Businesses can lose millions of dollars when their websites go down or are hacked.
During this time, customers struggle to get critical information and are unable to make purchases. Even worse, the business’s brand and reputation can take a hit.
Server overload is one of the top reasons websites crash. Infrastructure issues, spikes in web traffic, and hacks are some of the main causes of these overloads; hackings are prevalent all around the world.
To counteract this, businesses can implement a proxy server as a conduit to field requests, balance the load, and protect their origin servers.
This is valuable because a proxy server can act as a middleman between the initial request and the server that stores the requested file.
In this article, we’ll cover what a proxy server is and discuss different types of proxy servers in the market. Before we begin, let’s define what is a proxy server is and understand how one works.
Check Out Our Video Guide On What a Proxy Server Is Used For:
What Is a Proxy Server?
So you’re wondering, “What is a proxy?” A proxy server is a computer application that acts as a gatekeeper between a user seeking information and a server.
The server is like a castle where private information is protected and stored. The proxy is the drawbridge at the entrance of the castle, providing security and protection against threats (like DDoS attacks and more) while collecting and funneling all requests from the user in a systematic way.
To put it simply: it’s an intermediary, but its role and responsibilities are so much more than that.
Proxy servers enable sites (including personal sites, blogging platforms, and business sites) to operate more efficiently, driving down load times and protecting both the server’s security and the requester’s privacy.
Businesses implement them to protect their sites, establish a controlled employee network, and increase their firewalls against hackers.
Individuals might consider having a proxy server to add a layer of privacy or security for their online browsing. The proxy server will send the individual’s request to the site, thus shielding their private information from the final server in the process.
Although they are common, proxy servers are not required for individuals or businesses.
In fact, many businesses operate without them, and most individuals browsing the internet do not have them. But should they?
Now that you know what is a proxy, let’s discover how one works.
What Is a Proxy Server Used for?
There are many different reasons an individual or a business would consider investing in and implementing a proxy server into their tech stack. Let’s discover what is a proxy and how it can be used in a variety of ways.
Depending on your use case, you might find value in a proxy server in multiple different ways — and multiple proxies can be used as well.
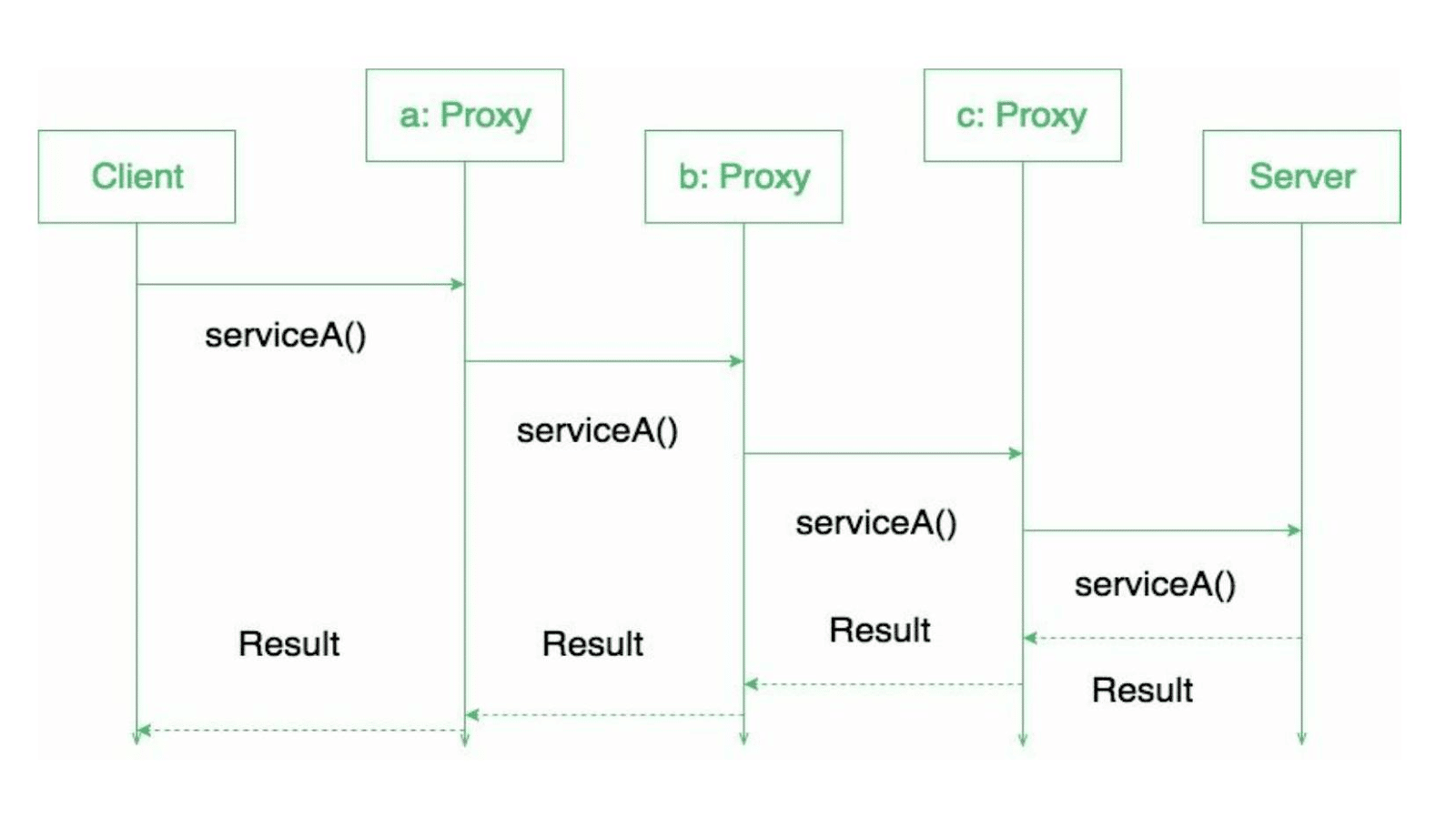
Some of the most popular usages of a proxy server include privacy, security, load balancing, increasing site speed, and more.
Let’s take a look at each one individually.
Privacy
A proxy server masks the requester’s location and ensures anonymous browsing. In a time when hacking, phishing scams, and pirated information is commonplace, it is a worthwhile benefit for businesses to implement a proxy server.
However, hackers can also use a proxy to mask their IP addresses and protect their identity. A masked IP address makes it difficult for law enforcement agencies or other specialists to find the hacker.
Generally speaking, proxies help individuals and businesses add another layer of defense from these bad actors by shielding their private information.
Security
Proxy servers can also protect businesses. A business can deploy a proxy to protect its server infrastructure. This will help ensure that their site continues to operate and that their employees’ emails, files, and communications have an additional layer of protection than if they were on a public server.
But how does a proxy server accomplish all of this?
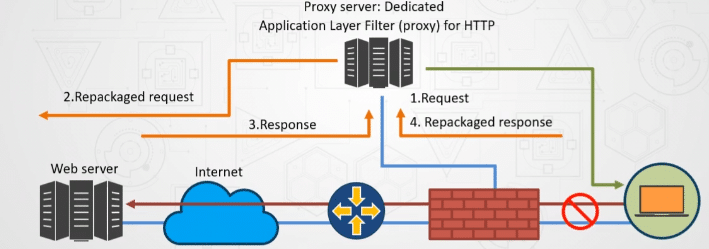
A proxy server can protect the business’ core server infrastructure that houses all their files by acting as the first line of defense and standing in between the user and the server.
If the castle is the server, the proxy could be the drawbridge or the moat. In order to get to the castle (server), the user must go through the proxy first. Thus, if damage is done to the proxy, the server will still remain unharmed.
This can be an additional shield that protects your WordPress CDN from attacks.
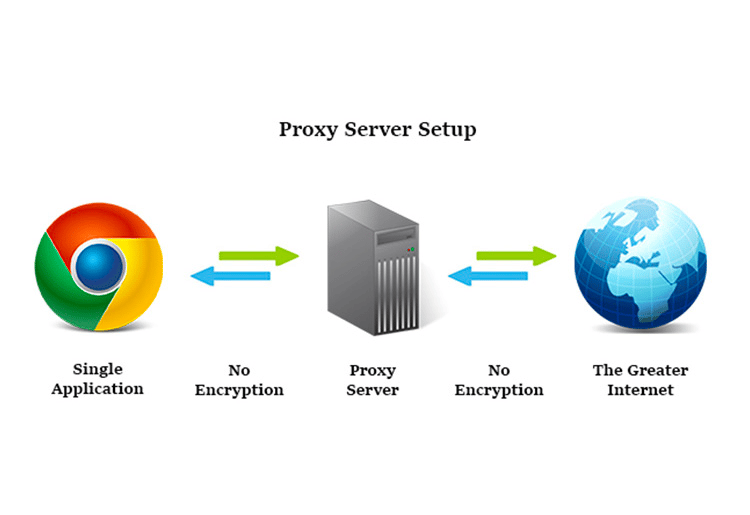
Take a look at the flowchart below:
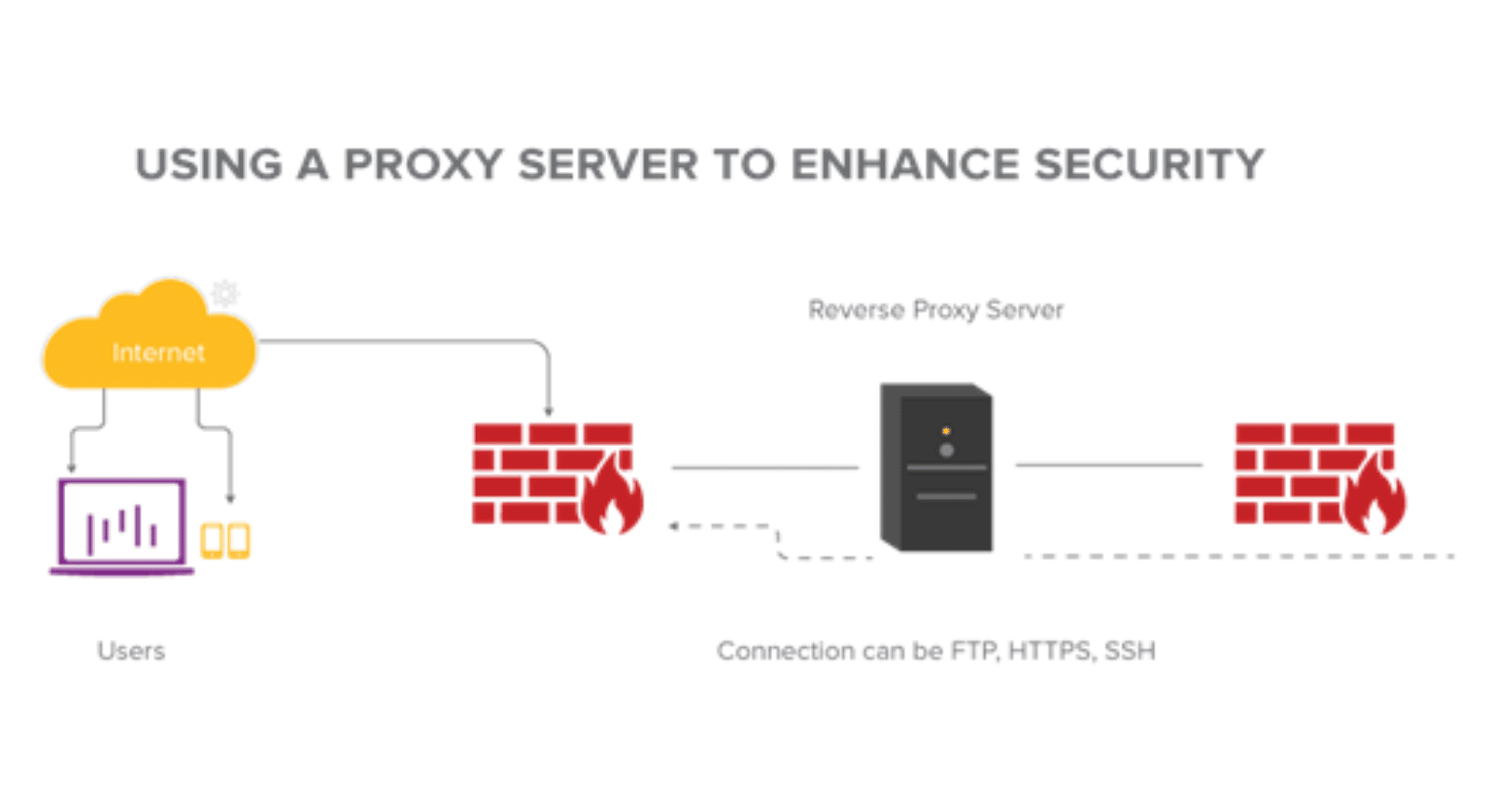
As shown above, the proxy server is isolated from both the users and the company’s server, thus adding another layer of protection for the company from direct attacks from individuals.
It’s important to note, though, that proxy servers won’t completely shield you from a hacker.
There are many ways to get around the proxy and attack a server and an organization. However, proxy servers are one of many tools businesses or organizations can use to improve security measures and counter those trying to hack their systems.
Load Balancing
Think back to all those ticket releases for major concerts featuring a global superstar. Every once in a while, one of the launches falls flat, leaving hundreds of thousands of eager fans with an error message on the site. Why?
One of the largest reasons for this is that the server is overwhelmed and ill-prepared to answer all the requests at once.
Although a proxy server won’t solve everything in the example above, it can assist with load balancing and lighten the work for the final server.
A proxy server can filter and manage requests from users before sending them to the origin server in a streamlined way.
This filtering prevents the server from being overwhelmed by all the requests at once.
Increasing Site Speeds
No one likes waiting for a website to load. For users, this can be a frustrating experience that compels them to look elsewhere.
For businesses, this damages their brand and bottom line. Consumers won’t wait for slow WordPress sites, and companies could lose money on lost sales, abandoned carts, and the absence of clicks.
Worst of all, a sluggish site will impact your ranking on search engine result pages (SERPs). Page load time is among the many factors that search engines, including Google, consider when serving websites to those inputting relevant keywords into their default search engine. (Plus, you wouldn’t want to be added to Google’s URL blocklist with a slow site.)
Therefore, it makes sense for businesses to invest time and resources ensuring their pages load as quickly as possible with the fastest site speed available. (To learn how to assess your site speed, use Google’s PageSpeed Insights or read our post about website speed tests.)
But how can a proxy help with your site speed?
Due to caching (the storing of data that leads to easy retrieval) that occurs, a proxy server can more quickly access the files being requested.
To return to the extended metaphor of the castle from above, caching would be like a historical record book that the army at the castle would use to defeat their attackers. The more logs in the record book, the easier it would be to anticipate what the attackers might do.
Caching is the storing of frequently accessed files and pages, which makes it easy for the proxy to load them quickly for the user requesting them.
This will ultimately make your site load faster since commonly requested files are requested once by the internet via the proxy and shared with multiple users simultaneously.
Although other variables, including file sizes, optimization, and network connection, can impact a site’s page load time, it is still important to consider how a proxy can help achieve better page load times as well.
Now that you know why people use proxy servers, let’s look at how one functions.
How Do Proxy Servers Work?
A step-by-step breakdown of how proxy servers work helps us understand the value that they provide. However, to understand how proxy servers work, you need to learn about the two most common types of proxy servers: forward proxies and reverse proxies.
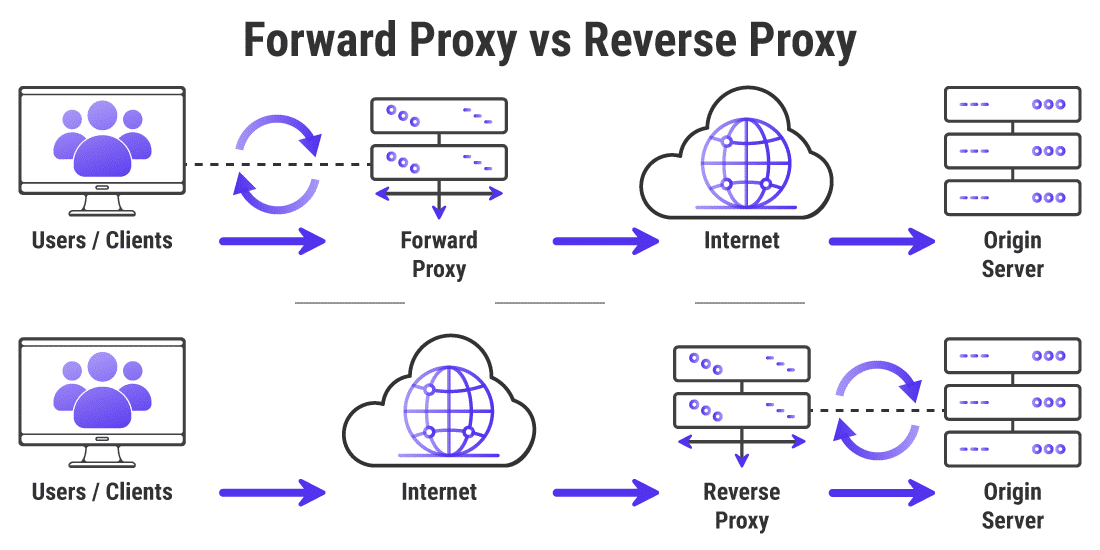
A forward proxy receives the request from a user/client and transmits it through the internet to the origin server.
A reverse proxy protects the server with added security by filtering the requests from the user/client and providing them to the origin server only to send back the file to the user/client. This prevents the user/client from ever interacting with the origin server. Kinsta provides the ability to add a reverse proxy on all of its plans.
Both function as an intermediary. They differ in where they stand when requesting a file or piece of content from a site. The forward proxy is stationed on the user’s end, while the reverse proxy is typically set up by a company to field and send back information to the user initiating the request.
By understanding how proxy servers work, you can troubleshoot yours and understand what is happening behind the scenes in real-time.
Are there more types of proxy servers other than forward and reverse proxies? Let’s look at some of the most common ones used today.
Types of Proxy Servers
There are many different types of proxy servers, so you need to understand which one is right for your use case.
Different factors, including use cases, functions, restrictions, and technical aspects, distinguish one proxy from another.
Some you should consider, others you should stay away from. Selecting the wrong type of proxy for your specific use case may not provide you with the benefits you desire.
Here are some of the types of top proxy servers in use today:
Static Proxy
This type of proxy keeps the same dedicated IP address for all requests. This is a simple, straightforward proxy that is quick and efficient.
Rotating Proxy
This type of proxy rotates IP addresses for each request.
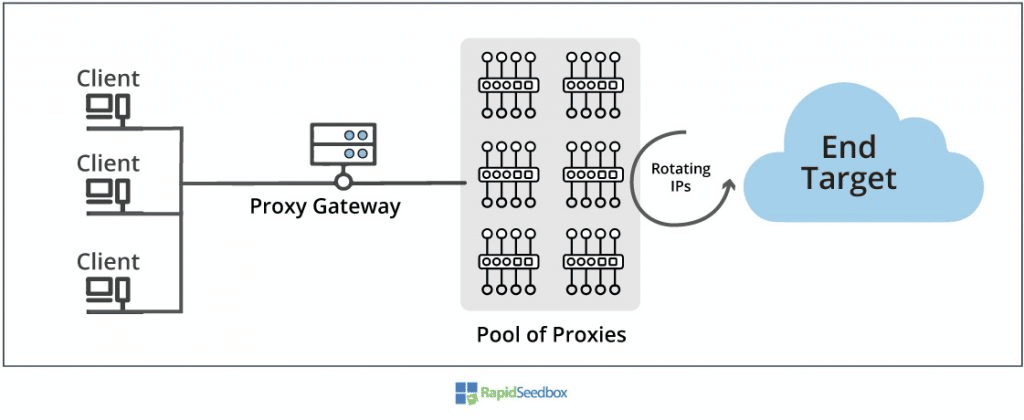
Because they rotate IP addresses, these can be much slower than static proxies.
Residential Proxy
These proxies are common and use the actual IP address of physical devices. Many use these to switch their geographical location or add an additional layer of protection.
If you’re trying to bypass a local restriction (whether it’s in place by your company or another entity), this type of proxy can help achieve that.
Data Center Proxy
These proxies do not use actual IP addresses of physical devices and instead are fake, manufactured IP addresses created in bulk.
All data center proxies may share the same IP address which can sometimes lead to banning them altogether. Be aware should you choose to use these.
Anonymous Proxy
This proxy hides your IP address and information and transmits a request to the origin server without requesting any identifying information from the original person making the request.
Dedicated Proxy
This type of proxy only allows one user to use it at a time, thus creating a private channel for that person. Some also call this a “private proxy.”
Shared Proxy
This proxy allows many people to use the proxy at the same time. Multiple clients can share the cost and use the proxy. However, with multiple requests from multiple users, this type of proxy will need a strong connection and architecture to handle the load.
Public Proxy
This type of proxy is set up in online proxy lists and can be unsafe and unreliable due to its accessible nature. Hackers can access these proxies and wreak havoc, so be careful if you plan to use one.
Transparent Proxy
This type of proxy is useful in work settings when clients don’t want anyone to know that a proxy exists. The proxy is hidden at all times for all users.
SSL Proxy
These proxies use an SSL protocol providing an added level of security and protection. SSL stands for the “Secure Sockets Layer” and is an encrypted security protocol.
HTTP Proxy
Opposite the SSL proxy is the HTTP proxy. The HTTP proxy is less secure than the SSL proxy, but it is still an option for those operating on an HTTP basis.
Not all sites and servers currently operate on the SSL protocol, making this proxy still valuable to those on HTTP.
However, what if a proxy server isn’t exactly what you need? What about a virtual private network (VPN)? How do both compare? Let’s dive in deeper to find out.
Proxy vs VPN: What’s the Difference?
Both proxies and VPNs provide consumers with an extra level of protection since they separate the requestor and the server from the files.
A VPN works similarly to a proxy:
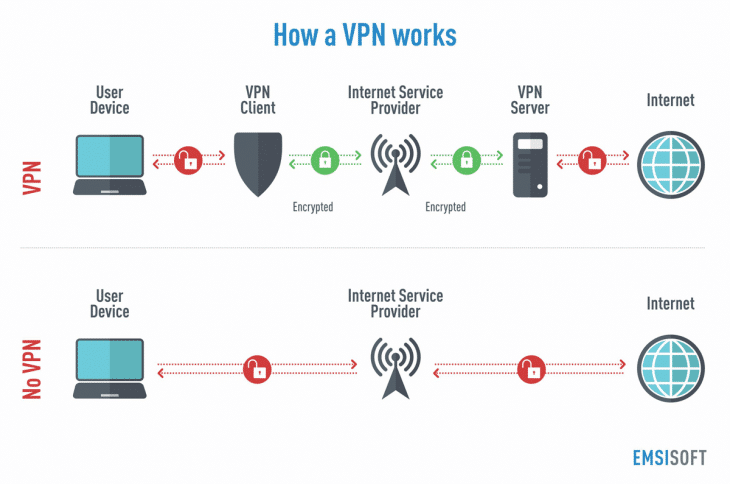
For example, a user requests a file or web application. The request is filtered through a VPN, which sends it to a VPN server via the internet. The file is retrieved and sent back in a similar way.
So then, what are the key differences between a VPN and a proxy server?
Five main differences distinguish a proxy from a VPN.
- Security: Proxies do not encrypt your connection like VPNs do.
- Privacy: VPNs offer more extensive privacy measures, while proxies act more as a go-between that simply hides your IP address from servers you visit.
- Cookies: VPNs offer additional protection against fingerprinting and digital tracking techniques.
- Cost: Reliable proxies are cheaper (about $5 per month), while VPNs typically average between $5 to $12 per month.
- Connection Speed: A public proxy server may struggle to get a single megabit per second, while VPNs can get up to 50 Mbps. If a VPN offers encryption, why would someone use a proxy? Let’s take a look at the distinct proxy benefits.
What Are the Benefits of Using a Proxy?
In addition to the variety of functions discussed above, there are many benefits of using a proxy.
Some of the most common ones include the following.
Geographic Location Masking
You can bypass regional restrictions for specific sites or media by using a proxy. This is helpful for restrictions that are set in place.
Safer Browsing
It is difficult to determine your IP address and track you digitally when all your requests are funneled through a proxy. This can be one safeguard against attacks and hackers.
Site Speed:
Due to caching, users can experience an increased level of page and resource retrieval thanks to a proxy.
Site Uptime
A proxy can collect and transmit multiple requests simultaneously to ensure that your origin server is not overwhelmed, keeping sites readily available at consumers’ fingertips.
As data and consumer privacy issues continue to rise, individual users should consider whether or not it makes sense for them to use a proxy while browsing the internet.
What Are the Risks of Using a Proxy?
Although there are plenty of benefits, there are also a few risks associated with using a proxy.
The two biggest concerns involve security and a lack of encryption.
Public proxies and other low-cost proxy servers can have security concerns that make them vulnerable to hackers and scammers. Additionally, proxies do not necessarily encrypt requests or your connection, much like a VPN does.
However, these concerns do not outweigh some of the concerns associated with not using a proxy at all.
By evaluating both the pros and cons of using a proxy, users can make the determination of whether or not it makes sense for them or their business to implement one.
Should You Use a Proxy Server?
A proxy isn’t for everyone, and there are some times when the cons will outweigh the pros.
You need to understand your motivation for why you are looking for one in the first place to make an educated decision.
You should consider using a proxy if:
- You’re interested in monitoring or controlling internet access for other users on your network.
- You’re interested in masking your IP address.
- You’re hoping to increase your speed (although there are many ways to do this).
- You’d like to bypass restrictions or blocked sites.
- You’re concerned about malware and want to add another layer of protection.
Proxies are not complicated to set up, and there are plenty of benefits to using one. If you think it makes sense for you or your business, let’s look at the step-by-step instructions to set one up on each major operating system.
How Do You Set Up a Proxy Server?
You don’t need to call the IT Team to set up a proxy on your own device. In fact, there are just a few steps for each operating system to get your proxy server running.
Once you’ve purchased your proxy server, you can begin to set it up on your device by following the steps below.
Setting Up a Proxy on a Mac
First, access your Safari web browser and select Settings > Advanced in the toolbar. A window will pop up where you can customize your proxy settings or establish a new one.
Near the Proxies row, you can select “Change Settings.”
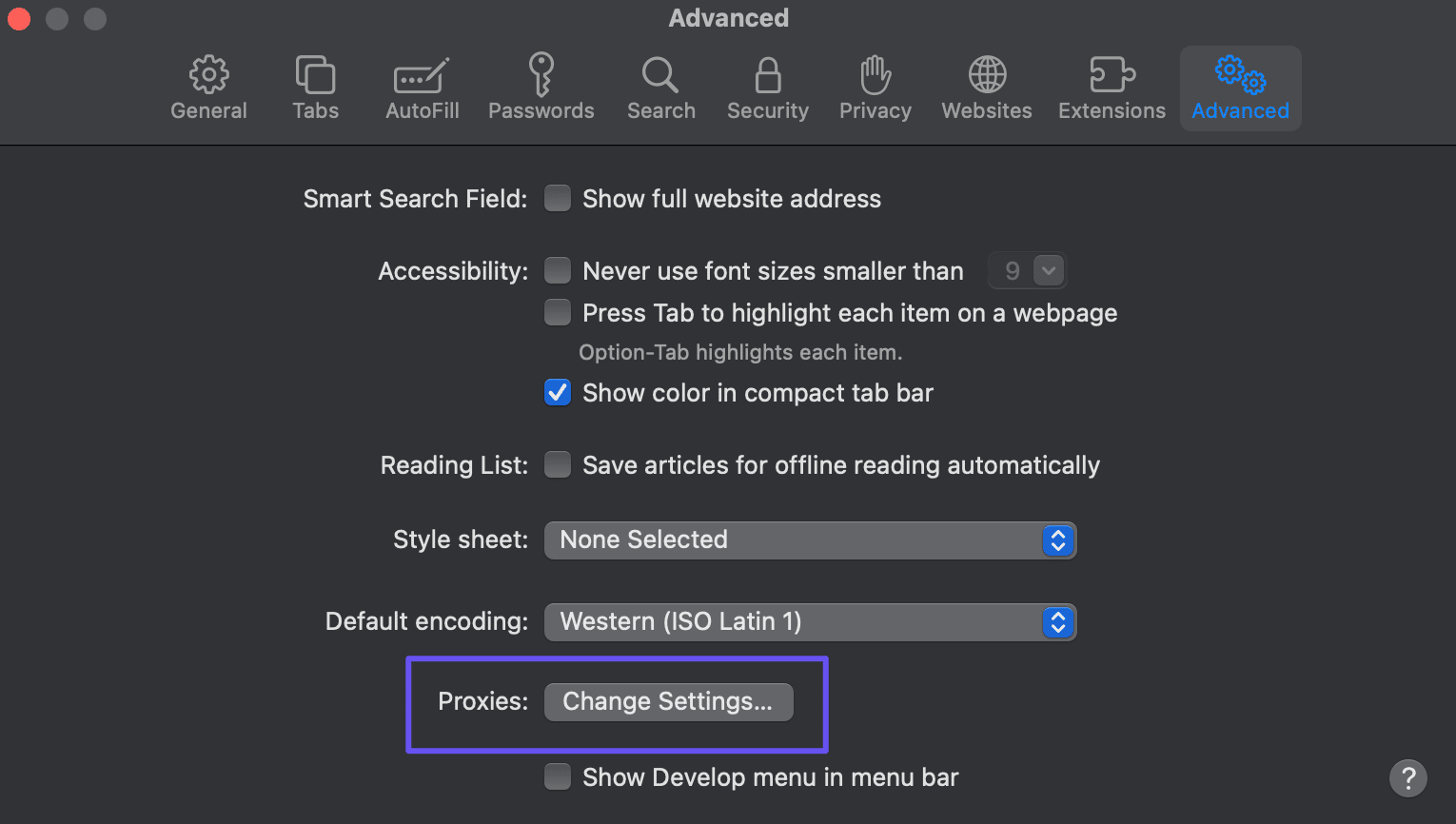
Once the change settings window pops open, you can input the correct information as it relates to your proxy and select “Okay.”
That’s it! You’re done, and your proxy is now set up and functioning.
Setting Up a Proxy on a Windows Computer
To start, select Settings > Network & Internet > Proxy in the menu tab of the Start button.
Next, look for the “automatic proxy setup” category. Activate it so it “automatically detects settings.” You can use an automatic proxy setup for the quickest and most effective way to get your proxy working.
This is a simple way to connect to your proxy and ensure the right inputs are where they need to be. Automatically detecting the settings will identify the proxy and connect on its own.
At times, a proxy server may take a few minutes to load before connecting. You can always check your proxy’s settings in the Network & Internet tab on your device. This will provide you with relevant information on whether or not your proxy is connected and functioning properly.
Summary
Now that you know what a proxy server is, you can decide if one makes sense for you.
Proxies can be an asset for both consumers and businesses. They offer added security, privacy, speed, and an added layer of protection.
By understanding how they work and the different types of proxies available, you can assess how you may improve and bolster your digital security in the years to come.
Whether you run a website, online store, application, or enterprise project, Kinsta has the tools and infrastructure to save you time and money. Join the 230,000+ companies and 55,000+ developers and entrepreneurs who switched to simpler, faster, and more reliable cloud hosting.


