Distributed Denial-of-Service (DDoS) attacks are one of a website’s most challenging threats. The number of DDoS attacks continues to rise every year.
The Q4 2023 DDoS threat report by Cloudflare says that the company noticed a 117% year-over-year increase in network-layer DDoS attacks and overall increased DDoS activity targeting retail, shipment, and public relations websites during and around Black Friday and the holiday season.
This shows that the number of DDoS attacks is growing as they are used against businesses and governmental institutions to wage cyber attacks. For example, Cloudflare reported an increase in DDoS attacks following the start of the Israel-Hamas war.
How DDoS attacks work
DDoS attacks can strike at any time and aim to overwhelm a server, service, or network with excessive Internet traffic, disrupting normal operations.
DDoS attackers often use botnets — compromised computer networks, known as “zombies” or “bots.” These bots are typically infected with malware and controlled remotely by the attacker.
When the attacker initiates a DDoS attack, they command all the bots in the botnet to send a massive volume of requests to the target server or network. This overwhelming influx of traffic exceeds the server’s capacity to handle legitimate requests, causing a slowdown or complete outage.
There are three types of DDoS attacks:
- Volume-based attacks — These are the most common types of DDoS attacks. They aim to saturate the bandwidth of the targeted site or network. Techniques include UDP floods, ICMP floods, and other spoofed-packet floods.
- Protocol attacks —These attacks consume server resources or intermediate communication equipment like firewalls and load balancers. Examples include SYN (synchronize) message floods, fragmented packet attacks, and the oversized packets used in ping-of-death attacks.
- Application layer attacks — These are the most sophisticated and stealthy DDoS attacks, targeting specific applications or services. They generate legitimate-looking requests but in large volumes, making distinguishing between legitimate traffic and attack traffic hard. Examples include HTTP floods and Slowloris attacks, which can be effective at lower request volumes than standard HTTP floods by keeping server connections open.
How to prevent DDoS attacks
Preventing DDoS attacks requires a strategic and multi-layered approach. By combining various methods, you can effectively safeguard your network and applications.
Here are five methods that can help prevent DDoS attacks:
1. Implement network and application protection
Start by limiting the number of requests a user can make to your server within a specific time frame. For example, if you run an online store, you can configure your server to allow only 10 requests per second from any user. This helps prevent a single client from overwhelming your server with too many requests at once.
Next, use a web application firewall (WAF). A WAF acts like a security checkpoint, inspecting incoming traffic and blocking harmful requests while letting legitimate ones through. For instance, if you’re using Cloudflare, its WAF can filter out malicious traffic based on known attack patterns. Regularly updating your WAF rules is crucial to keep up with new threats.
Additionally, deploy intrusion detection and prevention systems (IDPS). These systems are like security cameras for your network, watching for suspicious activity and automatically blocking anything harmful. For example, Snort is a popular open-source IDPS that detects and prevents attacks.
2. Leverage scalable and distributed infrastructure
Using scalable and distributed infrastructure helps manage and mitigate the impact of DDoS attacks. Anycast network routing is a great technique. Imagine you have a popular blog with readers all over the world. Anycast routing directs incoming traffic to multiple data centers, so if you’re hit with a lot of traffic, it gets spread out across different locations, reducing the burden on any single server.
Load balancers are another useful tool. They act like traffic cops, directing incoming traffic to multiple servers so no single server gets overwhelmed. For instance, AWS Elastic Load Balancing can automatically distribute traffic across several Amazon EC2 instances.
Content Delivery Networks (CDNs) like Akamai’s or Cloudflare’s can also play a big role. CDNs store copies of your website’s content on servers around the globe. If traffic suddenly spikes, the CDN can handle it by serving content from multiple locations, reducing the load on your main server.
3. Use specialized DDoS protection services
Specialized DDoS protection services are like hiring a personal bodyguard for your website. These services continuously monitor your traffic and use advanced techniques to filter harmful traffic. For example, services like Cloudflare’s DDoS protection or AWS Shield can detect and mitigate attacks in real time.
These providers have robust global infrastructures that can handle even the largest attacks. It’s like having a team of security experts constantly watching over your website.
4. Monitor and respond to traffic anomalies
Keeping an eye on your traffic is crucial. Use real-time traffic analysis tools to spot anything unusual. For example, your hosting provider could provide analytics that can help you monitor traffic patterns and detect anomalies. If you see a sudden spike in traffic from a single source, it could indicate a DDoS attack.
Set up rate-based alerts to notify you when traffic exceeds certain limits. For instance, if your usual traffic is 100 requests per minute and suddenly jumps to 10,000 requests, you’ll get an alert. Tools like Datadog can help you set up these alerts and monitor your traffic in real time.
5. Implement robust access control and regular audits
Finally, control who can access your network. Implement IP blocklisting to block known malicious IP addresses and IP allowlisting to allow only trusted addresses. For example, you can configure your server to block traffic from IP addresses flagged for malicious activity in the past.
Conduct regular security audits to find and fix vulnerabilities. This is like having a routine medical check-up to ensure you are in good shape. Tools like Nessus can help you scan your network for potential weaknesses and ensure your defenses are up-to-date.
How Kinsta prevents DDoS attacks
Your hosting provider can play a key role in protecting your site from DDoS attacks. In fact, if you use a good hosting provider, they should handle all the DDoS prevention techniques listed above.
At Kinsta, we are committed to mitigating all DDoS attacks on our platform. We implement robust security measures to prevent these attacks, notify you immediately if an attack occurs, and assist in fending off them. Additionally, we take daily automatic backups of your WordPress site to ensure your data is safe.
To give you a clearer picture, we asked some of our Security, DevOps, and SysOps engineers at Kinsta how we prevent DDoS attacks. They had a lot to share.
Enhancing Kinsta security through Cloudflare integration
A crucial component of our effort to provide our customers with the highest level of security is our Premium-Tier integration with Cloudflare. This strategic integration allows us to effectively handle and mitigate DDoS attacks, ensuring uninterrupted service and enhanced protection for our users.
Statistics provided by the DevOps team show that within the last 30 days (April 22 – May 23, 2024), we’ve served a staggering 75.51 billion requests through Cloudflare. Out of these, 3.3 billion were mitigated by Cloudflare’s Web Application Firewall (WAF), ensuring that potential threats never reach our clients.
We also received alerts for 200 DDoS attacks, all of which were automatically mitigated by Cloudflare. One of the most significant attacks we faced recently was back in March, with a peak of 318,930 requests per second, which we handled seamlessly with Cloudflare.
These numbers highlight how robust our security measures are, demonstrating the continuous protection we provide to our clients and showcasing the value of our Premium Cloudflare integration.
Historically, before our integration with Cloudflare, we had to manage all attacks manually. If an attack wasn’t too intense, we could SSH into load balancers (LBs) and analyze traffic using tools like tcpdump and Wireshark. Based on our findings, we would ban specific IPs or create targeted iptables rules and firewall rules to mitigate the attack.
We also temporarily resized LB instances to handle the load and tweaked various kernel settings. Over time, we automated many of these processes, running scripts to set and unset iptables rules and kernel parameters as needed. If an attack was too intense, we cloned LBs and multiplied instances to distribute the load.
As attacks became more frequent and sophisticated, we integrated Cloudflare into our hosting infrastructure to ensure our clients’ sites were safe and sound. We immediately started noticing fewer attacks reaching our servers.
Kinsta’s current DDoS mitigation infrastructure
Today, we have one of the best hosting infrastructures to fend off DDoS attacks, thanks to built-in tools, a dedicated team, and our integration with Cloudflare.
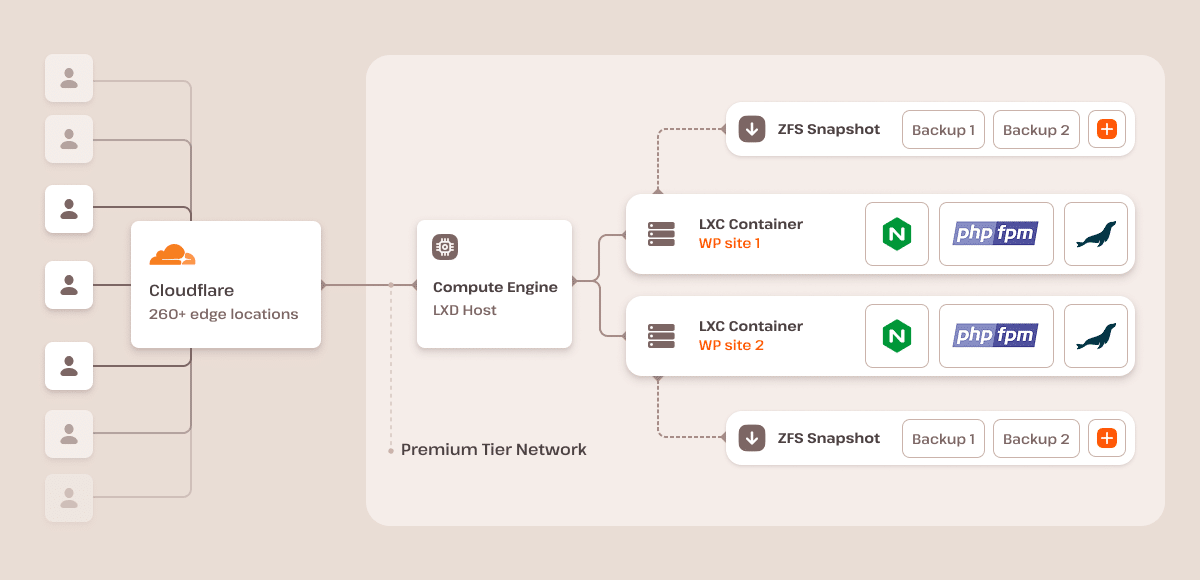
After integrating with Cloudflare, we effectively eliminated low-level sync flood attacks because all of our web traffic is routed through Cloudflare. This provides DDoS protection (layers 3, 4, and 7) to block unwanted TCP/UDP connections originating from specific IP addresses or networks at the edge of our network.
Kinsta provides a fully managed WAF with regularly updated custom rulesets and configurations, ensuring continuous protection against the latest threats.
Furthermore, we employ an automated feature that constantly detects brute force attacks on your site’s /wp-login.php path. We then block these actors from our infrastructure, further strengthening our security measures.
How we mitigated a massive DDoS attack for a financial client
Recently, a financial company decided to move to Kinsta as their new hosting provider. Little did we know, they were in the middle of a massive DDoS attack on their previous host. After going live at Kinsta, the client’s website was immediately bombarded with millions of requests from various IP addresses, causing significant disruption.
On the day of the site’s migration, everything seemed to be going smoothly before going live. We helped them with a WordPress theme issue, and they began pointing their DNS to Kinsta. However, shortly after, they noticed odd bandwidth statistics in their MyKinsta analytics and reached out to us, worried about the unusual traffic.
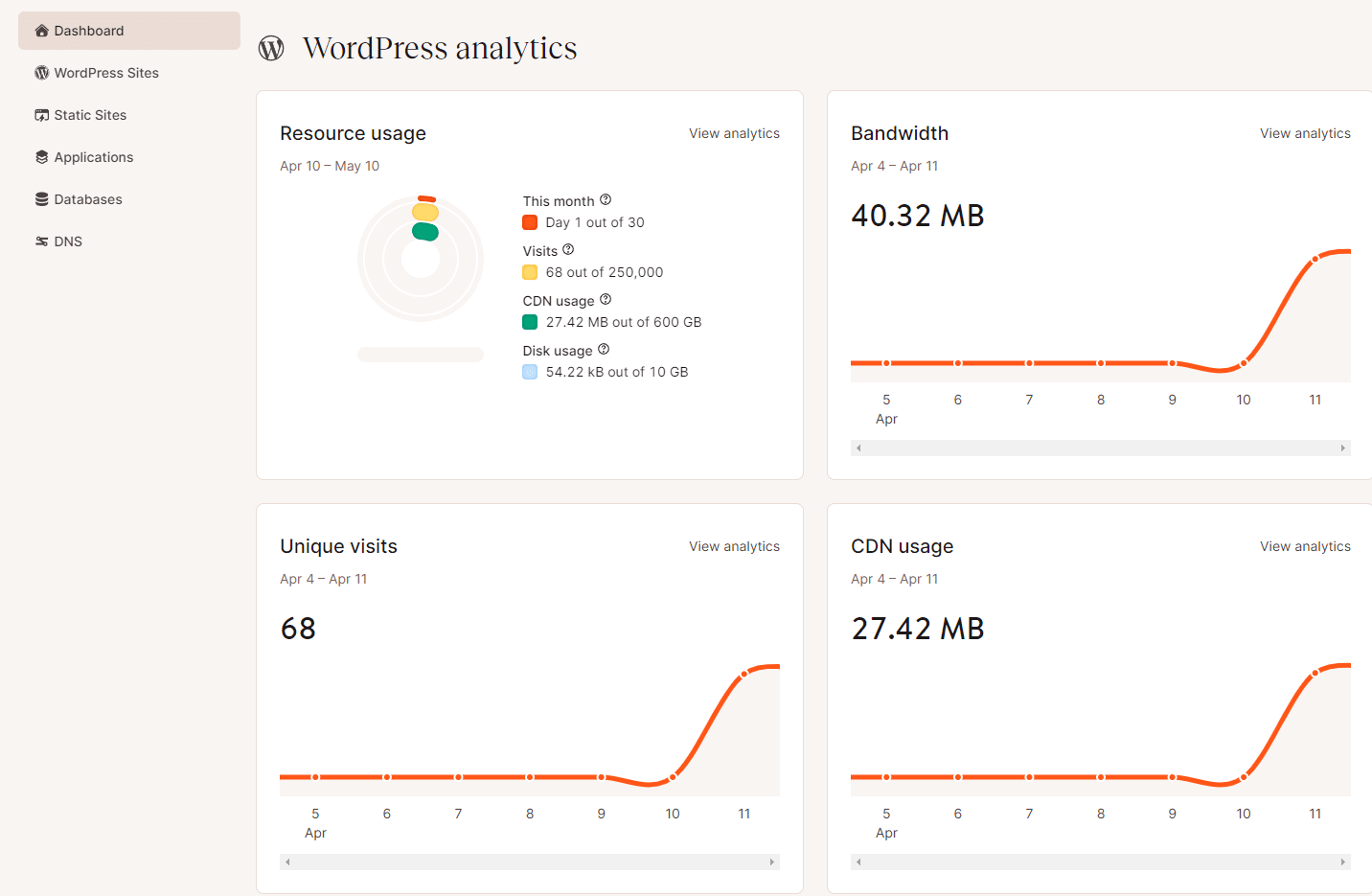
Our SysOps team quickly jumped into action, confirming that a DDoS attack was indeed happening. The client shared that they had experienced similar problems with their previous host but hadn’t realized it was due to a DDoS attack. They had hoped moving to Kinsta would solve their performance issues.
To address the situation, our SysOps team worked with Cloudflare to mitigate the attack. We implemented a custom Cloudflare WAF rule to challenge suspicious traffic and provide extra protection.
Throughout this period, the website remained accessible when tested by our support team. However, the client reported issues on mobile, which we later traced back to a DNS propagation issue caused by an old AAAA record.
By the end of the day, the attack had subsided. Cloudflare’s managed DDoS rulesets handled the bulk of the malicious traffic, automatically mitigating over 516 million requests. Our custom WAF rule provided additional security, ensuring the client’s site remained operational.
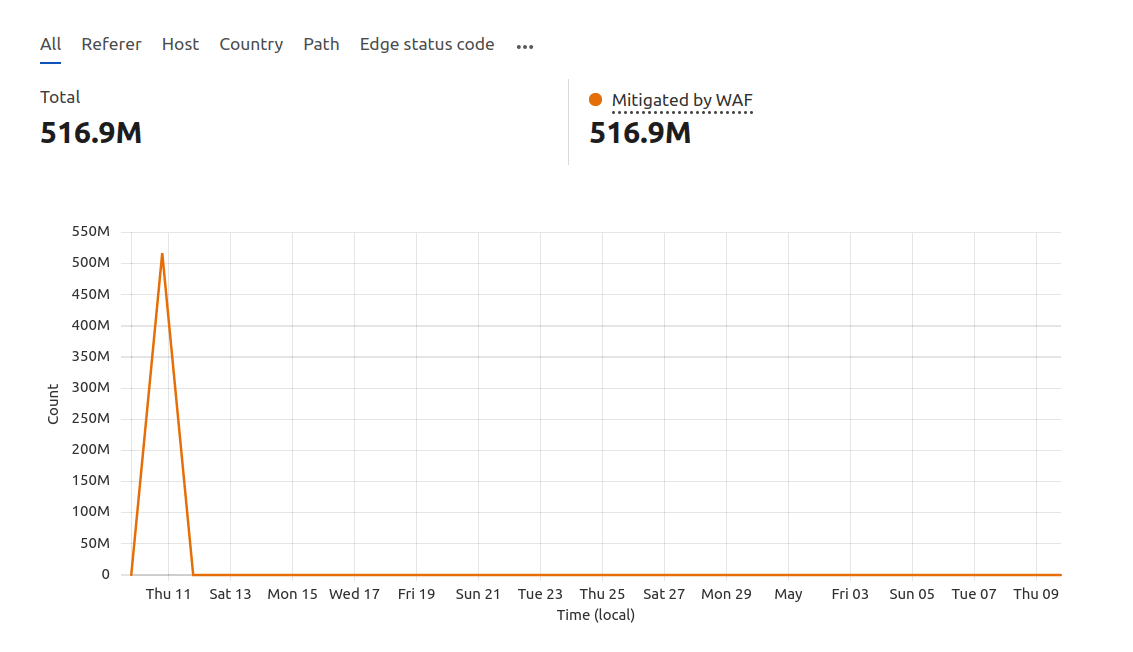
In just 27 minutes, we mitigated an attack with an average request rate of 350,000 per second. This demonstrates how an outstanding hosting provider can prevent DDoS attacks through robust monitoring, expert support, and advanced security measures.
From tracking bandwidth and analytics in the MyKinsta dashboard to engaging with support teams, having experts customize WAF rules, and leveraging a solid infrastructure, a reliable hosting provider like Kinsta can fend off most attacks and keep your site secure.
Summary
This article has explored how you and a quality web hosting company can work together to mitigate DDoS attacks, ensuring your site remains secure and operational.
Beyond DDoS attacks, Kinsta’s infrastructure offers robust protection against all forms of cyber attack. Every site on our platform runs in an isolated software container, ensuring 100% privacy and no shared software or hardware resources, even between your own sites.
How do you prevent DDoS attacks? We’d love to hear from you. Share with us in the comments section.


