If you regularly follow WordPress newsletters or cybersecurity updates, you’ve probably noticed a familiar pattern: almost every week, there’s a new report about a WordPress plugin vulnerability. Why is this happening so often?
One reason for these vulnerabilities is that plugin development in the WordPress ecosystem is vast and involves many developers who aren’t directly affiliated with WordPress itself. While WordPress provides clear guidelines to ensure security, the sheer scale and complexity of the ecosystem — with thousands of plugins and themes working together — can sometimes make it difficult to catch every potential flaw.
What’s more, developers sometimes rush to release updates or new features, and even well-meaning coders might unintentionally overlook security concerns, allowing hackers to exploit vulnerabilities.
Once a vulnerability is discovered, hackers can use various technical exploits to compromise your site. Common methods include cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF). These exploits allow hackers to perform a range of malicious activities, such as:
- Redirecting visitors to malicious sites.
- Injecting spam ads and unwanted content into your site.
- Installing malware (e.g., infecting files like
wp-feed.php) to execute further attacks. - Creating rogue admin accounts to take control of your site.
- Using your server to launch DDoS attacks or send spam emails.
These attacks can cripple your site’s performance, bring down your SEO rankings, and, most importantly, damage your business, revenue, and reputation.
However, it’s important to note that plugin vulnerabilities themselves are not the only problem. A major reason these attacks succeed is that many WordPress users fail to update their plugins. This article explores why these vulnerabilities are on the rise and what you can do to protect your site.
The real cause of most WordPress hacks
When WordPress sites get hacked, we are quick to blame either the hosting provider or the plugins that supposedly opened the door to attackers. It’s true that plugin vulnerabilities play a significant role. According to SolidWP’s 2022 WordPress vulnerability report, 93% of WordPress vulnerabilities came from plugins. However, the underlying issue is often user negligence.
Most hacks occur not because the platform or plugins are inherently insecure, but because users fail to either update their plugins in a timely manner or because some plugins are abandoned.
To better understand how these vulnerabilities expose your site, let’s take a closer look at the two major factors:
Outdated plugins
When a security flaw is discovered in a plugin, the developers are notified and typically work quickly to create a patch. Once the patch is ready, it’s released as an update, and a vulnerability disclosure is sent out, alerting users to apply the update.
However, there’s often a delay between the disclosure and when users actually update their plugins. Hackers capitalize on this gap, scanning the web for sites that haven’t yet patched the vulnerability.
A striking example of this was the File Manager plugin vulnerability discovered in September 2020, which affected over 600,000 WordPress sites. This zero-day remote code execution vulnerability allowed attackers to access the admin area, run malicious code, and upload harmful scripts on sites running older versions of the plugin (versions 6.0 to 6.8). While the developers released a patched version (File Manager 6.9) within hours, over 300,000 sites remained vulnerable because users hadn’t updated their plugins, and hackers quickly exploited this delay.
This example shows how dangerous a simple delay in applying updates can be, making it clear that user negligence in updating plugins is a major cause of WordPress hacks.
Abandoned plugins
Abandoned plugins are a ticking time bomb for many WordPress sites. Although the WordPress team permanently removes some of these plugins from its repository, many remain active on websites without ongoing maintenance or security updates.
In 2023 alone, 827 plugins and themes were reported as abandoned — significantly up from 147 in 2022. Of these, more than half (58.16%) were permanently removed due to serious security concerns.
For example, the Eval PHP plugin was abandoned for over a decade before hackers began exploiting it in 2023. The plugin, which was originally designed to let users execute PHP code within WordPress posts and pages, became a tool for attackers to inject backdoors into websites. Because Eval PHP was no longer maintained, the security vulnerabilities remained unpatched, and hackers took advantage of this, using the plugin to gain unauthorized access to websites.
Once inside, attackers could steal sensitive information, take full control of a site, or use it as part of larger malicious campaigns, like DDoS attacks. Even removing the plugin didn’t necessarily resolve the issue — hackers could persist on compromised websites by hiding backdoors in the site’s content.
This highlights the dangers of using abandoned plugins. When a plugin is no longer maintained, its vulnerabilities become permanent entry points for hackers. Website owners must be proactive in removing such plugins and replacing them with supported alternatives to keep their sites secure.
How to protect your WordPress site
Given the growing number of plugin vulnerabilities and the risks posed by outdated and abandoned plugins, it’s essential to take proactive measures to secure your WordPress site. Here are some practical steps you can follow to minimize risks and keep your site safe:
1. Use a quality hosting provider
Your hosting provider can play a crucial role in the security of your WordPress site by offering security measures to prevent common attacks. For instance, Kinsta emails vulnerability alerts to customer inboxes whenever vulnerabilities are reported for plugins installed on their sites.
Many people set up WordPress sites and forget about them, or they rely on agencies managing hundreds of sites at once. It’s easy to lose track of security updates. This is exactly why having a host that’s actively looking out for vulnerabilities is so important.
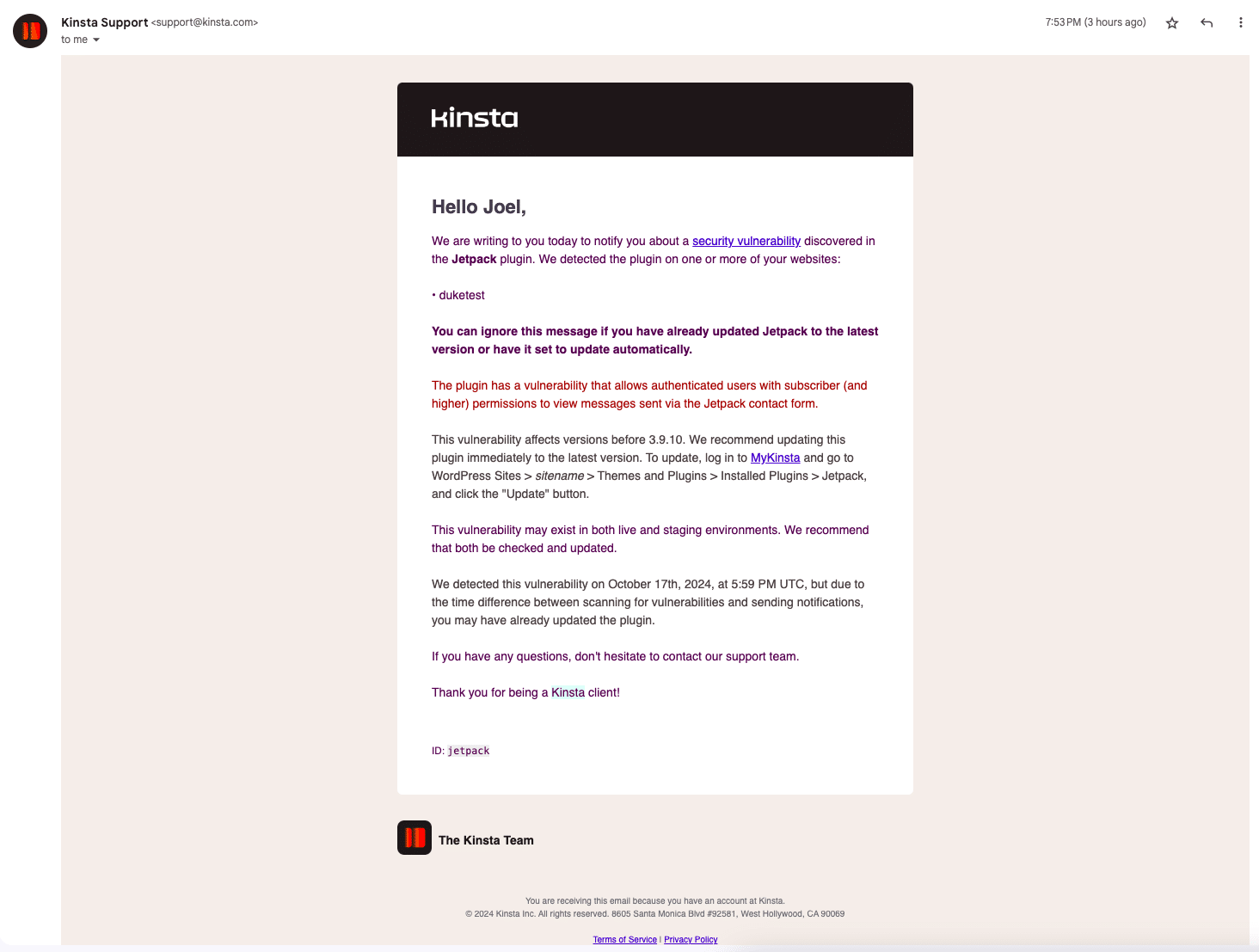
Take the Jetpack plugin example, which made headlines recently. Its developers released an update that fixed a critical vulnerability affecting 27 million sites — one that had gone unnoticed since 2016!
The flaw allowed any logged-in user to view other users’ form submissions. Jetpack’s team confirmed there was no evidence of it being exploited, but once the update was out, they warned that someone might try to take advantage of unpatched sites.
At Kinsta, we immediately rolled out a vulnerability report to all our customers using Jetpack, urging them to update and explaining why it was necessary. This is the kind of proactive support you need from a quality host.
Other ways a good host can protect your site include:
- Malware detection and cleanup — Your host should regularly scan for malware to ensure the safety of your site. At Kinsta, we conduct periodic malware scans within customer containers to detect most known malicious fingerprints. If any malware is detected, our abuse team will promptly clean it up and notify you.If your site has already suffered an attack and you are unaware, our scanning process is designed to identify compromises. As part of our commitment to your security, we have a security pledge: if your site gets hacked while hosted with us, we’ll help fix it for free. Check out our malware removal process for more details.
- Firewall and security monitoring — A firewall protects your site against malicious traffic. It blocks bad actors before they can even reach your plugins. Without this, hackers can easily target vulnerabilities in outdated plugins. At Kinsta, we offer firewall technology that assists in protecting our network against common threats, while our Cloudflare integration provides DDoS protection to keep our infrastructure safe.
Additionally, ensure your site has daily automatic backups in place so that if it is compromised, you can quickly restore it to a previous version, minimizing downtime and preventing data loss.
2. Keep plugins updated
One of the simplest and most effective ways to protect your WordPress site is to ensure that all plugins, themes, and the WordPress core are up to date. Most updates include security patches that address known vulnerabilities, and failing to apply these updates exposes your site.
To ensure your plugins are always up to date, follow these steps:
- Regularly check your WordPress dashboard for plugin updates.
- Consider setting up an automated process to handle updates and trigger alerts for essential plugins when they are outdated. Our customers can take advantage of the Kinsta Automatic Updates add-on to manage plugins (and themes). They can rely on the add-on’s built-in visual regression testing to detect failures during plugin updates and roll back installations to the most recent functioning configurations. Kinsta also offers an API that exposes endpoints customers can use to build tools for automating the plugin update process. The MyKinsta dashboard also includes a bulk update feature that allows customers to manually launch plugin updates across multiple sites with just a few clicks.
- Set a schedule to review and update plugins that don’t auto-update.
3. Remove abandoned or unsupported plugins
Abandoned plugins are one of the biggest security risks to WordPress sites. If a plugin is no longer maintained by its developer, it won’t receive critical security updates, leaving it vulnerable to exploitation.
To protect your site, make sure to:
- Regularly audit your installed plugins and remove any that haven’t been updated in a long time.
- Look for actively maintained alternatives to replace outdated or unsupported plugins.
- Check the WordPress plugin repository to confirm the plugin’s last update date and the developer’s activity.
4. Use only trusted plugins
Not all plugins and themes are equally secure. Installing plugins from unverified sources can expose your site to malicious code or poorly written software.
To minimize risk, make sure to:
- Stick to plugins and themes available from the WordPress plugin repository or well-known developers with a proven track record.
- Always check reviews, ratings, and the number of active installations before installing a plugin.
- Prioritize plugins that are regularly updated and supported by their developers.
- Avoid plugins with a history of security vulnerabilities or poor security practices.
5. Limit the number of plugins you install
Each plugin you install on your site introduces potential vulnerabilities, so it’s important to limit the number of plugins you use. By choosing a quality hosting provider like Kinsta, you can avoid installing unnecessary plugins for tasks already built into your hosting environment.
For example, Kinsta users don’t need to install separate plugins for:
- Backups — Kinsta provides automatic daily backups, eliminating the need for a backup plugin.
- Malware scanning — Kinsta offers built-in malware scanning, so there’s no need for an additional security plugin.
- CDN integration — With Kinsta’s built-in Cloudflare integration, you can avoid installing a CDN plugin.
- Vulnerability protection — Kinsta proactively monitors for security vulnerabilities and takes action, so no vulnerability attack plugins are needed.
By using fewer plugins, you reduce your attack surface and minimize the risk of plugin-related vulnerabilities while maintaining better site performance.
6. Limit admin access and enable strong authentication
Limiting access to your WordPress admin area reduces the risk of unauthorized access. Using strong passwords and enabling two-factor authentication (2FA) further strengthens your site’s security. Here’s how you can do it:
- Ensure only trusted users have admin-level access to your WordPress site.
- Use strong, unique passwords and require this from all users with access to your admin area.
- Enable 2FA to add an extra layer of protection to brute-force login attempts, making it harder for attackers to break in.
- Limit login access to specific IP addresses, IP ranges, or geographic locations. For example, if you run a WooCommerce store that only sells to customers in the U.S., you can restrict account creation and login access to U.S. users only. This helps reduce your site’s exposure to attacks.
7. Monitor vulnerability reports
Staying informed about security issues with your plugins and themes helps you act quickly before hackers can exploit vulnerabilities. To stay on top of potential threats, make sure to:
- Subscribe to security reports or services like WPScan, Wordfence, or iThemes Security for real-time vulnerability alerts.
- Regularly check for vulnerability updates related to the plugins on your site.
- Take immediate action if your installed plugins or themes are flagged as vulnerable.
Summary
Securing your site requires ongoing vigilance. Outdated and abandoned plugins are two of the most common gateways for hackers, but the good news is that these risks are manageable with the right hosting.
At Kinsta, we are committed to ensuring your WordPress site remains secure. Our hosting platform offers a range of built-in security features to protect your site from threats, including proactive vulnerability reports, free SSL certificates, two powerful firewalls, and Cloudflare integration for enhanced protection against DDoS attacks and other vulnerabilities.
To learn more about how Kinsta’s security features can help you, talk to our sales team today!


