So, you’re staying safe at home. But are you staying safe while working from home? There are some important work from home security tips we need to go over to effectively keep your data safe.
Working from home is peaceful and fun. It’s been around for decades but has gained momentum since the current global pandemic started.
The trouble is, working from home also brings cybersecurity risks, especially for small businesses that don’t have a proper IT infrastructure. Employees who lack security awareness can cause a great deal of harm to themselves and their employers.
Here at Kinsta, we’ve been fully remote from the beginning and always have openings for those seeking remote work.
That’s why in this comprehensive guide, we’re going to help you learn about the most common cybersecurity risks that you could face while working from home. We’ll also share important work from home security tips to help you stay safe as you do your work online.
Keep reading!
6 Common Work From Home Security Risks
Before we jump into the tips on staying safe online while working from home, let’s first take a look at the common types of cyberattacks on remote workers.
1. Phishing Scams
One of the biggest cyber threats to remote employees is phishing attacks. Even though phishing scams originated in the mid-1990s, they’re still widespread to this day and have become more sophisticated with the advance of technology.
Phishing is a type of cyberattack that aims at stealing confidential data such as credit card numbers, bank account details, and login credentials (e.g. usernames, passwords, and personal identification numbers). Not only does phishing directly harm you as an individual/employee, but it also presents a security risk to your organization/employer.
So, how does phishing work?
The attacker poses as a trusted entity to lure the target victim into clicking on a malicious link usually sent through an email or text message. When the recipient opens the infected link, they unwittingly install malware or even ransomware on their devices.
While the most common type of phishing scams is done via email, many phishers use other means of infection, including SMS (smishing), voice-based scams (vishing), social media-based threats, or even through USB flash drives.
With the spread of COVID-19, phishers are taking advantage of the pandemic to carry out cyberattacks through emails that contain links claiming to have important information about the virus.
2. Weak Passwords
Weak passwords are another major security risk and a doorway for hackers to wreak havoc for employees and companies, especially small- to medium-sized businesses. Would you believe that it takes only one weak password for attackers to breach an entire network?
Even though a lot of companies invest in cybersecurity to combat security threats and data breaches, weak passwords used by employees make it easy for hackers to get access to not only their personal computers but also business data.
The Verizon Data Breach Investigations Report revealed that 81% of the total data breaches were due to using weak passwords. That’s a whopping percentage.
Attackers use many different methods to hack passwords, such as credential stuffing, dictionary attacks, brute-force attacks, and rainbow table attacks. Let’s briefly cover what each of these is.
Credential Stuffing
This is one of the most common attacks used by hackers by running database lists of breached login credentials automatically against the target website login. In this kind of attack, hackers rely on many users employ the same passwords and password variations.
Dictionary Attack
This is a type of password-guessing attack where hackers use a dictionary of commonly used words often seen in passwords. Individuals who use real words or phrases in their passwords are highly vulnerable to this kind of attack.
Brute Force Attack
This is another type of password-guessing attack in which hackers submit as many password combinations (letters, numbers, and symbols) as possible until a password is eventually cracked.
Rainbow Table Attack
This hacking attack uses a rainbow hash table that contains the values used to encrypt passwords and passphrases. It’s similar to a dictionary attack, but hackers use a table instead of a list of words.
3. Unsecured WiFi Networks
While working from home has its perks, if you’re connected to an unsecured WiFi network — such as public WiFi networks available in cafes, restaurants, hotels, libraries, co-working spaces, or airports — this could create security problems for you and your employer.
A public WiFi network is like a Disneyland for hackers and cybercriminals: It allows them to easily hack into devices to steal your personal data and identity.
Hackers use some popular techniques to attack your computer or smartphone while you’re using an unsecured WiFi network. Let’s discuss a couple of them.
Machine-in-the-Middle (MITM) Attack
This is an eavesdropping attack where a hacker can intercept the data transmitted between a client (your device) and the server you’re connected to. The attacker then has the ability to communicate with you through fake websites or messages to steal your information. Public WiFi networks are common targets as they’re either poorly encrypted or not encrypted at all.
Evil Twin Attack
This is a type of MITM cyberattack in which hackers take advantage of poorly encrypted or unencrypted WiFi networks (usually public WiFi/hotspots) to set up a fake WiFi network with a fake (evil twin) access point. Once you join this fake network, you unwittingly share all of your information with the hacker.
4. Using Personal Devices for Work
While some organizations provide their employees with devices for remote work, most companies still allow their employees to use their personal devices (e.g. laptops, desktops, tablets, and smartphones). The result? A growing number of security and data breaches.
When employees work from home using their personal devices, they often don’t consider that these devices aren’t based on their company’s IT infrastructure, nor do they share the same security measures. That’s why personal devices are more vulnerable to cyber threats.
Moreover, employees who work from home using their personal devices can visit any website they want and install any apps or software programs that might otherwise be blocked by an employer for security reasons, making them an easy target for malicious activities and hackers.
5. Malware and Viruses
Malware and viruses have become very sophisticated, creating serious problems for businesses and individuals, especially during these difficult times of the pandemic. Poor security measures and reckless employee behaviors lead to the spread of malware and viruses.
Wait — aren’t malware and viruses the same thing?
The answer is no. While viruses are a type of malware, not all malware is a virus.
Malware is a collective term for any malicious software created to infect and cause damage to the host system or its user. There are different types of malware, including viruses, worms, trojan, ransomware, spyware and adware, and scareware.
A computer virus is a type of malware created to replicate itself and spread to multiple devices as widely as possible through infected websites, applications, emails, removable storage devices, and networking routers, just like a biological virus. The point of a computer virus is to cause as much harm as possible without the user’s knowledge. It can easily spread through servers and destroy websites.
6. Unencrypted File Sharing
If you think malware, viruses, and hackers are dangerous, unsecured file sharing is equally dangerous and even riskier for remote working.
Remote employees may inadvertently put critical business data at risk through poor practices. Sharing files through unencrypted emails makes it as easy as shooting fish in a barrel for hackers to intercept those emails and steal information.
Using cheap and poorly secured cloud file sharing such as personal cloud storage drives is another risk factor. In addition, employees who use peer-to-peer (P2P) file-sharing pose a threat to their company since anyone can get access to data files on their devices, including hackers.
Flash drives can also be dangerous if infected with malware as they can easily bypass network security. It gets worse if an employee sets their system to autorun a flash drive, which allows malicious content.
Work From Home Security Tips to Protect Your Data
Here’s our roundup of the best cybersecurity tips for secure working from home. Make sure to consult with your employer first to be certain that you’re both on the same page.
1. Invest in Good Security Software
There are numerous security software brands on the market that help defend you from cybersecurity threats. Most of these software applications protect your devices against a wide range of different types of threats at the same time.

Nowadays, there’s a multitude of software for different types of attacks, including antiviruses, antimalware, hacking attempt blockers, and DDoS defense. Some programs are free while others are paid, with prices ranging between cheap ($2) and expensive ($120) depending on the protection features they offer.
But, as cyber threats are continuously evolving and becoming stronger to bypass this software, it’s better to go for the paid versions as they are usually more comprehensive and include more robust security features to combat vicious threats.
Bear in mind that what separates reliable security software from a poor one is the frequency of its updates. In other words, if the software continuously updates itself, that means it’ll always be aware whenever a new threat is introduced to the computer world.
2. Separate Work Devices from Personal Devices
If you’re working from home, it’s preferable to use two separate devices for work and personal use. In this case, if one device gets compromised by an unwanted threat, the other won’t be affected.
This doesn’t only go for your computers, but for any device connected to the internet that’s open to external risks. This includes your computer, your mobile device, your tablet, etc. It even applies to other devices like portable storage units.
If you don’t already have separate devices, then we strongly recommend you make the change. Some employers provide their employees with dedicated work devices, especially during the current pandemic. If this is the case with you, then you’ll have no problem.
Another important step we recommend is to always keep separate but continuously updated backups of your important work files. In this case, you can use your personal devices just for the sake of these backups — except, of course, if this information is highly confidential.
3. Keep Operating System Up to Date
Most major operating systems have their own defense tools such as firewalls to prevent certain threats from affecting your device. Like with security software, these tools need to be constantly updated to keep in line with newly introduced threats.
These tools are updated with the updating of the operating system. That’s why it’s highly recommended to always keep your operating systems up to date on all your devices.
Most operating systems give you the option to either have the updates take place automatically or manually. We recommend you keep it set to the automatic option to have updates take place as soon as they’re available.
Another important pointer is to make sure that the operating system you’re using is 100% authentic. This is more common with Microsoft Windows than other operating systems, as some people install a copy of Windows without having the proper activation key required to keep all its built-in security tools working properly.
4. Keep Software Up to Date
Software updates aren’t limited to your OS — it’s also crucial to keep all the software and programs you use on your devices up to date constantly, especially those programs that rely on connecting to the internet to work.
This includes, but isn’t limited to, your browsers and communication programs (Zoom, Skype, Whatsapp Messenger, etc.). All these programs usually have their own built-in security measures, which, like any security software, require regular updates to face any newly introduced threats.
On your work devices, it’s also important to only install the programs you actually need for work and keep all other programs such as games, streaming apps, and so forth on your personal devices. This pairs with the “separate work devices from personal devices” tip that we discussed earlier.
5. Secure Your WiFi Network
Today, almost every home uses a wireless internet network, or WiFi, instead of a wired ethernet cable. As you know, to connect to the network requires a password, which you created when setting up your router. This password is a major factor in determining whether your home internet network is secure or not.
The least damaging result of your network being penetrated is your internet speed slowing down as several unwanted devices are connected to it and using it. However, more serious issues can occur, like cybercrimes being committed by other parties using your network, which will be traced back to you.
If you have a nosey neighbor with some techy skills, there’s always a risk of them figuring out your password and penetrating your network. That’s why it’s important to have a complex password, but not so complex that you end up forgetting it yourself.
It doesn’t end there. You should also change your password from time to time to keep it even more secure. Finally, don’t forget to install your firmware updates regularly to protect your network from any new vulnerabilities.
If you’re working off of a public network (coffee house, hotel, etc.), it’s recommended that you choose to keep your device invisible on the network (check your sharing options when connecting to the network).
6. Use a VPN
A virtual private network (VPN) is best known for bypassing geolocations online to access streaming websites that are blocked in certain locations around the world. However, VPNs are also used for security reasons. For instance, they encrypt your connection and secures all your browsing data from unwanted breachers.
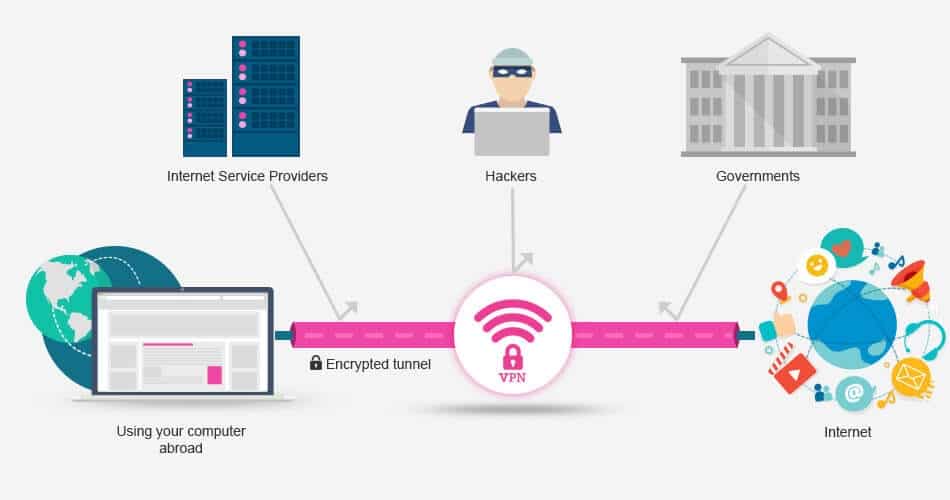
When you connect to a VPN, instead of your data going through the internet service provider’s (ISP) servers, it goes through the VPN’s company servers. In this process, your IP is changed, thereby hiding your true online identity.
There are numerous VPN names on the market today, and all of them serve the same purpose, more or less. However, there are a few key factors to consider when choosing the right VPN for you.
First off, you must make sure that the VPN you choose actually works in your country, as several countries block the usage of a VPN. You can find out by asking the VPN’s customer support before subscribing.
Other factors include the levels of encryption the VPN supports (L2TP, OpenVPN, etc.) and the number and locations of its servers. The level of encryption can determine whether or not a VPN is secure enough. Many VPNs today support multiple encryption levels, which are suitable for different situations.
The number and locations of the VPN servers determine whether or not you’ll find a close enough server to your geolocation to benefit from faster connection speeds. The closer the server, the faster the connection speed is.
VPNs come with several security features. One useful feature you might come by is the kill switch. The purpose of this is to block your internet connection altogether in the case that, for any reason, your VPN connection drops unexpectedly. This protects your devices from being exposed during this connection drop.
Other VPNs offer browser extensions and apps for different devices and operating systems (Windows, Mac, iOS, Android, Linux, etc.). In some cases, you can even set up your home router to connect directly through the VPN, thereby securing all devices connected to the network at the same time.
7. Physical Security
When working from your company’s office, it’s not your responsibility to keep your devices physically secure from theft. There’s usually security staff taking care of that for you, though in some cases, you may be required to lock your office or computer before leaving.
The same concept applies at home, but the reasons are different. At the office, it’s only you and your tech-savvy staff walking around, but at home, there are children, pets, relatives, or even friends. We’re not implying that you can’t trust them or that they’ll intentionally affect your work devices, but you still need to keep your data safe from unwanted fiddling.
This can be done by keeping all your work-related devices and items (documents, files, etc.) locked in a separate room — or, when you’re not using them, keep them locked in a safe cupboard or anyplace that only you can access.
8. Use a Secure Browser and Search Engine
We already know that popular browsers and search engines, such as Google and Bing, collect your data for their own advertising purposes. This is concerning when it comes to your work, as you’re likely dealing with sensitive information.
Don’t get us wrong — we’re not implying that these search engines are bad! But when it comes to your work, it’s better to be safe than sorry. That’s why it’s fine to use them in your everyday personal life, but it’s preferred to use a more private alternative when working.
There are several search engine alternatives that serve that purpose. The most popular one is DuckDuckGo. Not only does it have a search engine that collects very minimal data, but it also has its own browser for mobile devices that bears the same privacy concept.
Unlike most search engines, DuckDuckGo doesn’t collect any information that gives away your online identity. Instead, it allows you to browse the internet without a user profile, which is useful to avoid personalized ads or search results.
9. Back Up Your Data
There are several factors that can cause you to lose your data, and that’s why keeping separate but continuously updated backups are one of the most important tips on our list. There are two main ways to keep backups: physical backups and cloud backups.
Physical backups are the more traditional method that involves keeping a backup of your data on a separate hard drive or, more preferably, a portable hard drive. How frequently you update your backups depends mostly on your workload. In other words, the more work you do, the more frequent backups are required (e.g. daily backups, weekly backups, etc.).
Unlike physical storage drives, cloud storage is based on remote servers you can access from any device anywhere in the world. You can also share this access with your coworkers, employees, or employers. In addition, the risk of the storage unit being damaged and causing a loss of data is far less than with physical storage drives that you keep with you.
Today, numerous cloud storage services are available, all of which vary in capacity availability, features, and price. The most popular of these services are Google Drive, Dropbox, Microsoft OneDrive, Apple iCloud Drive, and IDrive.
Our advice? Invest in a highly secure cloud storage solution to safeguard your data, and remember to secure yourself on the cloud.
10. Use Encrypted File Sharing
All major operating systems today come with a built-in encryption tool that allows you to encrypt all the files on the device. However, you have to enable it yourself, as this tool isn’t activated by default. It’s more important to encrypt the files shared between you and your coworkers/employees/employers.
These files are accessible by numerous parties (the people you’re sharing them with), and hence they’re at the risk of being exposed to unwanted breaches.
We’re not saying that encrypting your files will completely prevent bad actors from getting their hands on your data, but it’ll surely decrease their chances greatly. And even if they do access the information, it’ll be encrypted, which will make it difficult to make use of.
11. Set Up Two-Factor Authentication
Two-factor authentication (2FA) is a relatively new security measure that many services are turning to to further secure users’ accounts. It requires an additional verification step to either sign in to an account or perform a transaction (like financial services).
For instance, when you try to buy something online using your credit card, some card services require you to enter a one-time password (OTP) that’s sent to your phone via text message. To complete your transaction, you must then enter this code to complete your purchase as a type of security verification. This helps to prevent unauthorized transactions.
A similar method is used in many cases, such as when you forget your password and need to reset it. Some services apply this method by default, while others give you the option to utilize or disable it.
Whenever prompted, it’s highly recommended to agree to use 2FA to further secure all your accounts.
12. Use Strong Passwords
Whether on your phone or computer, you should use highly unpredictable passwords that only you can remember. They don’t have to be long, but they do have to be as complex as possible. Proper password management is one of the most important work from home security tips you will receive.

This means they should, at a minimum, contain both numbers and letters. Your passwords should contain a combination of uppercase letters, lowercase letters, numbers, and non-alphanumeric characters (question marks, ampersand symbols, etc.).
Even though we recommend having highly complex passwords for all your accounts, you shouldn’t go so complex that you end up forgetting the passwords you set.
It’s also important to avoid using a single password for all your accounts. If multiple passwords are too difficult to remember, you can always use a password manager.
A reliable password manager helps you set up strong passwords across all accounts and makes it easy to submit your login credentials to any site — all without you having to remember your passwords yourself. These managers also facilitate the process of periodically updating your passwords.
Password managers can be used on a personal or corporate level, helping all your employees keep their accounts secure and circumventing the risk of one or more employees causing a data breach by applying weak passwords.
13. Watch Out for Phishing Sites
This one may seem rudimentary: Don’t click on suspicious links.
Sounds simple, right?
Well, it’s a little more complex than that. We’re sure by now you won’t fall for the Nigerian prince scam email, but phishers today are becoming much sneakier.
While working, you should only click on links related to work and from trusted sources. If an email looks suspicious in any way, don’t open it. And if you’re curious about something you received, such as a link claiming to contain important COVID-19 information, check with trusted sources first (e.g. WHO, CDC, etc.).It’s also important to learn how to identify a secure website.
If your work requires research and browsing unknown websites, don’t be tempted by the different ads displayed on those websites. Just stick to your target information and leave the website.
14. Lock Your Devices
This advice goes for both your smartphone and your computer. Whenever you’re not using them, always keep them locked with a password. Some phones today even use fingerprint recognition for unlocking in addition to passwords. Others use patterns, facial recognition, and several other methods.
When we worked in offices, we were always required to lock our office computers when we were not present to prevent unauthorized access and our work information from being compromised.
This also applies when at home, but for different reasons. For instance, when you’re not working, you wouldn’t want your kids accessing your computer and messing up your work. Make sure to use strong passwords when locking your devices.
15. Use Multiple Email Addresses
Just like using separate devices for work and personal use, the same goes for email addresses. Having a separate email account for your work and another for your personal use is important to avoid any of the accounts being affected if the other becomes compromised in any way.
It also makes you look more professional, especially if you’re a freelancer dealing with different clients. Let’s be honest. We’ve all been at that place of having an embarrassing personal email address at one point in our life. This was fun when using it for social media or school, but that’s a different story in a work environment.
It doesn’t have to be just an account for work and another for personal use. You can have several different accounts for different purposes. For instance, you can have an account for work, another for finances (banks, money transfers, etc.), one for social media, and one for all other personal uses.
The more accounts you use, the more secure you’ll be. However, make sure not to overdo it and end up forgetting passwords, the email addresses themselves, or getting confused about which email address is set for which purpose.
16. Enable Remote Wipe
This feature is not just useful for your work devices but also for your personal devices. Most operating systems today come with a feature that enables you to wipe their entire storage remotely. This is useful if your device is lost or stolen to keep all your data from falling into the wrong hands.
Before enabling this feature or using it, make sure that you have updated backups on a separate device or cloud-based (as previously mentioned). If your device gets lost or stolen and this feature is enabled, once the device is turned on and connected to the internet, you’ll be able to delete all the data on it from any other device, from anywhere in the world.
17. Watch Out for Third-Party Apps
Surely not all the apps you use for work are created by your company, and you likely rely on a few third-party apps. You can’t always be sure if these apps, or third-party service providers, are taking the same security precautions as you, and so it’s highly recommended to make sure that the apps you use are trustworthy.
The best way to know if these apps are safe to use or not is to view their security ratings on review websites. It’s like doing a background check for a potential client or business partner. There are numerous well-known websites out there that are specialized in these kinds of reviews.
18. Enable Access Control
Access control is a fundamental element of data security, most importantly with remote working. It’s a method to guarantee that employees are indeed who they say they are. When it comes to working from home, logical access control should be a top priority.
By logical access control, we refer to setting up an automated system that can control a user’s ability to access the company’s system resources such as networks, applications, and databases. The system can automatically identify, authenticate, and authorize users attempting to access it.
By virtually restricting access to a company’s data, you can secure your business and minimize cybersecurity threats like data breaches and data leaks.
19. Turn Off Network Name Broadcasting
When setting up your WiFi network at home, you can choose to have the network name visible for anyone that has the WiFi turned on on their device or have it invisible, and to connect, the user has to type in the name of the network (turning off network name broadcasting).
If someone with bad intentions can’t see your network, they won’t try to hack it. The first step to hacking a network is being able to see this network. If that feature is turned off, the risk of it being hacked decreases greatly.
20. IT Support and Cyber Security Training for Employees
A word to the wise: Don’t skip your company’s cybersecurity training. This is so important, especially if your company has shifted to working remotely from home.
Companies must not ignore providing useful cybersecurity training sessions for their employees if they want to keep their business afloat during these hard times. As an employee, it’s important to attend those security sessions and follow your company’s cybersecurity policies to protect yourself and your company from any harmful cyber threats.
Summary
To wrap up, organizations and employees must take work from home security risks very seriously.
Even though working from home has proven to be successful, more productive, and more convenient, without taking proper cybersecurity measures, it can turn into a real nightmare for employees and businesses.
However, if you follow the security tips discussed above, you’ll enjoy a safe and efficient remote working experience.
Got any questions left about how to keep your data safe while working from home? Let’s discuss this in the comments section!


