If there’s one thing Hollywood movies teach us, it’s that hackers are clever and have various tricks to bypass our security. In the real world, a security issue often comes down to opportunity rather than developed skill. A “DNS poisoning” attack fits this description, and in fact, you need to have the skills to keep your domain from being spoofed.
The concept is simple: visitors see what looks like your website, but it’s fraudulent and harmful, while this fake website looks similar. As such, you need to employ several techniques to make sure users are safe, and your site remains free from attacks.
In this post, we’re going to dive into the concept of DNS poisoning and domain spoofing. We’re also going to talk about some of the surrounding concepts to help you understand why your eventual response is the best approach.
A Primer On the Domain Name System (DNS)
Before we get into the specifics of DNS poisoning, let’s chat about the Domain Name System. While browsing a website appears a straightforward task, a lot is going on under the server’s hood.
There are lots of elements involved to get you from ‘A’ to ‘B’:
- IP Address. It’s a string of numbers that is your actual web address. Consider them the coordinates of your house. For example, 127.0.0.1:8080 is a standard “localhost” address (i.e. your computer).
- Domain name. If the IP address represents coordinates, the domain name is your address as it appears on the envelope. Of course, “kinsta.com” is one of the millions of examples.
- A DNS request. It’s an excellent example of a high-level frontend task with a complex low-level process. For now, consider a request to be your browser asking a dedicated server what the address is for a set of coordinates.
- A DNS server. This is different from your website’s server in that it’s four servers in one. Its job is to process DNS requests. We’ll talk about this in a little more detail in later sections.
- Recursive server. You’ll also see these servers called “resolving name servers.” It’s part of the DNS lookup process and is responsible for querying servers for the domain name relating to an IP address.
On the whole, a DNS makes fetching a domain name simple for the end-user. It’s a core part of the web, and as such, it has many moving parts.
We will look at the lookup process itself next, although you can already see how the DNS has a vital job to fulfill.
The Process of a DNS Lookup
Bear with us here while we offer what looks like an abstract analogy.
Activities that take people into remote places, such as mountaineering or sailing, share one specific danger: getting lost and not being found in time. The traditional way of locating stranded people has been to use coordinates. They’re explicit and offer pinpoint accuracy.
However, this process has drawbacks. First, you need to know how to calculate your coordinates for any location — tricky if in a remote part of the world. Second, you have to articulate those coordinates to the rescue team. One wrong number and the consequences are dire.
The what3words app takes the complex process of calculating and passing on coordinates and turns it into a three-word summary of your general location. For example, take Automattic’s headquarters:
The coordinates of the location are 37.744159, -122.421555. Unless you’re an expert navigator, though, you’re not likely to know this. Even if you did, getting this in the hands of someone who could help you is a slim proposition.
In a nutshell, what3words takes an abstract set of coordinates and translates them into three memorable words. In the case of Automattic’s offices, it’s decent.transfers.sleeps:
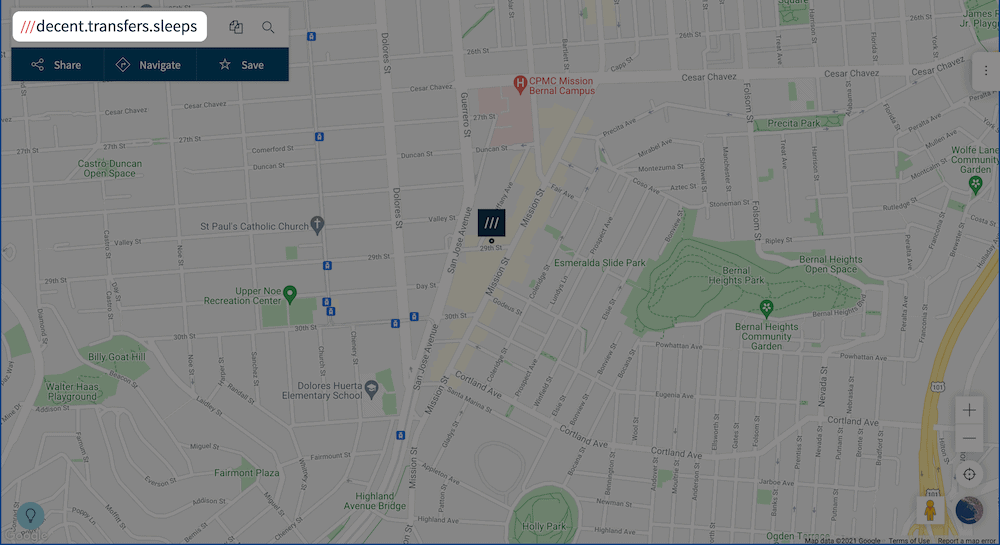
This puts complex global positioning in the hands of almost anyone with access to the app. It’s saved a lot of civilian lives already.
This ties in with a DNS lookup because the process is similar. In the case of what3words, the rescuer asks the app for the coordinates of a word string. The request is sent across servers to look for the coordinates and return to the end-user when they’re found.
A DNS lookup has a similar flow:
- Your browser requests the IP address for a domain name.
- Your operating system (OS) asks the recursive server to find the domain name and begins a run through its collection of servers.
- When it finds the domain name, it’s returned to the browser.
One of the drawbacks of what3words is how a word string isn’t as accurate as a set of coordinates. This means you can pinpoint a general location fast but may spend longer finding the stranded person.
A DNS lookup has drawbacks as well, and malicious attackers can exploit them. Before we look at this, though, let’s take a brief detour to talk about caching and how this can speed up a lookup.
DNS Caching
Much like web caching, DNS caching can help you recall regular queries to the server. This will make the process of fetching an IP address faster for each new visit.
In short, the cache is located within the DNS server system and cuts out the extra trip to the recursive server. This means a browser can fetch an IP address straight from the DNS server and complete the GET request in a quicker time.
You’ll find DNS caches throughout your entire system. For example, your computer will have a DNS cache, as will your router and internet service provider (ISP). You often don’t realize how much your browsing experience relies on DNS caching — until you’re a victim of DNS poisoning, that is.
What DNS Poisoning Is
Now that you understand the concept of a DNS lookup and the entire process of fetching an IP address, we can see how it can be exploited.
You’ll often see DNS poisoning referred to as “spoofing” too because having a fraudulent “lookalike” website in the chain is part of the attack.
We’re going to talk in more detail about all of these aspects, but know that DNS poisoning or spoofing is a harmful attack that can cause mental, monetary, and resource-related problems for users and the internet.
First, though, let’s get into the process of cache poisoning.
How DNS Spoofing and Cache Poisoning Works
Given that the whole spoofing process is complex, attackers have created many different ways to achieve their goal:
- Machine-in-the-Middle. This is where an attacker gets between the browser and DNS server, poisons both, and redirects a user to a fraudulent site on their own server.
- Server hijacking. If an attacker gets into the DNS server, they can reconfigure it to send all requests to their own site.
- Poisoning through spam. In contrast to a server hijack, this approach poisons the client-side (i.e. the browser). Access is often granted through spam links, emails, and fraudulent ads.
- “Birthday attacks.” This is a complex cryptographic attack that takes some further explanation.
A birthday attack is based on the “birthday problem.” This is a probability scenario that says (in a nutshell) if there are 23 people in a room, there’s a 50% chance of two sharing the same birthday. If there are more people in the room, the chances rise.
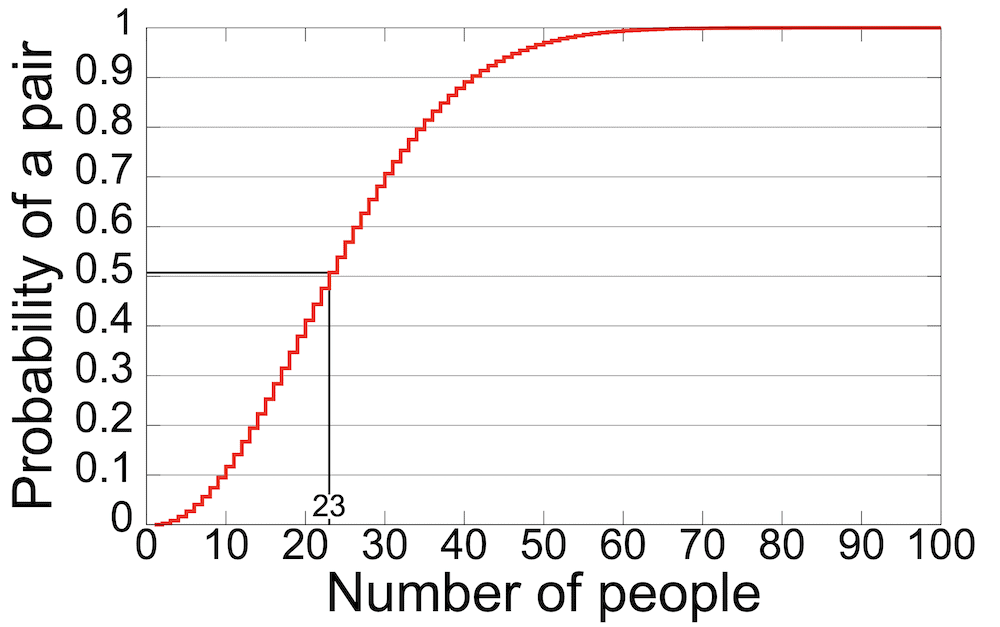
This translates to DNS poisoning based on the identifier that connects the DNS lookup request to the GET response. If the attacker sends a certain number of random requests and responses, there’s a high probability of a match resulting in a successful poisoning attempt. From around 450 requests, the probability is about 75%, and at 700 requests, an attacker is almost guaranteed to crack the server.
In short, attacks to the DNS server happen in most cases because this gives a malicious user greater flexibility to manipulate your site and user data. There’s also no verification for DNS data because requests and responses don’t use Transmission Control Protocol (TCP).
The weak point in the chain is the DNS cache because this acts as a repository for DNS entries. If an attacker can inject forged entries into the cache, every user who accesses it will find themselves at a fraudulent site until the cache expires.
Attackers will often look for a few signals, weak points, and data points to target. They work to spot DNS queries that haven’t been cached yet because the recursive server will have to undertake the query at some point. By extension, an attacker will also look for the nameserver a query will go to. Once they have this, the port the resolver uses and the request ID number are vital.
While meeting all of these requirements isn’t necessary — after all, an attacker can access servers through numerous methods — ticking these boxes off makes their job easier.
Real-World Examples of DNS Poisoning
There have been a few high-profile examples over the years of DNS poisoning. In some cases, it’s an intentional act. For instance, China operates a firewall on a massive scale (the so-called “Great Firewall of China”) to control the information internet users receive.
In a nutshell, they poison their own servers by redirecting visitors heading to state-unsanctioned sites such as Twitter and Facebook. In one case, Chinese restrictions even made their way into the Western world’s ecosystem.
A networking error from a Swedish ISP served root DNS information from Chinese servers. This meant users in Chile and the US were redirected elsewhere when accessing some social media sites.
In another example, Bangladeshi hackers protesting mistreatment in Malaysia poisoned many domains relating to Microsoft, Google, YouTube, and other high-profile sites. This appears to have been a case of server hijacking rather than a client-side issue or spam.
Even WikiLeaks isn’t immune to DNS poisoning attacks. A potential server hijack a few years ago caused visitors to the website to be redirected to a page dedicated to the hackers.
DNS poisoning doesn’t have to be a complicated process. So-called “ethical hackers” — i.e. those who look to expose security flaws rather than inflict damage — have straightforward methods for testing spoofing on their own computers.
Other than being redirected, though, there may not seem to be any long-term effects of DNS poisoning on the surface. In fact, there are — and we’ll talk about them next.
Why DNS Poisoning and Spoofing Is So Harmful
There are three main goals of an attacker hoping to perform DNS poisoning on a server:
- To spread malware.
- Reroute you to another website that will benefit them in some way.
- Steal information, either from you or another entity.
Of course, it does not leap the imagination to understand why DNS poisoning or spoofing is a problem for ISPs, server operators, and end-users.
As we noted, spoofing is a massive problem for ISPs, so much so that there are tools like the CAIDA Spoofer available to help.
A few years ago, statistics showed that there were around 30,000 attacks a day. This number will almost certainly have increased since the report was published. What’s more, as was the case with the example in the previous section, delivering spoofed sites across a network brings user trust issues to the fore, along with privacy concerns.
Regardless of who you are, there are a few risks involved when you’re the victim of poisoning and spoofing:
- As with the Great Firewall of China, you could be subject to censorship. This means the information you get won’t be accurate, which has a knock-on effect on many social and political arenas.
- Data theft is a top concern, and it’s a lucrative venture for those who want to obtain user banking information and other sensitive data.
- You could be susceptible to different types of malware and other Trojan viruses on your system. For example, an attacker could inject a keylogger or other forms of spyware on your system through a spoofed site.
There are other related effects of DNS poisoning too. For instance, you may not be able to apply any security updates to your system while the recovery process is in full swing. This leaves your computer vulnerable for longer.
Also, consider the cost and complexity of this cleanup process, as it will affect everyone along the chain. Higher prices for all of the connected services is just one of the negatives.
The effort of eliminating DNS poisoning is immense. Given that spoofing affects both client- and server-side setups, ridding it from one doesn’t mean it’s gone from all.
How To Prevent DNS Poisoning
There are two areas affected by DNS poisoning — client-side and server-side. We’re going to take a look at what you can do to prevent this damaging attack on both sides of the coin.
Let’s begin with what the internet as a whole is doing on the server-side.
How the Internet Tries to Prevent DNS Poisoning and Spoofing Server-Side
Although we’ve talked a lot about DNS throughout this article, we haven’t noted how antiquated the technology is. In short, DNS isn’t the best fit for a modern web browsing experience due to a few factors. For starters, it’s unencrypted, and without some vital validation considerations, that would stop a lot of DNS poisoning attacks from continuing.
One quick way to prevent attacks from becoming stronger is through a simple logging strategy. This carries out a straightforward comparison between the request and the response to see if they match.
However, the long-term answer (according to the experts) is by using Domain Name System Security Extensions (DNSSEC). This is a technology designed to combat DNS poisoning, and in simple terms, it puts different levels of verification in place.
Going deeper, DNSSEC uses “public-key cryptography” as verification. This is a way of signing off on the data as genuine and trustworthy. It’s stored alongside your other DNS information, and the recursive server uses it to check that none of the information it receives has been altered.
Compared to other internet protocols and technologies, DNSSEC is a relative baby — but it’s mature enough that it’s implemented in the root level of the internet, though it’s not yet mainstream. Google’s Public DNS is one service that supports DNSSEC in full, with more popping up all the time.
Even so, there are still some drawbacks with DNSSEC that are worth noting:
- The protocol doesn’t encode responses. This means attackers can still ‘listen in’ on traffic, although the attacks will have to be more sophisticated to bypass DNSSEC.
- Because DNSSEC uses extra records to gather DNS data, there’s another vulnerability called “zone enumeration.” This uses one record to “walk through” and collect all DNS records within a specific “zone.” Some versions of this record encrypt the data, but others don’t yet.
- DNSSEC is a complex protocol, and because it’s also new, it can sometimes be misconfigured. Of course, this can erode the benefits of using it and present further problems down the line.
Even so, DNSSEC is the future on the server-side, at least. As for you as the end-user, there’re also some preventative measures you can take.
How You Can Prevent DNS Poisoning on the Client-Side
There are more ways to prevent DNS poisoning on the client-side, although none on their own will be as robust as server-side DNSSEC implemented by an expert. Still, there are some simple boxes you can check off as a site owner:
- Use end-to-end encryption for any requests and replies. Secure Sockets Layers (SSL) Certificates do a good job here.
- Employ spoofing detection tools. These can scan received data packets before sending them out. This mitigates any malicious data transfers.
- Increasing the Time-To-Live (TTL) values for your DNS cache will help flush malicious entries before they can reach end-users.
- You should have a good DNS, DHCP, and IPAM (DDI) strategy in place. This consists of your DNS strategy, Dynamic Host Configuration Protocol, and IP Address Management. It’s a complex yet necessary process handled by sysadmins and server security experts.
As an end-user, there are a few more things you can do to help prevent poisoning and spoofing:
- Use a Virtual Private Network (VPN), as your data will be encrypted end to end. You’ll also get use of private DNS servers, again with end-to-end encryption.
- Take simple precautions, such as not clicking unrecognized links and carrying out regular security scans.
- Flushing your DNS cache regularly also clears malicious data out of your system. It’s something that takes seconds and is simple to carry out.
While you can’t rid DNS poisoning in total, you can prevent the very worst from happening. As an end-user, you don’t have much control over how the server handles attacks. Likewise, sysadmins don’t get to control what happens in the browser. As such, it’s a team effort to stop this most harmful of attacks from affecting the entire chain.
Summary
Internet attacks are commonplace. DNS poisoning (or spoofing) is a common attack that can affect millions of users if left unchecked. This is because the DNS protocol is old and unsuited for modern web browsing — although newer technologies are on the horizon.
In short, DNS poisoning redirects an end-user to a fraudulent version of an existing website. It’s a way to steal data and infect systems with malware. There’s no foolproof way to prevent it altogether, but you can contain it through some simple measures.
Have you ever been a victim of DNS poisoning or spoofing, and if so, what was the cause? Please share your experience with us in the comments section below!


