Organizations can now manage access to the MyKinsta dashboard using Security Assertion Markup Language (SAML) protocols, enabling secure single sign-on (SSO) for their team members.
With SAML-based SSO enabled in MyKinsta, companies can grant users access to the dashboard using the same centralized identity provider (IdP) they might be using to mediate access to other enterprise applications.
Those providers might include popular services like Microsoft Entra ID, Okta, OneLogin, Google Workspace, Auth0, Duo, and JumpCloud, but any IdP that supports SAML will work with MyKinsta.
Enabling SAML SSO in My Kinsta
The first step to enabling SAML SSO for your organization’s MyKinsta access is to review our extensive documentation for this new feature. In addition to instructions common to all SAML SSO configurations, we’ve documented configurations for a list of providers that, so far, includes:
It all begins on the MyKinsta side by navigating to username > Company settings > Single sign-on, and clicking Enable:
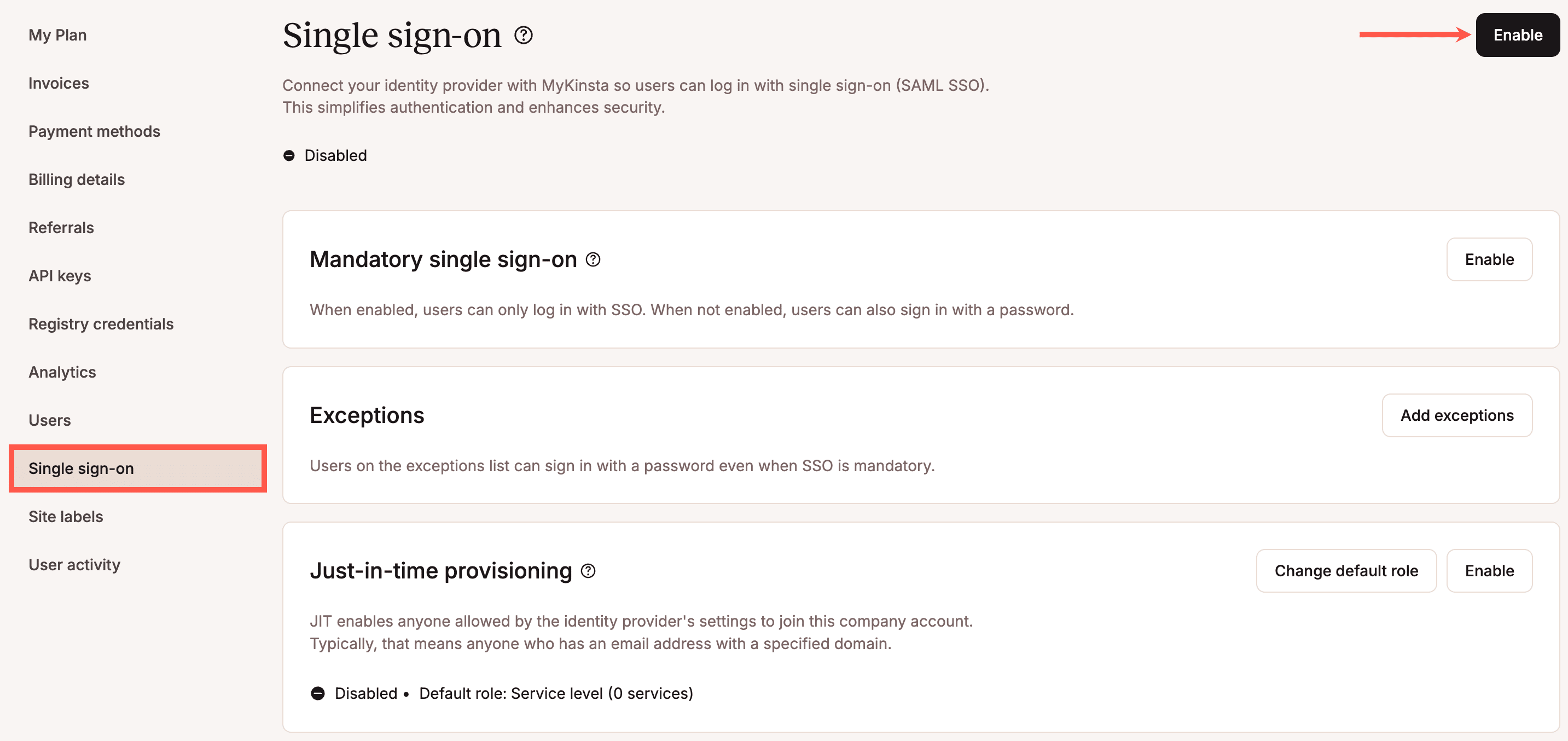
You will be configuring a SAML app in MyKinsta, the particulars of which you will provide to your IdP.
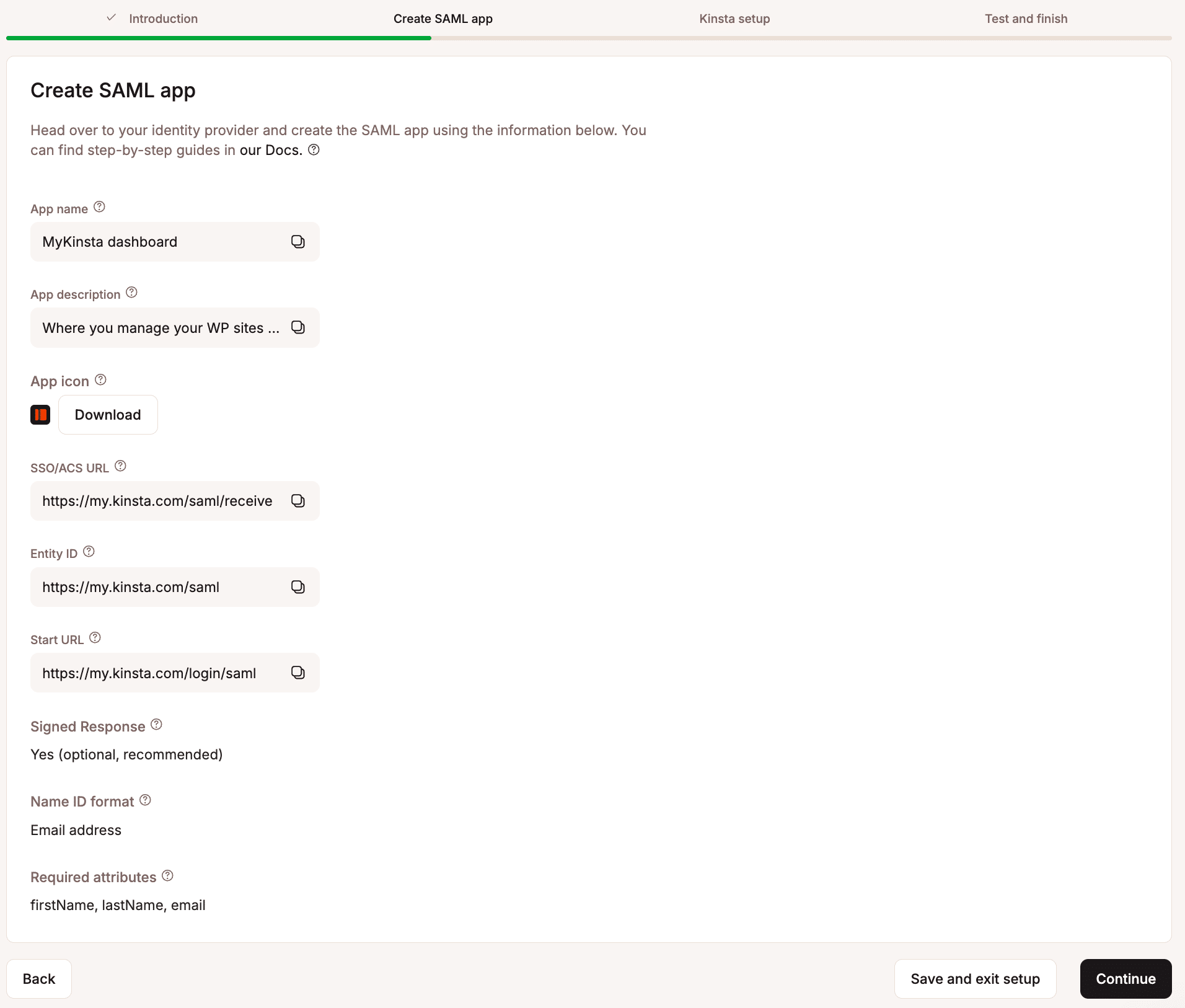
There’s a good chance you will find yourself jumping back and forth between the SAML configuration in MyKinsta and your IdP’s dashboard, so MyKinsta allows you to save your work there as you go.
MyKinsta SSO and your team
Organizations that adopt SAML for SSO typically seek to simplify user access management across multiple applications while also enhancing security. SAML supports the kind of secure authentication many companies demand, while IdP platforms enable centralized user management.
When enabled in MyKinsta, SAML SSO allows organizations to avoid creating multiple user accounts in our dashboard to support their team. Instead, they can grant access to the Kinsta “SAML app” in their IdP platform.
For example, users of the Okta IdP would see something like this within that platform’s dashboard:
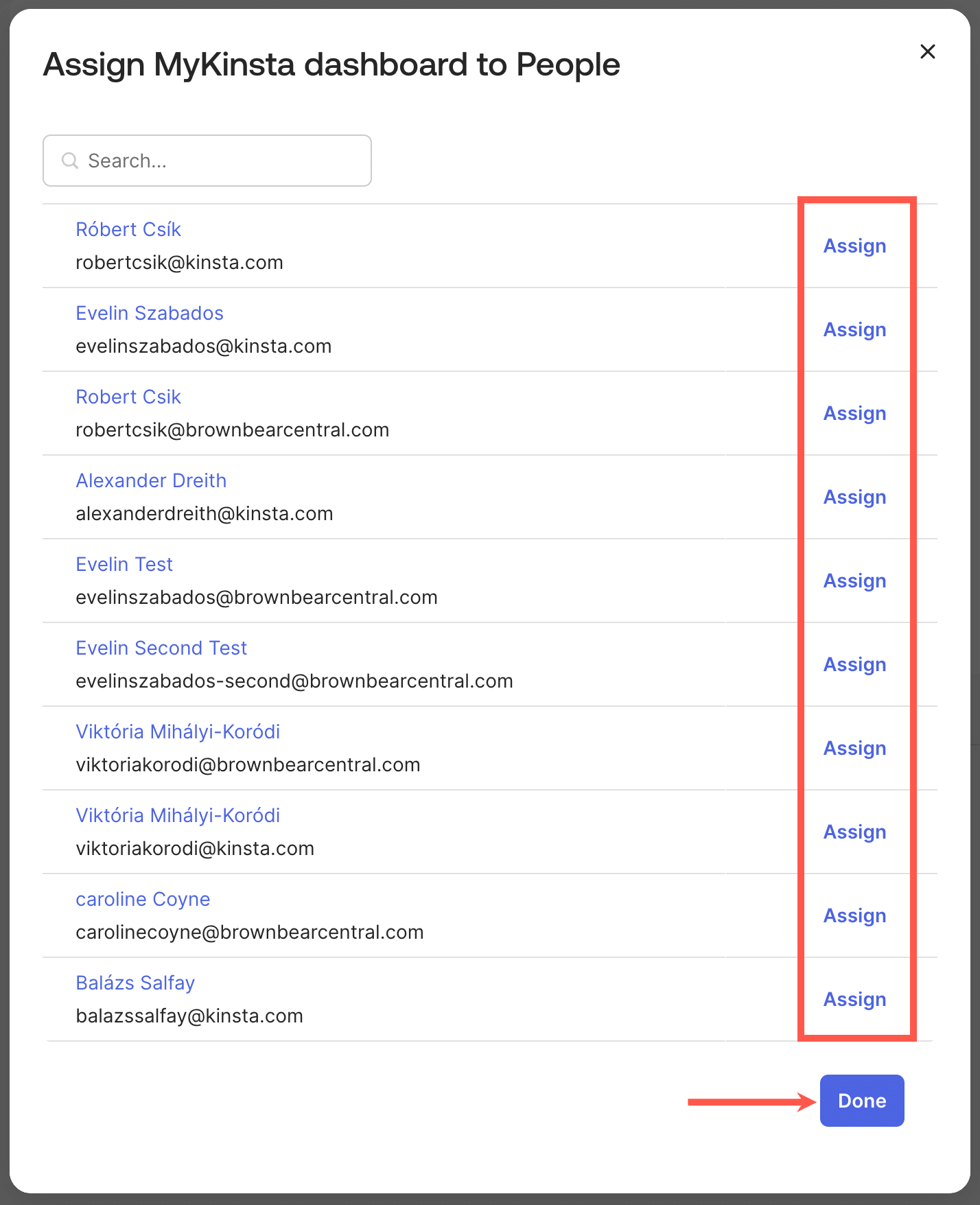
Users who sign in to MyKinsta using SAML SSO are not required to complete Kinsta’s two-factor authentication (2FA) steps, since authentication is handled directly by the IdP (which may use multi-factor authentication itself).
Just-in-time provisioning of SSO
Kinsta supports Just-in-time (JIT) provisioning of SSO in MyKinsta, usually enabling any user authorized by your IdP to log in to the dashboard without an invitation. This allows your team to manage access requirements entirely within your IdP’s platform.
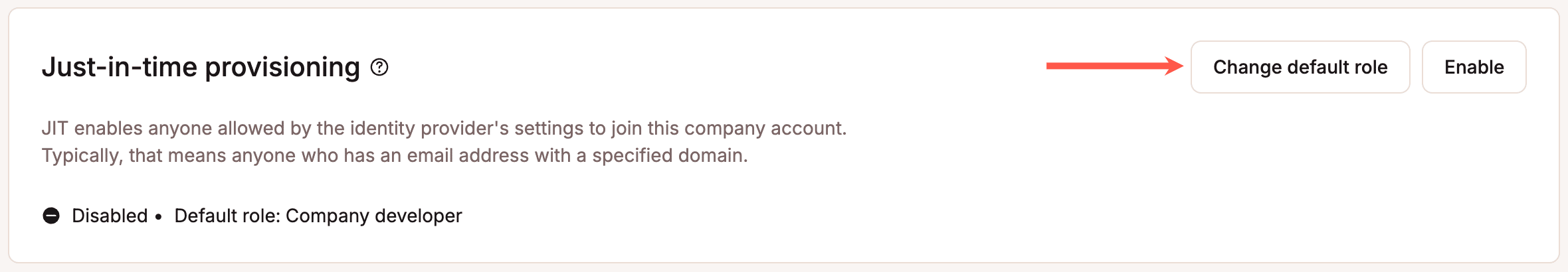
By default, users provisioned through JIT are assigned the Company Developer role in MyKinsta. You can edit a user’s access level in MyKinsta after they join, or update the default role for JiT for newly provisioned users.
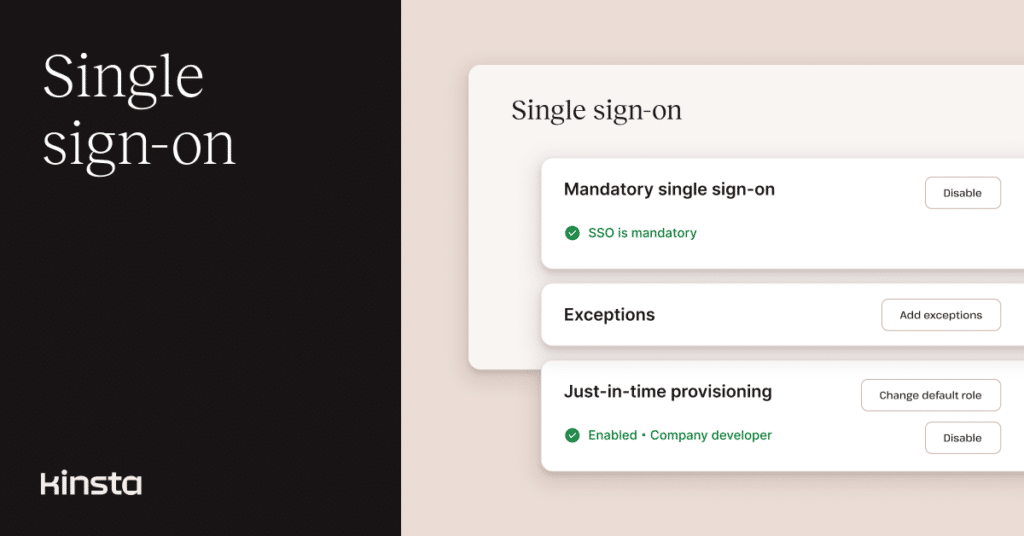
Mandatory SSO and exceptions
A key feature of SAML SSO in MyKinsta is the ability to make such authentication mandatory:
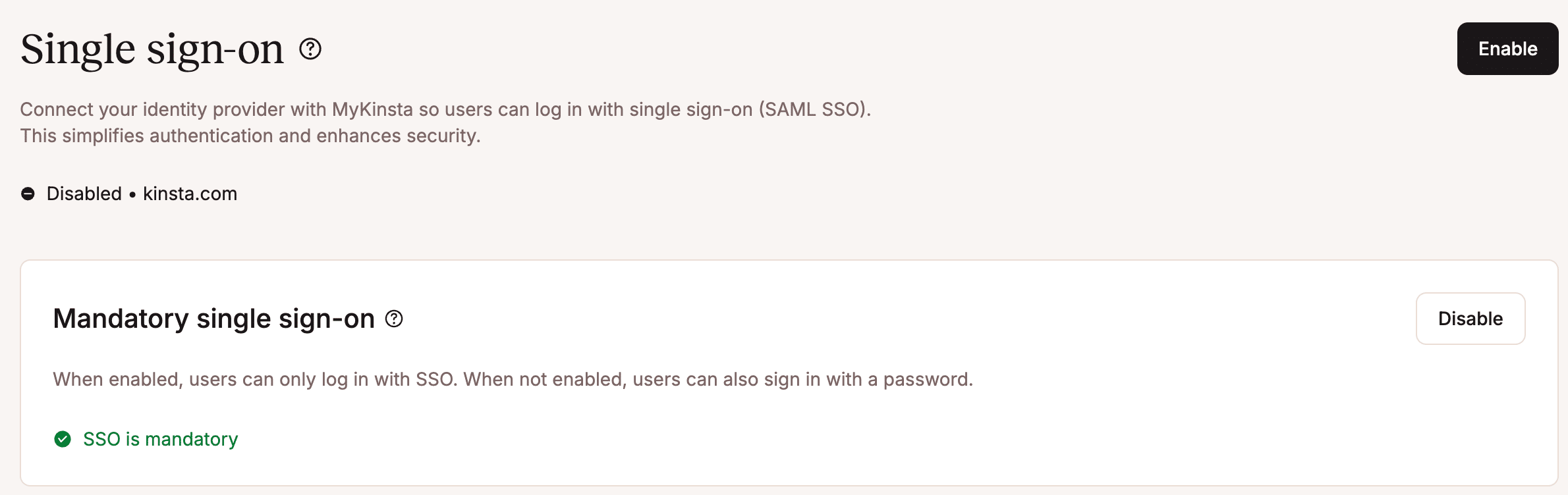
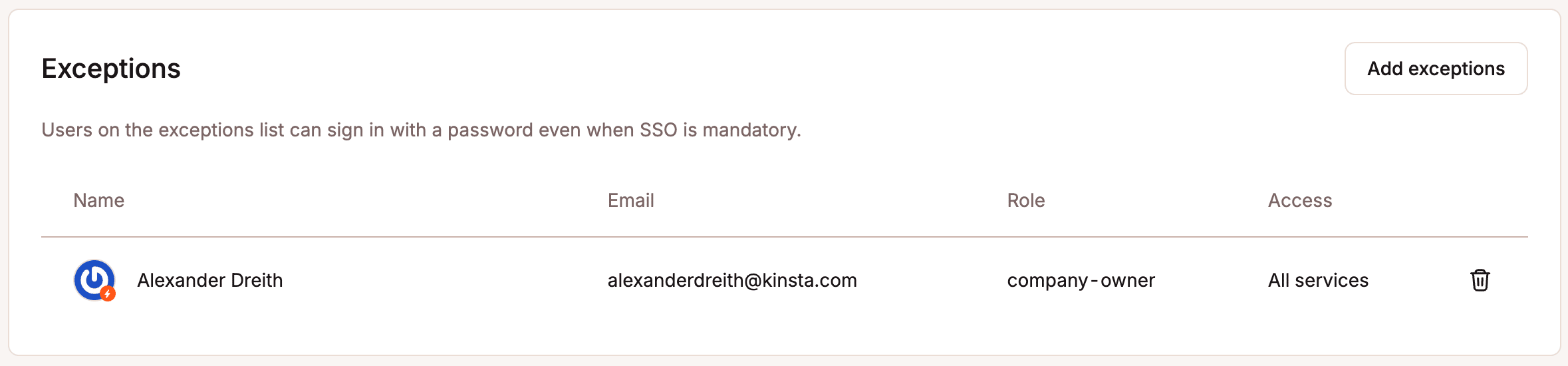
When SSO is declared mandatory, organizations can create exceptions to that rule, allowing some users to log in with their MyKinsta passwords. This feature is particularly useful when dashboard access is granted to a user whose account is not managed in a SAML-based IdP.
Secure WordPress management for organizations
The addition of SAML-based SSO is the latest enhancement to MyKinsta, supporting the security requirements of teams like yours.
Security is built into every part of the Kinsta platform. From ISO 27001 certification and SOC 2 compliance to built-in firewalling, DDoS protection, and wildcard SSL, we’re committed to keeping customer data safe.