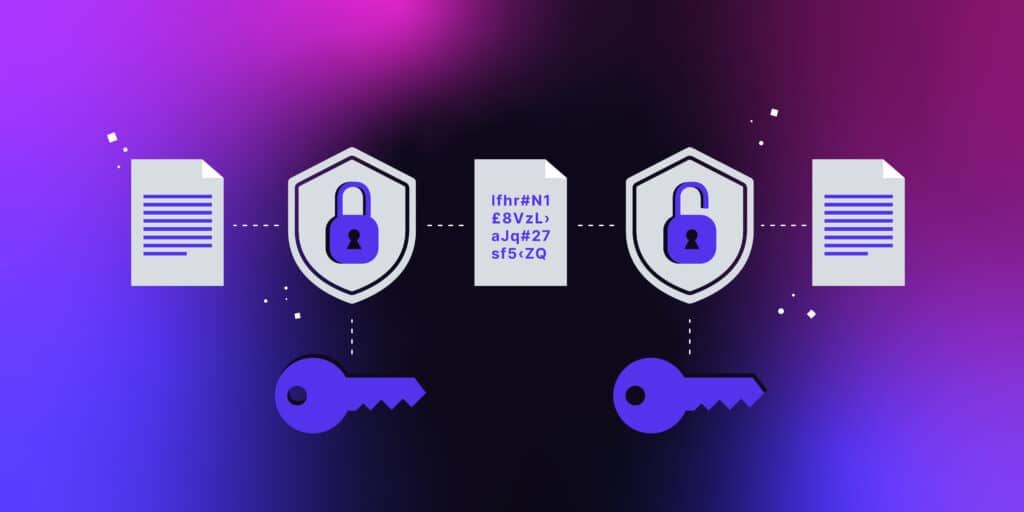
Imagine you wanted to send a text message and be sure that no one except the intended recipient could read it. How would you do it? In a word: encryption.
Encryption converts regular text into a coded language that only someone with the right key can decode. It is used to secure communication, protect sensitive information, and prevent data breaches. Encryption is routinely used in daily life in ways you may not even notice, such as securing your credit card information during online purchases.
This article will explore encryption theories, types, and practical uses that help keep our digital world safe.
What Is Encryption?
Encryption is the process of encoding readable text into secure code. It’s a fundamental technology for securing information against outside access.
Historically, it has been used in spycraft and wartime for sensitive communications, but the more familiar applications today center on online data.
Personal information, financial data, and confidential documents shared online must be encrypted to secure them properly against cybercrime.
Encryption uses a formula called a “cipher” or an encryption algorithm, which ensures that anyone who tries to intercept information communicated across a digital space cannot read its true contents.
Encryption unlocks information for the intended recipient alone by using a special key that only their device will have. Anyone without this key will be unable to properly decrypt the message.
What Is Encryption in Cybersecurity?
Encryption is a pillar of many cybersecurity protocols and procedures. For example, if cyber attackers breach your network, easily-accessed personal and confidential information could be at risk of theft and either held for ransom or sold to the highest bidder.
However, if your device stores only encrypted information, the data that the hackers access will be rendered useless, as they cannot read it without the correct secret key.
Many regulations now require encryption as part of their set of cybersecurity standards. This is especially true for organizations that store Private Personal Information (PPI), such as financial and healthcare institutions.
What Is the Purpose of Data Encryption?
The fundamental purpose of encryption is to protect sensitive information being seen by those with unauthorized access. Encrypting communications helps you maintain data confidentiality during transmission and storage.
This is especially important to people and organizations whose private data is particularly sensitive or confidential, such as banks, healthcare providers, military organizations, power and energy companies, and insurance providers.
Data encryption allows these types of organizations to hold onto personal information in a secure way that will not compromise your identity. Regular individuals may want to protect their information, too.
Encryption prevents your information from being tampered with. In a digital age that lacks trust, encryption can make you feel more secure that the information you send and receive is authentic. Improving data integrity and authenticity is another of encryption’s core benefits.
Types of Data Encryption
There are many different types of encryption, each with varying levels of security and usability. Let’s explore the most common forms of encryption and the benefits and disadvantages of each of them.
Symmetric Encryption
Symmetric encryption is when a single encryption key is used to encrypt and decrypt information. This means that the key must be shared with both the person sending the information and the person receiving the information.
Symmetric encryption can be created using a block algorithm or a stream algorithm. Using a block algorithm, the system utilizes a unique secret security key to encrypt set lengths of bits in blocks. On the other hand, a stream algorithm does not retain encrypted data in its memory but encrypts it as it flows in.
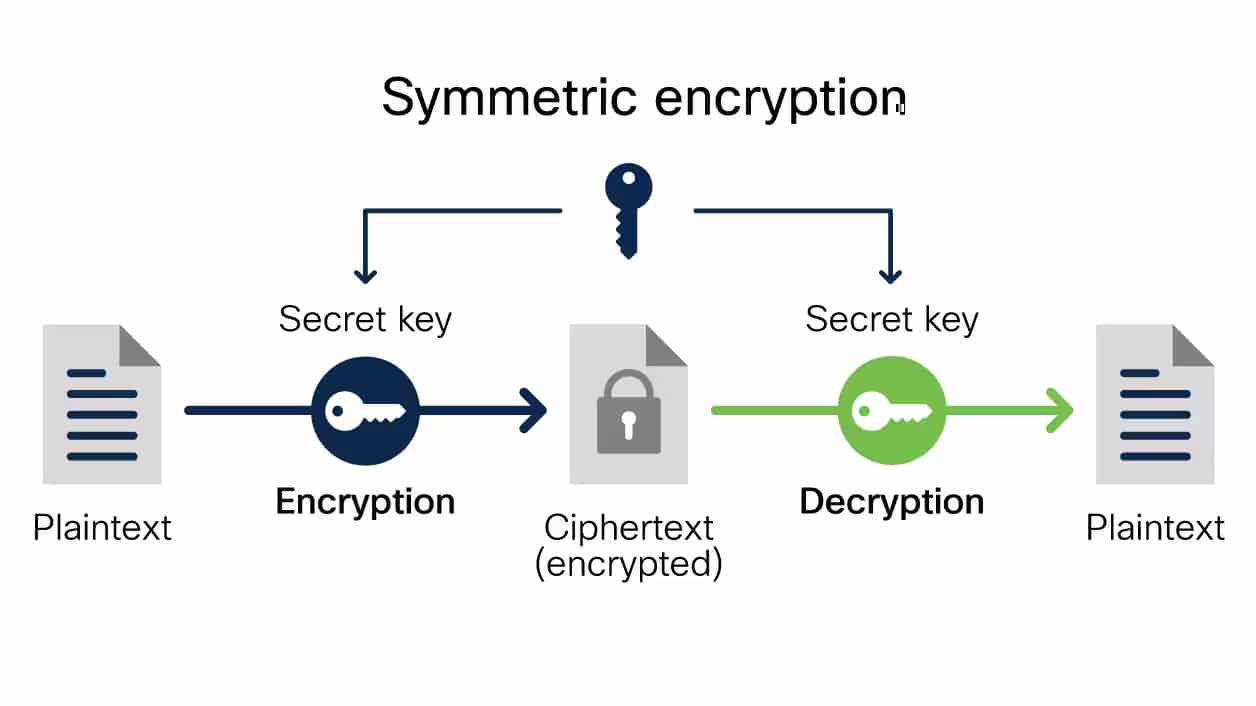
The benefits of symmetric encryption are that it is a very fast form of encryption and is good to use for bulk encryption needs. However, symmetric keys are difficult to manage at a mass scale and can reduce the security of transmitted messages if their key information has been leaked.
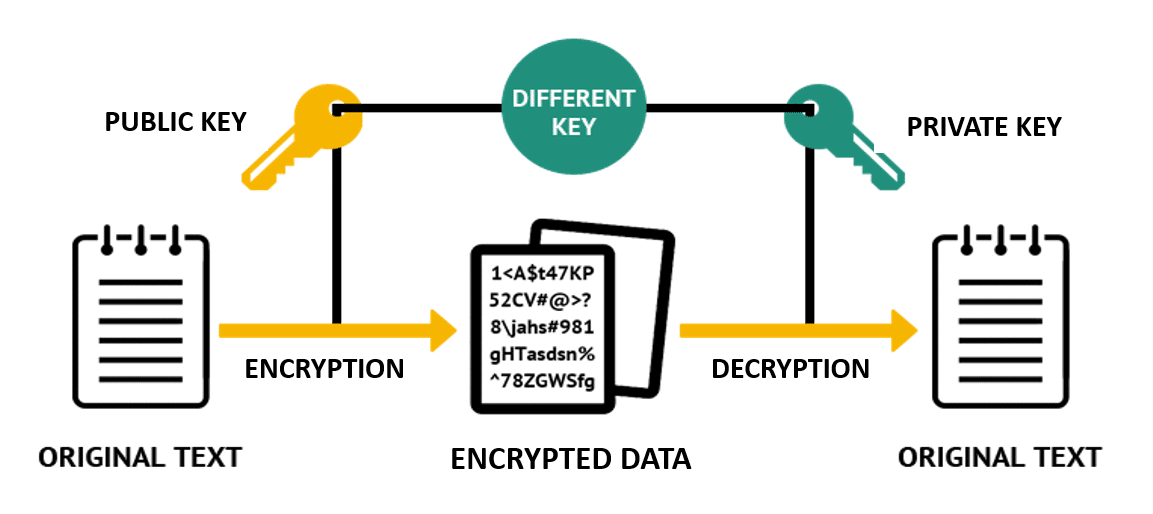
Asymmetric Encryption
Unlike symmetric encryption, asymmetric encryption uses one key for encrypting information and a separate key for decryption.
Asymmetric encryption is also known as public-key encryption, as the key to encryption information is available publicly and can be used by many people. Meanwhile, the person receiving the message has a corresponding private key used to decrypt the message.
Asymmetric encryption is used in many fundamental internet protocols. One application is used in Transport Layer Security (TLS) and Secure Sockets Layer (SSL).
Another common use of asymmetric encryption is in software that requires a connection to be established over an insecure network. By encrypting the information communicated across that connection, browsers and other digital communication devices can maintain security.
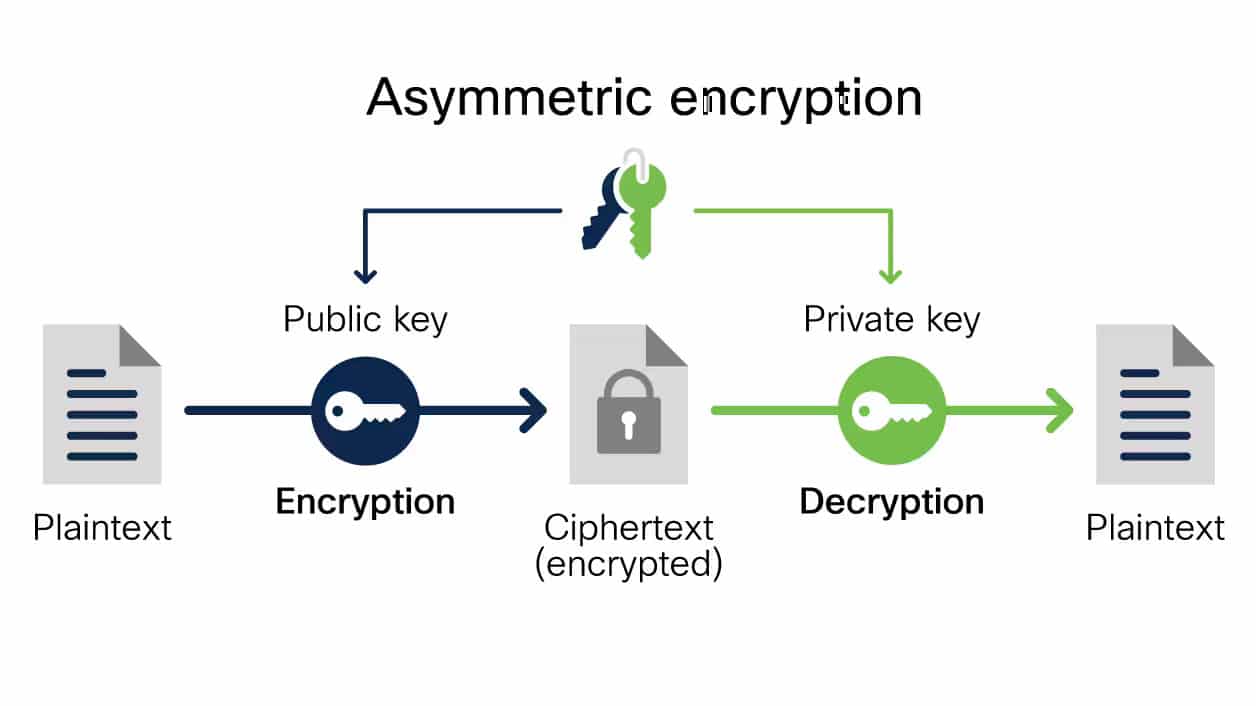
It’s important to note that public keys used in encryption do not hide metadata, meaning that information about which computer the message came from or when it was sent will be available.
It is also a much slower form of encryption. Interestingly, one of its common uses is to send the symmetric encryption key to the receiver of a message.
Hashing
Hashing is a process for applying an algorithm that transforms input data into a fixed-length output. The same input will always result in the same hash string output, so comparing hash results is useful for verifying data integrity.
For security purposes, sensitive information can be hashed and stored in ‘hash tables,’ such as when an organization stores passwords in hashed form rather than in plaintext.
Hashing is frequently mislabelled as a type of encryption. While it is a cryptography tool, it is not considered encryption, as hashed information can be recreated without a secret key.
What Is an Encryption Algorithm?
Regardless of whether you are using symmetric or asymmetric encryption, the secret keys exchanged must use an algorithm to encrypt information.
These algorithms are created using a mathematical formula or a set of rules. Using the specific mathematical formula that has been created for that type of encryption, the algorithm converts plaintext into cipher text. Utilizing standardized algorithms ensures that text can always be decrypted in a predictable way.
There are several different common encryption algorithms, each used for different purposes, industries, or required levels of security.
What are Common Encryption Algorithms?
1. Data Encryption Standard (DES)
The Data Encryption Standard (DES) was developed by IBM in the 1970s and was first used by the United States government to send and receive private information.
It is a symmetric-key algorithm for encrypting electronic data. It uses a block algorithm with 56 bits to encrypt information.
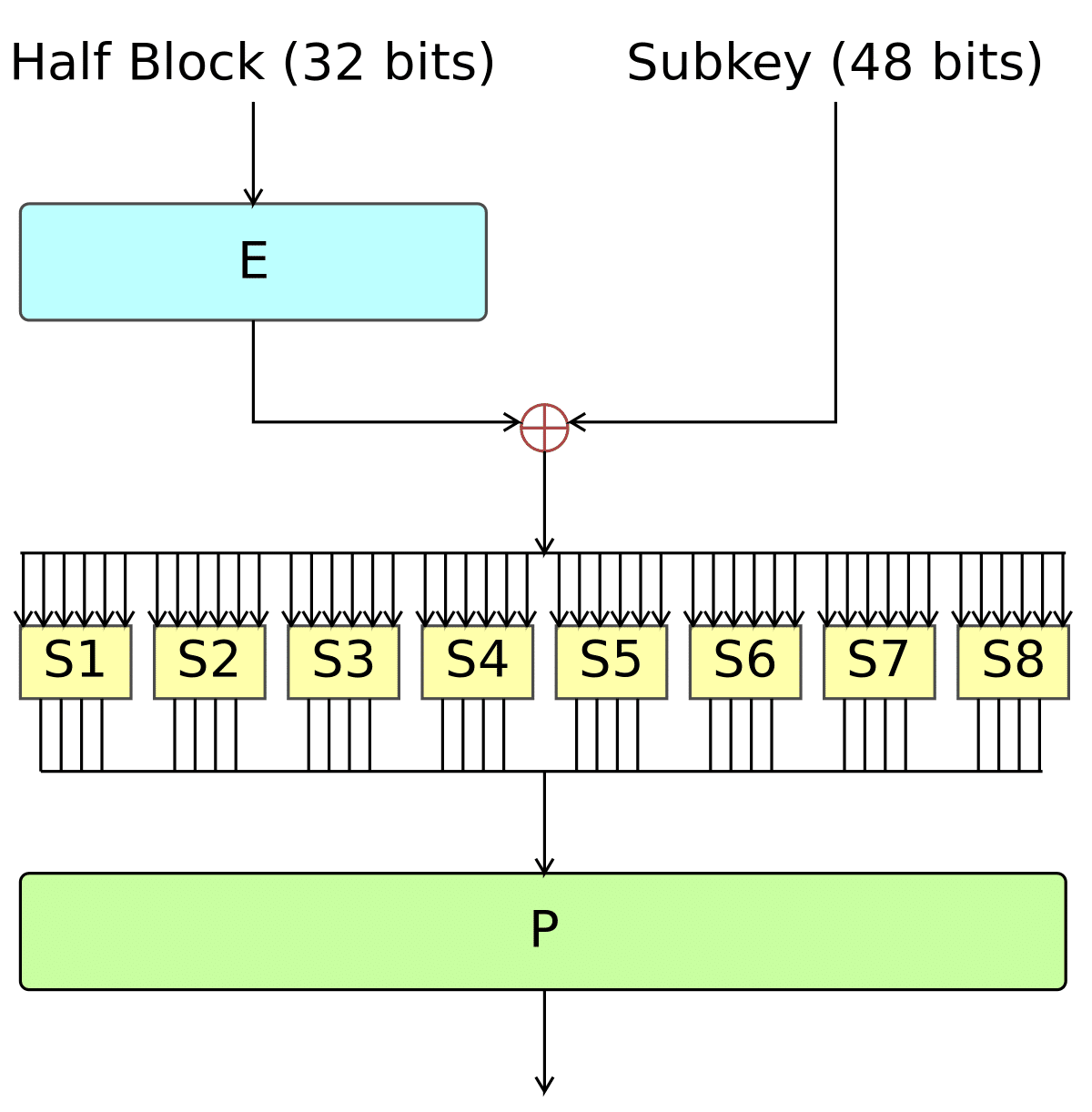
As it is an older form of encryption, it is no longer considered secure for most cryptographic functions today. As computers evolved, the 56 bits were not enough to securely protect information because newer devices’ improved computing power could crack the DES algorithm quickly.
However, the DES algorithm paved the way for stronger and more advanced encryption algorithms to follow it.
2. Triple Data Encryption Standard (3DES)
One of the first attempts to improve on the original DES encryption model produced the Triple Data Encryption Standard (3DES).
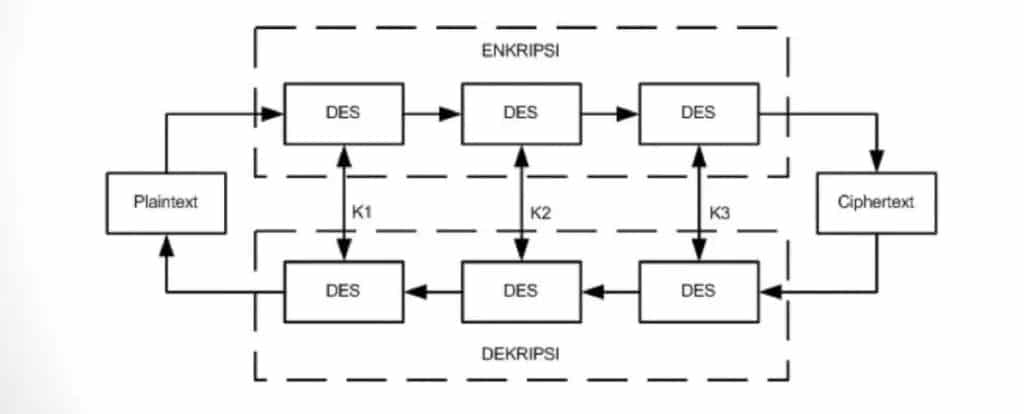
3DES is also a symmetric encryption block algorithm. Its block cipher uses 64-bit blocks to encrypt information. However, instead of stopping there as DES does, it goes through three rounds of encryption to provide a higher level of security that further hides the original message.
Even so, the National Institute of Standards and Technology (NIST) has stated that as of the end of 2023, 3DES is depreciated. That means while it can still be used for legacy software, it cannot be used to create new cyber-secure applications.
3. Advanced Encryption Standards (AES)
Like DES, Advanced Encryption Standards (AES) is a symmetric encryption algorithm that uses a block cipher to encrypt and decrypt information.
AES differs mainly in its available key sizes. Data can be encrypted using AES with three different key sizes: 128-bit, 192-bit, or 256-bit. These longer bit sizes make it much stronger than DES, as even today’s computers would take an impossibly long time to crack the algorithm. As such, it is used widely and is considered to be one of the most secure encryption methods available today.
AES is used in many common applications, including file encryption, wireless security, processor security, and cloud security protocols such as SSL and TLS.
4. RSA Encryption
Rivest-Shamir-Adleman (RSA) encryption, named after the surnames of its creators, is a type of asymmetric encryption, meaning that you need both a private and public key in order to decrypt the transmitted information.
RSA works by multiplying two very large prime numbers together and relying on the improbability of hackers being able to guess which exact two numbers created the new one.
It also uses extremely large bits to encrypt information, including 1,024-, 2,048-, and sometimes 4,096-bit encryption.
RSA can be applied to different use cases by changing the setup of private and public keys. In the more common configuration, the public key is used for encryption and a private key is required to decrypt the data. This arrangement is commonly to send private information and ensure that it cannot be read if intercepted.
However, RSA encryption can also be used in the reverse arrangement, where the private key encrypts data and the public key decrypts. This method is used to confirm the sender’s authenticity rather than to hide information.
5. Blowfish Encryption
Blowfish encryption is another symmetric-key block cipher algorithm. It was created in the 1990s to replace DES. It can use variable key sizes ranging from 32-bit to 448-bit.
What is distinct about Blowfish is that it is an unpatented algorithm, meaning it can be used by anyone without having to pay for its use. For this reason, it is widely used in software and internet security applications.
Blowfish is slower than some other types of block algorithms, which in some use cases is to its benefit.
6. Twofish Encryption, Threefish Encryption, and More
A demand for increased security has spawned many new encryption algorithms, including Twofish, Threefish, and Macguffin, just to name a few. Each algorithm uses its own unique mathematical formula, and each has its own benefits and drawbacks.
The most important thing is to ensure that the tools you use to encrypt data meet today’s highest standards from the NIST and other regulatory security bodies.
How Is Encryption Used?
Encryption is used every day to protect a variety of data transactions online. You may not even realize some places where it’s used.
Let’s explore the common day-to-day use cases of encryption.
File Encryption
If you’re sending and receiving sensitive information through files such as Word documents, PDFs, or images, file encryption can be used to protect the information contained in those documents.
Using one of the algorithms we discussed in the previous section or another type of encryption method, files can be encoded data in a way that makes them unreadable without a decryption key.
This process provides protection against unauthorized access, theft, and data breaches. There are tools such as Filezilla that allow you to encrypt the documents that you store and send. Making this part of your regular document-sharing process can keep your information much safer.
Disk Encryption
While it’s less common these days, information is sometimes stored and shared on physical devices such as hard drives or USB drives. Ensuring these physical devices have proper cybersecurity procedures implemented in their distribution will help keep the information on them out of the hands of hackers.
Disk encryption uses encryption algorithms to scramble the data on physical storage devices, and only those with the correct secret key can unscramble it. Whereas file encryption is applied to individual files, disk encryption can be applied across the entire disk structure to prevent access to all the files within.
By encrypting your disks, you can protect sensitive data from cyber-attacks or from information falling into the wrong hands.
Email Encryption
A very common and important use of encryption is email encryption.
Email encryption protects the content of your email from being viewed by unauthorized persons. Even if your emails are intercepted by an attacker, encryption can prevent them from being understood by the middleman. Email encryption can also help businesses comply with data protection regulations and maintain the confidentiality of their clients.
When deciding on a secure email provider, you should ensure that the one you choose offers strong encryption capabilities.
Encryption in the Cloud
Cloud security is one of the most important tools in cybersecurity today. Almost everything we do on the web today is stored on servers in the cloud. But when it comes to security, its ease of access is as much of a drawback as it is a benefit.
That’s why cloud encryption is integral to securing data. Encryption in the cloud involves encrypting data before storing it on a cloud server, making it more difficult for hackers or unauthorized users to access it. The encryption keys are typically managed by the cloud provider or the user.
End-to-End Encryption
If you’re using messaging apps today, it’s likely you’re using end-to-end encryption without even realizing it. End-to-end encryption ensures that only the sender and intended recipient can access the content of a text message.
Many popular messaging apps, such as WhatsApp and Signal, use end-to-end encryption to protect their users’ communications.
Encryption has become commonplace in almost all aspects of modern digital life and for good reasons. Let’s explore its main benefits below.
Benefits of Data Encryption
Compliance with Data Protection Regulations
Many organizations and entities are required to be compliant with various data protection standards. Many of these regulations require sensitive data to be stored and transmitted using encryption standards.
One example of this is PCI compliance, which is required by all ecommerce stores. This standard ensures that credit card data is stored and transmitted securely using encryption.
Understanding whether the data you have is properly encrypted or not can save you from fines, lawsuits, or denied insurance claims being found non-compliant. Be sure to check with IT security personnel to ensure you’re meeting the required standards.
Remote Work Protection
While remote work has its many benefits, it can create additional risks when it comes to transmitting sensitive information. With remote work, there’s more information being transmitted over email and instant messaging, all of which are susceptible to interception.
Even though many organizations implement VPNs, firewalls, and other cybersecurity procedures to keep out attackers, the information behind them should still be encrypted in case those protections are breached. Data encryption provides a layer of protection for users working remotely by ensuring that the data is sent in encrypted form and can only be accessed by authorized personnel.
Encryption prevents attackers from capturing network traffic containing sensitive information or exploiting isolated connections over the internet.
Increased Consumer Trust
Using encryption beyond its regulated requirements is also a good idea for many businesses. Being able to promise customers that their data and information will be securely protected with encryption may make them more likely to use your product over another that does not offer similar promises. It shows clients that your company takes data privacy seriously and is committed to protecting its customers.
Furthermore, by using encryption whenever possible, you also reduce the likelihood of being affected by a data or compliance breach. Cyber attacks or compliance violations can cause serious reputational damage to your business and hurt your bottom line.
By using encryption, you can avoid costly and harmful data breaches.
Can Encrypted Data Be Hacked?
Encryption provides strong protection against unauthorized data access, but it is not foolproof. As we’ve explored, some encryption methods are more secure than others. Legacy algorithms are considered less secure because they do not apply enough permutations to avoid being broken by modern-day computers. This problem will increase as computational power continues to increase, and today’s strong encryption could become tomorrow’s weak encryption.
Additionally, there is always a danger that encryption keys can be stolen or lost. Human error plays a role, as encryption keys may be accidentally shared or compromised in other ways.
You should also be aware that encryption also does not categorically protect against every type of cybersecurity risk. Cybercriminals can try to attack your domain from other angles, such as through DDoS attacks, DNS poisoning, phishing, and so on. Therefore, you should harden your security posture with additional tools beyond encryption to ensure your sites and web applications are fully protected.
While these risks do exist, it’s important to remember that cybersecurity is best when layered upon multiple types of security. Encrypted data is still better than unencrypted data, especially if it’s combined with additional types of security procedures to ensure the encryption secrets remain hidden.
Data Encryption FAQs
Encryption is a wide-ranging topic. If you’re interested in diving deeper, here are some commonly asked questions about encryption:
Encryption vs. Tokenization: What’s the Difference?
While encryption is a process that turns intelligible information unintelligible and then back again, tokenization cannot be reversed.
The process of tokenization involves removing key data points from an organization’s data storage and replacing them with placeholder information. Meanwhile, the correct information that was removed is stored elsewhere so as not to be included in the information a hacker may steal if the company is breached.
In Transit vs. At Rest Encryption: What’s the Difference?
The key to understanding the difference between these two types of encryption is understanding the two common states that data can exist in – at rest or in transit.
Data at rest is what we call data that is stored somewhere, on a hard drive, USB, or other digital storage space. This data is in a fixed location, and it doesn’t move. Data in transit is data that is being communicated or transferred. It’s moving between computers, networks, or across the internet. Encryption in transit involves scrambling the information while it’s being moved from one place to another.
Encryption at rest is the process of protecting the data while it is stored at its physical location.
Ensuring your information is encrypted when it is in both states is crucial to protecting the private data of your clients and your company.
What are Encryption Backdoors?
The key to understanding encryption backdoors is to remember that many cybersecurity protocols are built with the knowledge that humans are prone to errors and, on occasion, need a backup plan.
Like the spare house key, you can hide under the mat, encryption backdoors are built-in bypasses that allow authorized personnel to undo the process of encryption in the case of emergencies. However, when not properly protected, these same built-in bypasses can be exploited by attackers and used as backdoors into your encrypted information.
Summary
Encryption is a vital tool in protecting our sensitive information and keeping it safe from cybercriminals. Whether personal data like credit card information or business secrets, encryption ensures that only authorized individuals can access it.
As a website owner, it’s important to understand the different types of encryption, which methods you need to implement to remain in compliance, and how to use them properly to ensure maximum security.
As technology advances, encryption will continue to play a crucial role in safeguarding our data. If you’re curious about how to implement encryption on your web-hosted site, contact us today.