When choosing the right web hosting for your sites, you consider factors like speed, security, pricing, and scalability. Hosting providers try to meet those needs in different ways: with shared hosting, dedicated hosting, virtual private server hosting, and more.
In the past, we have written several guides comparing the various types of hosting, but in this guide, we explore isolated container technology and the underlying container technology of Kinsta’s infrastructure.
What are containers?
Before diving into isolated container technology, let’s consider what containers are. Containers are standalone packages that include everything needed to run an application, including the code, runtime, system tools, and libraries.
Unlike traditional virtualization, where each virtual machine (VM) runs its operating system, containers share the host OS kernel, which makes them lightweight and efficient.
Benefits of container technology
There are several advantages to using containers in web hosting, including:
- Portability: Containers encapsulate an application and its dependencies, making them highly portable. You can easily move a container from one hosting environment to another (like from a developer’s laptop to a test environment and then to production) without worrying about inconsistencies or compatibility issues.
- Consistency and efficiency: Containers enhance web hosting by efficiently using resources while ensuring applications run consistently across all environments, from development to production.
- Rapid deployment and scaling: Containers can be created and deployed quickly — a significant advantage in continuous integration and continuous delivery (CI/CD) environments. They also allow for quick recovery in case of a failure, as you can rapidly start a new container with the same configuration.
- Isolation and security: Containers provide an isolated environment for each application or service. This isolation ensures that the processes within a container do not affect other containers or the host system. This improves security, as issues in one container are contained and don’t impact others.
Challenges of container technology
Though there are many good things about using containers in web hosting, there are a few drawbacks as well:
- Security concerns: In web hosting, ensuring the security of containers is crucial as they share the host’s OS kernel. One container’s vulnerabilities could risk the entire server’s security, necessitating strong isolation and security practices.
- Complexity: Managing multiple containers for web hosting can be complex. Orchestrating these containers’ deployment, scaling, and maintenance requires expertise, especially when using tools like Kubernetes for larger setups.
- Storage challenges: Containers are stateless, posing challenges for persisting data in web hosting scenarios. Effective strategies are needed to ensure data from websites and applications remain intact even when containers are restarted or removed.
- Networking: Setting up and managing network configurations for containers in web hosting is complex. This involves ensuring containers can communicate effectively with each other and with external networks while maintaining security and performance.
- Compatibility issues: Ensuring that web applications run consistently across various environments is challenging. Differences in operating systems and dependencies can cause compatibility issues, requiring careful management and testing of container images.
The need for isolation
While containers provide several advantages over traditional software deployment methods, they have limitations.
One significant concern is the potential for security vulnerabilities when running multiple containers on a single host. If one container is compromised, there is a risk that the attacker could gain access to other containers on the same host.
Additionally, containers often compete for system resources like CPU, memory, and network bandwidth. This competition can lead to unpredictable performance and resource contention issues when containers are not properly isolated.
Container isolation refers to the practice of limiting the interactions and communications among containers within a containerized environment. This isolation guarantees that every container functions independently and securely, avoiding interference with other containers on the same host system.
Isolation in container technology relies primarily on two mechanisms:
- Namespaces: Containers use namespaces to create separate instances of system resources such as processes, networks, and filesystems. This prevents one container from accessing or modifying the resources of another container.
- Control Groups (cgroups): cgroups complement namespaces by limiting and prioritizing the resources (CPU, memory, I/O, network, etc.) that processes in a namespace can use. This ensures that a particular container doesn’t monopolize system resources, maintaining overall system stability and efficiency.
Isolated container technology vs shared hosting
Shared hosting is a more traditional form of hosting where multiple websites share resources on a single server. This cost-effective method is a popular choice for small businesses, bloggers, and individuals with limited budgets.
Shared hosting providers typically offer user-friendly control panels and easy setup processes, lowering the technical barrier to entry. However, the shared nature of resources means that high traffic or resource usage by one website can impact the performance of others on the same server.
Additionally, shared hosting poses higher security risks; if one website is compromised, others on the same server could be affected.
The choice between isolated container technology and shared hosting hinges on the specific needs and capabilities of the user. Isolated containers are ideal for those prioritizing security, stability, and scalability but come at a higher cost and require more technical know-how.
Shared hosting, while more affordable and user-friendly, has performance, security, and flexibility limitations, making it more suitable for smaller, less resource-intensive websites.
Understanding how Kinsta uses isolated container technology
Kinsta’s application, database, and managed WordPress hosting plans don’t fall into traditional hosting categories. Unlike other hosts, which are cheaper and less secure, Kinsta’s infrastructure is built for performance. We maintain a custom and containerized hosting stack that does not compromise quality.
Kinsta uses Linux containers (LXC) and LXD as the underlying container technology for our WordPress hosting infrastructure on the Google Cloud Platform (GCP), ensuring complete isolation for each account and WordPress site.
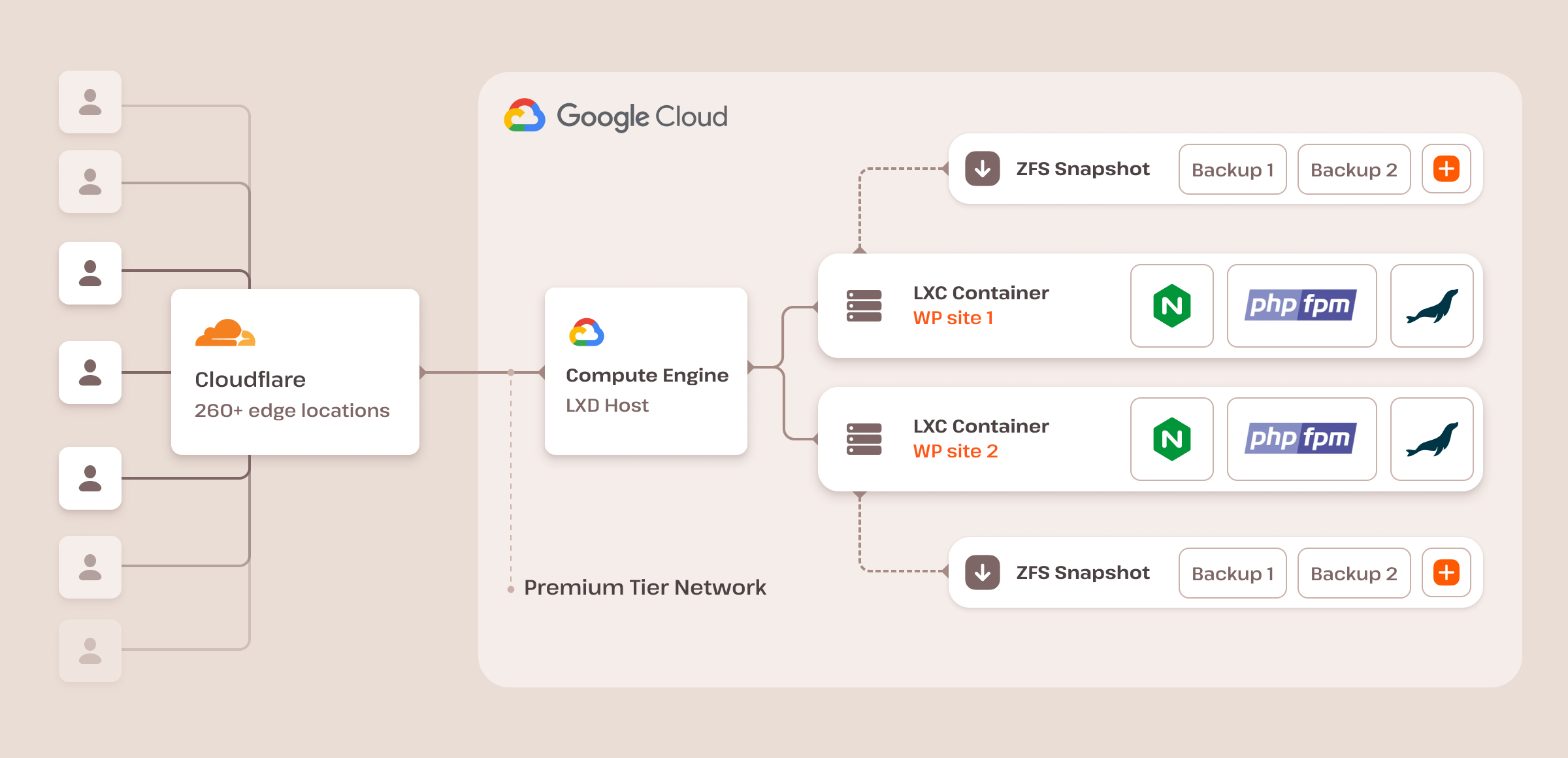
However, it’s important to note that our approach to Application and Database hosting is slightly different. These services are hosted on Kubernetes, which is also housed on GCP and protected by Cloudflare.
Our platform ensures each site runs in a dedicated, isolated software container equipped with all necessary software resources (Linux, NGINX, PHP, MySQL), guaranteeing 100% privacy and no resource sharing, even between your own sites.
These containers run on a generously sized virtual machine in one of the multiple GCP data centers, secured by our free Cloudflare integration. Additionally, we employ encryption at rest to safeguard customer data, ensuring top-notch security and privacy.
On our standard plans, each live site container can access 12 CPUs and 8 GB of RAM by default. Each staging environment on our standard plans has access to 1 CPU and 8 GB of RAM.
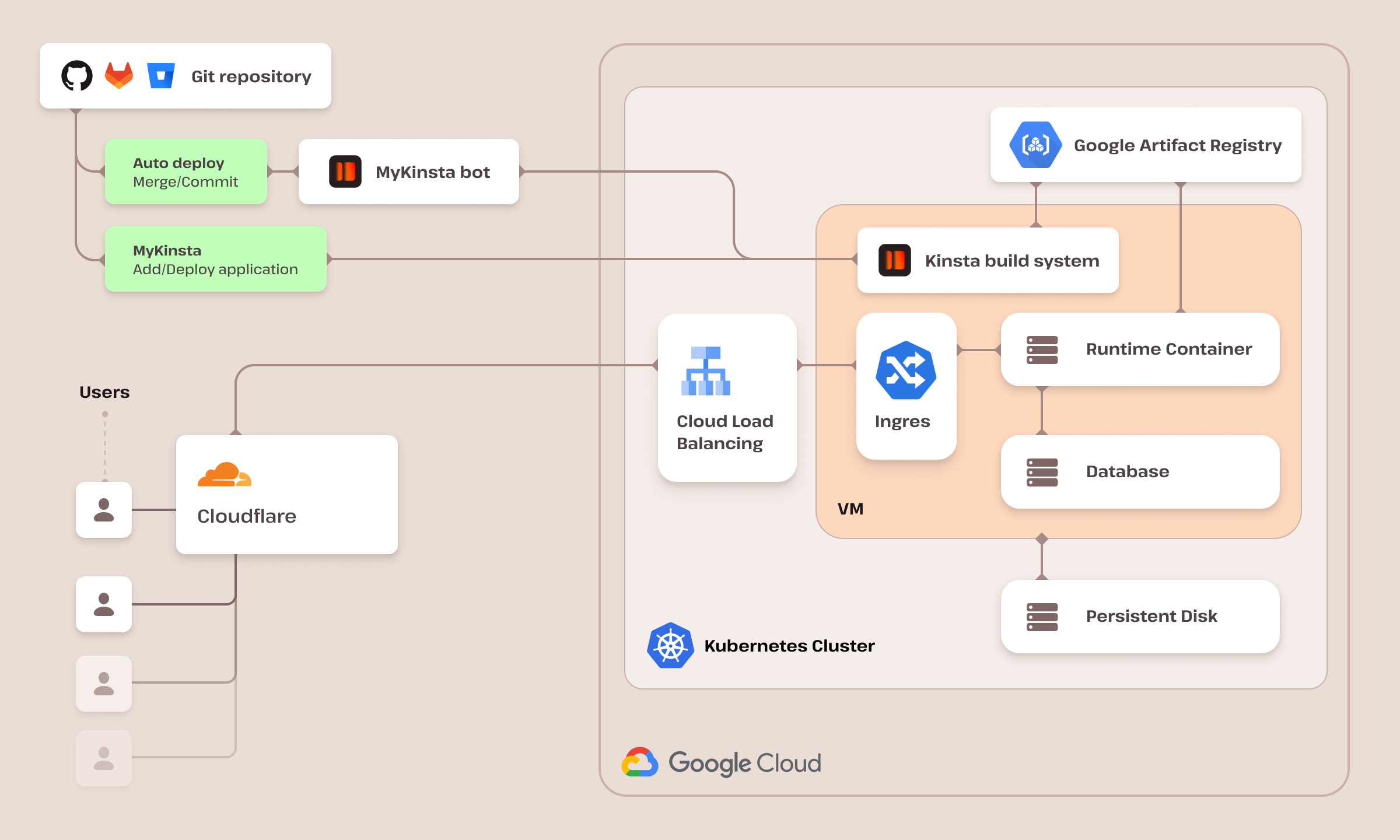
We also have a custom-designed dashboard (MyKinsta) that streamlines the creation and management of your website, all without the need for an external setup. It provides comprehensive access to vital information and tools, including detailed analytics, logs, backups, and more.
Our application and database hosting service simplifies your work by eliminating the complexities of orchestrating container deployment, scaling, and maintenance. With our user-friendly dashboard, you can effortlessly create databases and deploy applications.
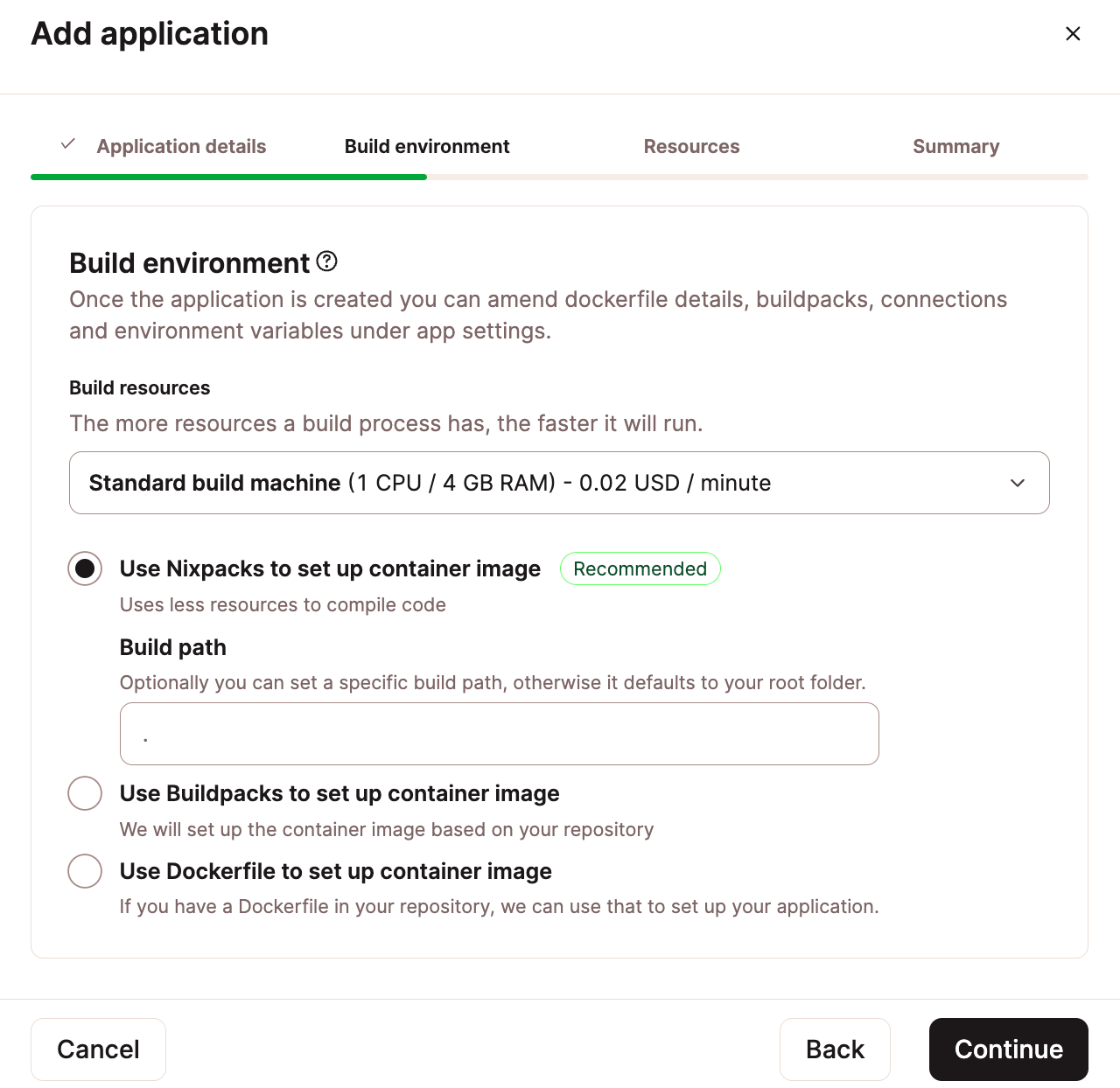
We offer versatile options for creating container images, including Nixpacks, Buildpacks, and Dockerfile. Additionally, our service supports automatic horizontal scaling, ensuring your applications perform optimally without the need for specialized expertise.
Summary
Now that you know what isolated container technology means, how it works, its features, and its advantages and disadvantages, you’re fully equipped to decide whether your website needs it.
If you’re looking for more reliable and secure hosting for your WordPress sites, we suggest choosing our managed WordPress hosting solution, which houses every WordPress site in its isolated container.
Check out what our customers say, or contact us to learn more about our managed hosting solution and how it excels on the isolated container technology.