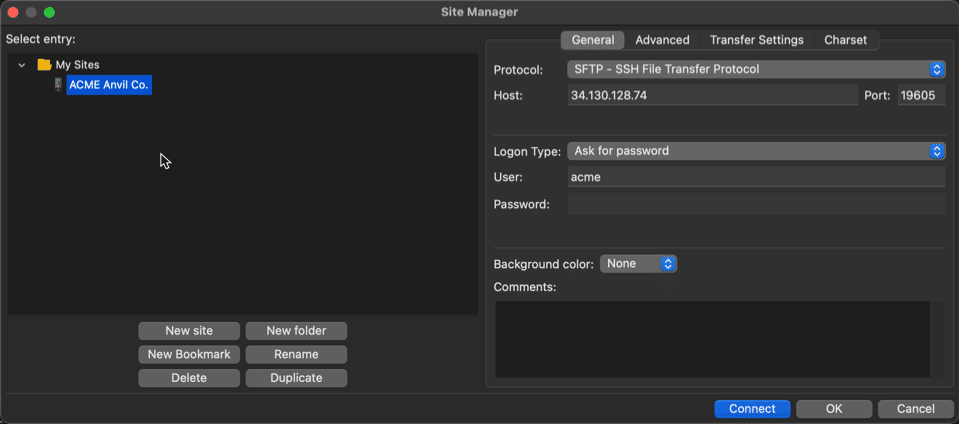
The client configuration files do not include passwords or shared-key data. You will provide that information within the client before connecting.
We’re serious about security at Kinsta
Looking for secure cloud hosting? Learn how Kinsta leverages the Google Cloud and Cloudflare to provide firewalling, DDoS protection, and free wildcard SSL.
And independent auditors have confirmed our compliance with System and Organization Controls (SOC) security standards. You can request access to Kinsta’s SOC 2 Type II report from our Trust report page.
