Your computer has two addresses on the Internet: a permanent physical address or Media Access Control (MAC) address and a logical Internet Protocol or IP address. But with many computers changing IP addresses all the time, how can networks associate various IPs to a single MAC address?
Enter ARP, formally known as Address Resolution Protocol.
ARP’s job is to translate between a computer’s MAC address and IP address(es) — a pretty useful function for any network. Despite its usefulness, however, ARP can also present several security risks, including those that can intercept potentially sensitive data.
But how does it all work?
In this article, we’ll define ARP, contrast it with similar networking protocols, explore its various types and use cases, and the risks of using it in your network. Read on to learn more about this common — and sometimes risky — network protocol.
Check Out Our Video Guide On ARP:
What Is ARP?
Address Resolution Protocol or ARP is a common way for networks to translate between (or resolve) a computer’s IP address to its physical machine address.
Since these two addresses differ in length and format, ARP is essential for allowing computers and other devices to communicate over a network. To truly understand why this is important, however, let’s have a quick refresher on these two address types and how they relate to our daily networking models.
IP vs MAC Addresses
Your computer, smartphone, and other connected devices have two addresses on the Internet: an IP address and a MAC address.
But why have two separate addresses for one device?
Imagine for a moment that your computer is a mobile home. When the mobile home comes off the manufacturing line, it might have a serial number (or some other unique identifier) that separates it from all the other mobile homes. In other words, the mobile home can be identified by its serial number.
Now let’s say you park the mobile home in your neighborhood. Depending on which lot you parked it, the mobile home will be given a street address — let’s say “27 Kinsta Lane.” If your mobile home is parked in that same lot, its street address will remain 27 Kinsta Lane. However, you could just as easily move it down the road to give it a new street address, such as “93 Kinsta Lane.”
Notice here that parking your mobile home gives it two forms of identification: its serial number and street address. Here, the street address tells everyone where the mobile home is located relative to the rest of the world, while the serial number tells the mobile home apart from other mobile homes that might be on the same lot.
Your computer’s IP and MAC addresses serve exactly the same purposes, only that the neighborhood from our example is now a local network.
Here, your computer’s MAC address is its unique physical identifier on a network — very much like how your mobile home’s serial number was its unique physical identifier. To this end, the MAC address is often known as a physical address or hardware address. Also like a serial number, you can’t change your computer’s MAC address.
Meanwhile, your computer’s IP address is its “street address” on the network. When a computer connects to a network, it’s assigned an IP address just like a mobile home is assigned a street address once it’s parked in a lot.
However, if the computer disconnects from the network, it loses the IP address, just like removing a mobile home from a lot will disassociate it from its street address. Reconnecting to the network is also the same as parking the mobile home somewhere else, where the computer will be given a new IP address, just as the mobile home would be given a new street address.
Of course, IP and MAC addresses are still very different from street addresses and serial numbers.
Where a postal worker can deliver mail to a mobile home without knowing its serial number, the Internet equivalent — the Internet Protocol or IP — needs both addresses to deliver mail or packets to the right computer.
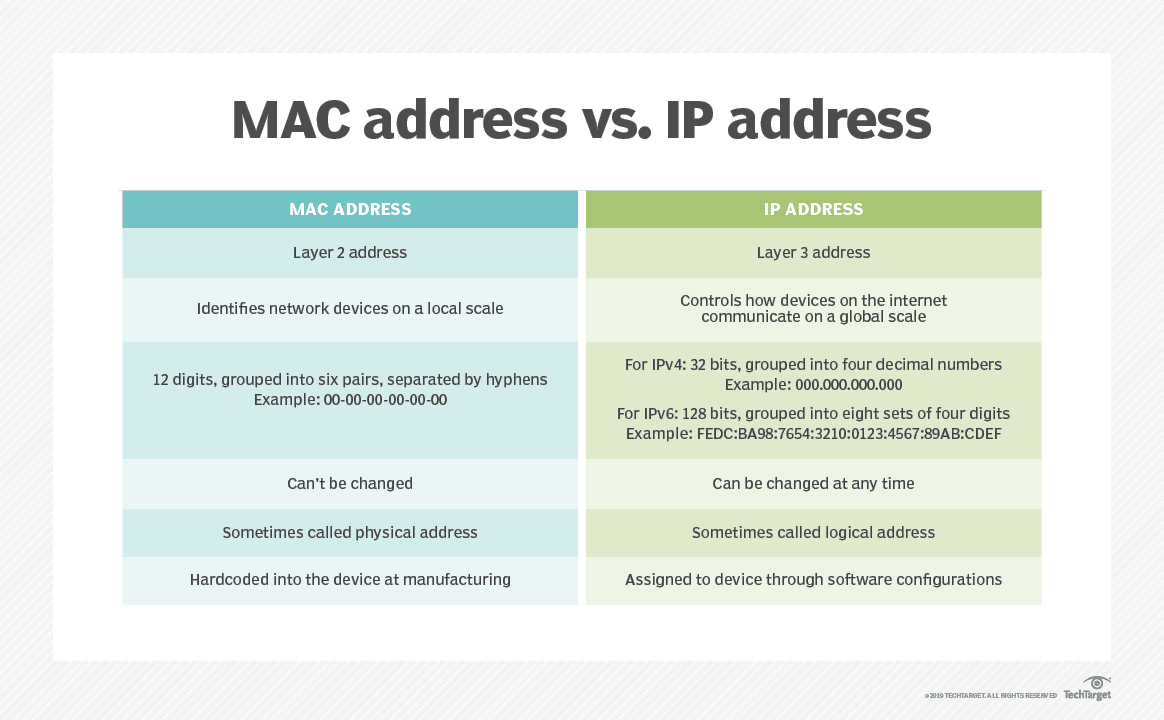
In short, MAC addresses and IP addresses identify devices on a network in different ways. Here are some of the main differences between the two:
- Addresses different layers. MAC and IP addresses work at different layers of the Open Systems Interconnection (OSI) Model, which describes the various stages data goes through as it’s sent between computers. While we won’t get too detailed here, MAC addresses work on the Data Link layer (or layer 2), which directly translates electrical signals sent over a wire and logical data. IP addresses work one layer higher on the Network layer (or layer 3), which handles addressing and routing throughout the network — almost like writing an address on an envelope.
- Local vs. global scope. MAC addresses are used for identifying different devices on a “local” scale, such as different computers sharing a network in an office building. IP addresses work more globally, controlling how devices across the Internet locate and communicate with each other.
- Different address formats. Since MAC and IP addresses work on different layers and do different things, they also have different formats. A MAC address has a serial number-like format of 12 digits grouped into pairs and separated by hyphens or colons (00:00:00:00:00:00), while a typical IPv4 address is a 32-bit address (bit meaning binary digit) grouped into four decimal numbers (000.000.000.0000). While you don’t need to know the specifics for now, note that associating these two address formats is the main function of ARP.
- MAC addresses are permanent. MAC addresses are assigned to a device by the manufacturer as soon as it’s built. This address is essentially “embedded” into the device’s network hardware, making it permanent and unchangeable — just like our mobile home’s serial number from earlier. IP addresses are temporary and are assigned whenever the device connects to a network. As a result, devices can assume any number of different IP addresses over its lifetime.
- Physical vs. logical. By extension of the above, a MAC address is also known as a physical address or hardware address, while IP addresses are sometimes (but not as commonly) known as logical addresses.
- Assigned at different times. As mentioned previously, MAC addresses are assigned once at the time of manufacture. IP addresses can then be assigned any number of times afterward, for as many times as the device connects to a network.
So where does ARP come in?
Since every computer has both addresses, there must be some way to associate one with the other so packets are delivered to the right place. This brings us to the core function of ARP: linking a device’s MAC address to its ever-changing IP address and vice versa.
Let’s take a closer look at how exactly this works.
How Does ARP Work?
Now that we’ve answered, “What is ARP?” let’s understand how it functions. ARP maintains an updated list of MAC addresses and their associated IP addresses. This list is usually maintained by a gateway or router — essentially, any network switch responsible for managing data flow between networks and devices.
To make sense of this, let’s take a look at the diagram below.
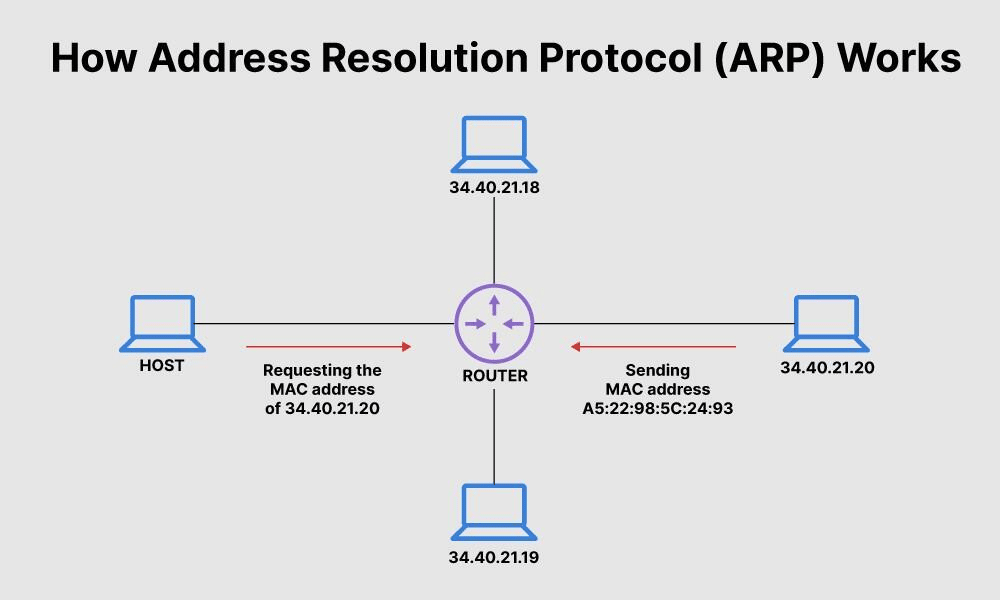
Here, the “HOST” computer on the left is trying to send something to the computer on the right with the IP address 34.40.21.20. To successfully send data to this computer, the HOST computer needs its IP address and MAC address.
Thankfully, the HOST computer already has the computer’s IP address. All it needs now is the computer’s MAC address, which is where ARP comes in.
Network-connected devices and switches (in this case, a router) maintain a list of known IP-to-MAC address translations on their operating systems. This list is known as an ARP cache or ARP table, which requires constant updates to keep up with the ever-changing IP addresses.
When a computer wants to send something to a specific IP address, it first checks its ARP cache to see if it has a matching MAC address. It sends out request packets for the MAC address if it doesn’t.
Let’s illustrate this process using the two computers in the diagram:
- The HOST computer checks its ARP cache to see if it already knows the MAC address of 34.40.21.20. If it does, it has everything it needs and sends the message.
- The HOST computer sends a request for 34.40.21.20’s MAC address.
- The router receives the request for network addresses from the HOST computer and uses ARP to try and locate the MAC address.
- ARP will try to reference the router’s existing ARP cache, and if the MAC address can’t be found, it sends a request to 34.40.21.20.
- 34.40.21.20 sends their MAC address (A5:22:98:5C:24:93) back to the router.
- The router updates its ARP cache and sends 34.40.21.20’s MAC address back to the HOST computer, completing the request.
- The HOST computer sends something to 34.40.21.20.
While this is only a basic example, it should give you some idea of ARP’s core function.
Another core function of ARP is maintaining (and purging) IP-to-MAC translations in the ARP cache. Keeping the ARP cache relatively clear isn’t just necessary for getting the latest information; it also helps eliminate inaccurate or unused addresses. As we’ll see later, purging translations is also necessary for preventing IP addresses from falling into the wrong hands.
Entries in an ARP cache can also be either dynamic or static. Dynamic entries are those populated automatically in the way we’ve already described. However, users can also manually specify static entries that they want to keep permanently. This is useful for persistent network devices with set (i.e., static) IP addresses.
ARP vs DHCP vs DNS: What’s The Difference?
If you’re even somewhat familiar with networking, you’ve probably heard of Dynamic Host Configuration Protocol (DHCP) and/or the Domain Name System (DNS). If so, you may also wonder how ARP in networking differs from these similar protocols.
- DHCP vs ARP: ARP exists largely because IP addresses are always being changed and reassigned on a network. DHCP is responsible for this constant change, being the protocol that configures a dynamic IP address for hosts — hence the name dynamic host configuration protocol. DHCP also helps avoid conflicts such as multiple computers being assigned the same IP address.
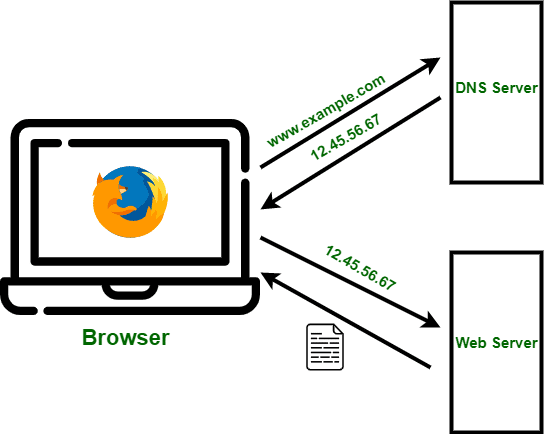
- DNS vs ARP: Where ARP associates IP and MAC addresses, DNS associates IP addresses and domain names (such as “kinsta.com”). All websites rely on web hosting to host their web pages, images, and anything else that comprises them. Like any other network device, web hosting servers have an IP address. Thanks to DNS, however, you don’t need to type in a host’s IP address to access a website. Instead, you simply type in a URL like “www.example.com,” and the DNS server fetches the matching IP address so your web browser can request and serve the web pages from the web host.
Uses and Types of ARP
Though ARP may seem like some big, monolithic process, it can be implemented in many different ways.
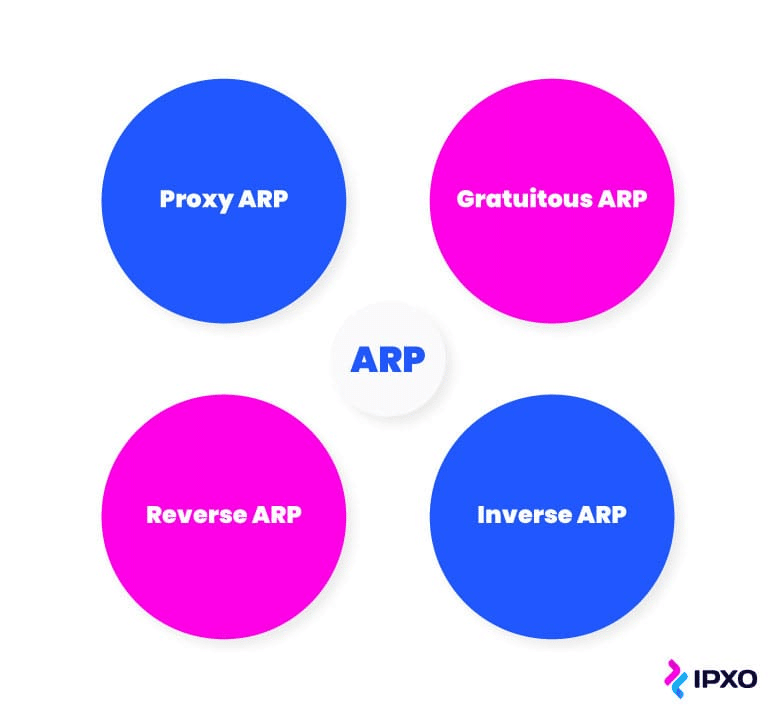
When explaining what is ARP, there are four special types: proxy ARP, gratuitous ARP, reverse ARP (RARP), and inverse ARP (IARP). Each type presents different use cases and in some cases, distinct advantages and disadvantages.
What Is Proxy ARP?
A proxy ARP is where an ARP-configured switch (such as a router) handles ARP requests (i.e., requests for MAC addresses) from devices/hosts outside its immediate network. The switch sends its own MAC address in response, effectively serving as a “representative” of every host in its network.
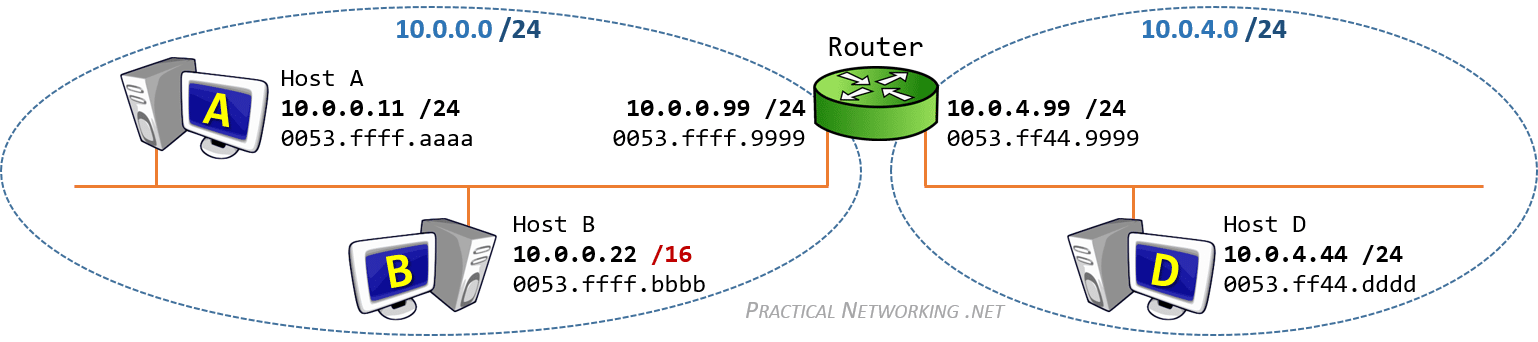
To clarify, let’s take a closer look at the diagram above. Here, the green router in the middle serves two separate local area networks: 10.0.0.0/24 and 10.0.4.0/24.
Let’s say Host B wants to send a message to Host D. While that would be no problem if Host D were on the same local area network (like Host A), it’s unfortunately on a different network. As a result, Host B finds itself in a tricky situation: how can it get the MAC address of Host D?
Thankfully, the router comes to the rescue. When Host B sends an ARP request message to the router, the router steps in and provides its own MAC address in response. With the router’s MAC address in hand, Host B sends its message to the router, which is now literally acting as a “proxy” for Host B. The router then sends Host B’s message to Host D, the intended recipient.
As you might imagine, proxy ARP is extremely common in computer networking, with typical uses including VPN connections and firewalls.
However, there are some disadvantages to proxy ARP, most of which stem from improper configurations. One such disadvantage is the increased risk of sending messages to the wrong places, as devices outside the network might not be aware of improper configurations when only dealing with a proxy ARP. Proxy ARPs can also serve as vectors for denial of service (DoS) attacks, which we’ll explore a little later.
What Is Gratuitous ARP?
A gratuitous ARP is an ARP response that wasn’t previously requested. In other words, gratuitous ARP is gratuitous with sending ARP responses, effectively broadcasting its IP-to-MAC translation to every host/device on the network. It’s almost like someone sending a “mass email” to let everyone know they’ve updated their contact information.
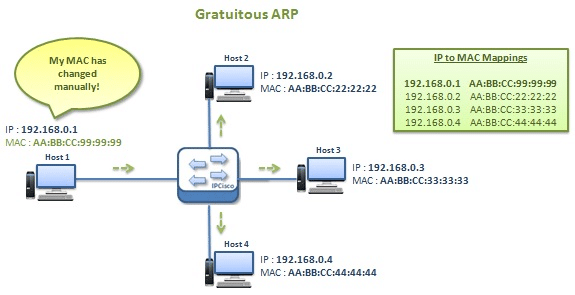
Gratuitous ARP has several useful applications. For one, it’s essential for updating ARP caches and mapping, especially when a new device or node joins the network. In the case of a new device, gratuitous ARP avoids sending and responding to individual ARP requests to every other device on the local network.
Ensuring redundancy is another important use for gratuitous ARP. For example, some redundant networks might use two or more routers with the same IP address. When one of these routers fails, the “surviving” router sends a gratuitous ARP to inform the network where to send messages.
What Is Reverse ARP (RARP)?
Reverse ARP (RARP) does exactly what its name suggests. It sends an IP address instead of a MAC address.
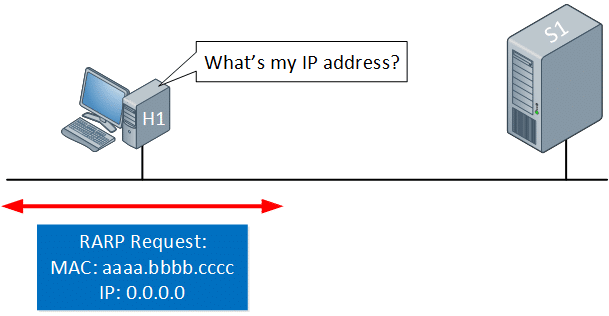
But why do this at all? Aren’t IP addresses already known to hosts on a network?
Not always. Unlikely as it may seem, some hosts don’t even know their own IP addresses. This is often the result of a host simply not having the memory or space to store their IP information, making a RARP request necessary for communication. Remember, only MAC addresses are permanently assigned — and, as a result, hosts may not know anything beyond their MAC address!
What Is Inverse ARP (IARP or InARP)?
Like RARP, inverse ARP (abbreviated as either IARP or InARP) also sends IP addresses instead of MAC addresses. However, unlike RARP, inverse ARP works exactly the same as traditional ARP, only that it translates MAC addresses to IP addresses rather than IP addresses to MAC addresses.
IARP is especially useful for ever-changing IP addresses (thanks again to DHCP). Here, a host might know the MAC address of another host or router whose IP address has since changed. With only the MAC address in hand, IARP is necessary for the host to get the new IP address and send their message.
What Is ARP Spoofing?
Also known as ARP Poisoning, ARP Spoofing is where hackers send fake ARP messages to a target network in an attempt to link their own MAC address with a legitimate IP address on the network.
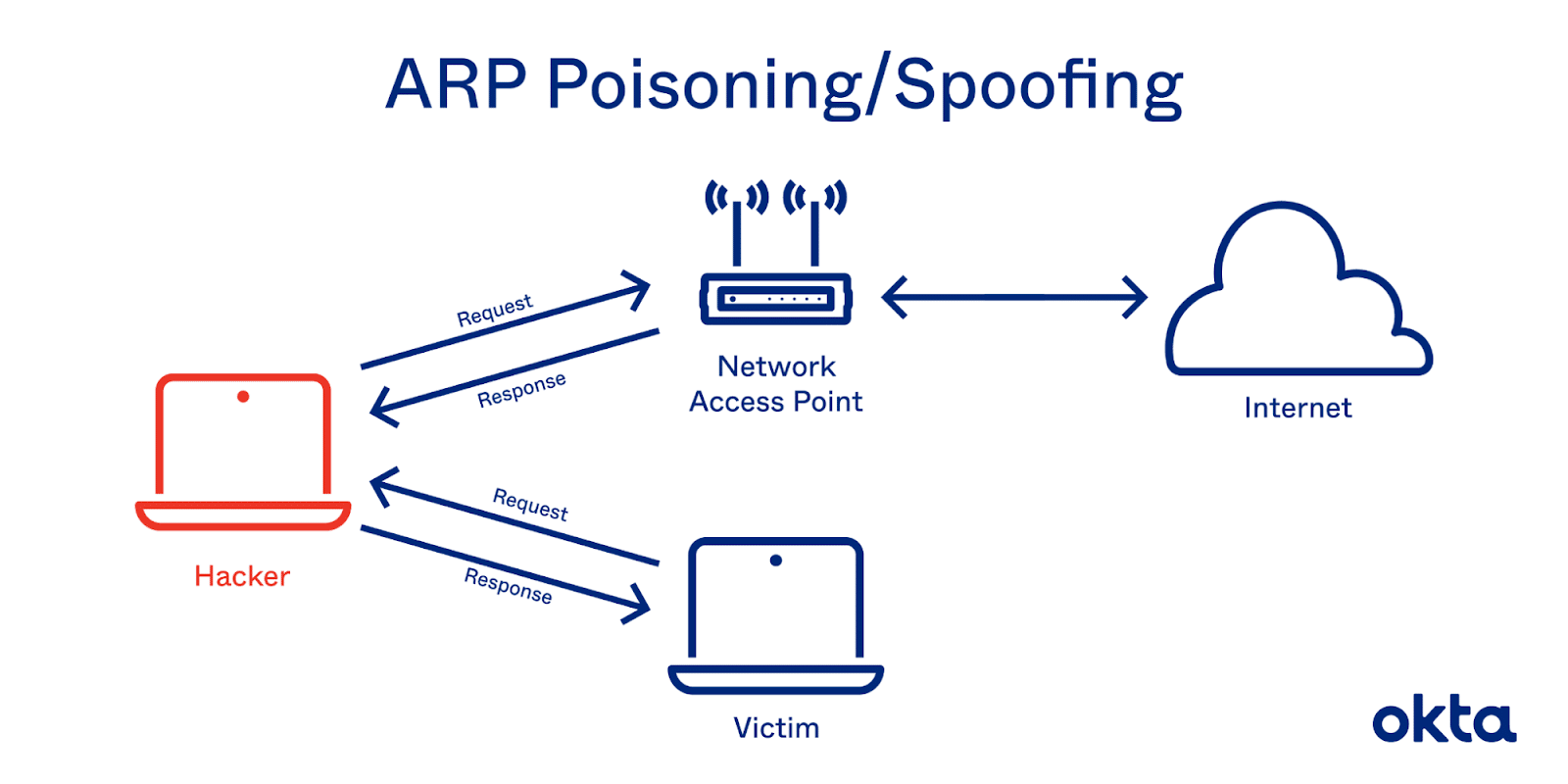
If successful, messages intended for the computer with the legitimate IP address will be sent to the hacker instead. This allows the hacker to launch several other types of cyber attacks, including:
Man-in-the-Middle (MTM)
A man-in-the-middle (MTM) attack is where a hacker “eavesdrops” on network traffic, potentially intercepting valuable data such as passwords, bank information, etc. In the case of ARP spoofing attacks, hackers use fraudulent ARP messages to redirect network traffic through their computers, often passing it along to the intended recipient to make it look like nothing has happened.
Session Hijacking
Session hijacking is where a hacker steals and assumes a user’s session ID, a special type of data that authorizes users to perform certain actions on websites. Often distributed by websites in the form of cookies, session IDs allow users to stay logged in or access saved shopping carts.
By redirecting traffic through ARP spoofing, hackers can easily gain access to session IDs and impersonate the user. This means they’ll be able to do anything the user is authorized to do, such as access logged-in bank accounts.
Denial-of-Service (DoS)
A denial of service (DoS) or distributed denial of service (DDoS) attack can take one of two forms: a hacker blocking messages to a host or a hacker overwhelming a host with too many messages. The latter is more often the case.
In either case, however, ARP spoofing is what allows hackers to either block or transmit messages en masse. By intercepting regular network traffic, the hacker can block messages to their intended recipients or redirect them to a single target.
Summary
Here we’ve provided an in-depth answer to “What is ARP?” — one of the most common and useful protocols in computer networking. Thanks to ARP, computers and network devices can associate physical MAC addresses with ever-changing IP addresses, allowing for the easy communication we enjoy today.
However, even the most well-intentioned ARP can lead to security vulnerabilities and cyberattacks. With security features like DDoS protection, Kinsta’s managed WordPress hosting can help protect against many cyberattacks linked to ARP spoofing.


