WordPress is, by far, the most popular way to build a website. That popularity has the unfortunate side effect of also making WordPress sites a juicy target for malicious actors all across the world. And that might have you wondering whether WordPress is secure enough to handle those attacks.
First – some bad news: Every year, hundreds of thousands of WordPress sites get hacked, as well as ecommerce sites (that’s why we have an in-depth guide about Ecommerce Fraud Prevention).
Sounds grim, right? Well…not really, because there’s also good news:
Hackers aren’t getting in due to vulnerabilities in the latest WordPress core software. Rather, most sites get hacked from entirely preventable issues, like not keeping things updated or using insecure passwords.
As a result, answering the question of “is WordPress secure?” requires some nuance. To do that, we’re going to cover a few different angles:
- Statistics on how WordPress sites actually get hacked, so you understand where the security vulnerabilities are.
- How the WordPress core team addresses security issues, so you know who’s responsible and what they are responsible for securing.
- If WordPress is secure when you follow best practices, so you know if your website will be safe.
How WordPress sites get hacked (by the data)
Ok, you know that plenty of WordPress sites are getting hacked each year. But…how is it happening? Is it a global WordPress issue? Or does it come from those webmasters’ actions?
Here’s why most WordPress sites get hacked, according to the data that we have…
Out-of-date core software
According to a 2023 security report by Sucuri, about 39.1% of hacked CMS websites were running outdated software at the time of infection. While this statistic includes all CMS platforms, WordPress has seen substantial improvements over the years in addressing core software vulnerabilities.
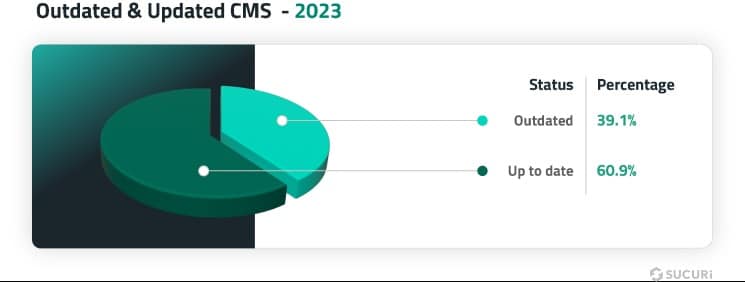
In earlier years, like 2016, Sucuri reported that 61% of WordPress hacks were due to outdated core software. To combat this, WordPress introduced automatic updates — a game-changing feature that has kept many installations up to date and reduced exploits targeting core vulnerabilities.
These efforts are paying off. The 2023 Patchstack security report recorded 5,948 new vulnerabilities, but only 0.2% were related to core WordPress — a mere 13 low-severity vulnerabilities. This demonstrates how WordPress has significantly improved its core security over time.
However, the importance of keeping software updated cannot be overstated. Despite improvements, only 49.8% of WordPress sites are running the latest version, leaving many unnecessarily vulnerable to exploits.
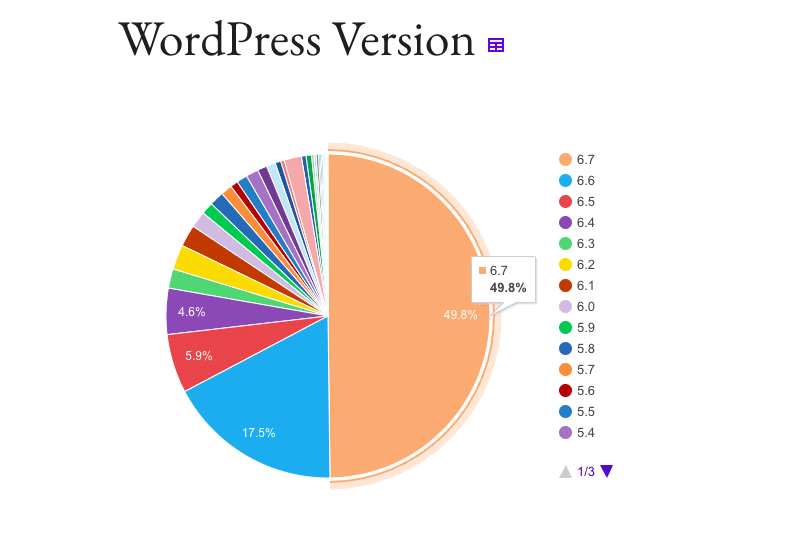
The connection between updates and security becomes clear with the infamous WordPress REST API vulnerability from February 2017. Hundreds of thousands of sites were defaced due to vulnerabilities in WordPress 4.7.1. However, WordPress 4.7.2, released weeks before the exploit occurred, had already patched those issues.
Sites that applied the update or had automatic updates enabled were safe. Those that didn’t faced the consequences.
Takeaway: The WordPress Security Team does a great job at quickly fixing issues in the WordPress core software. If you promptly apply all security updates, it’s highly unlikely that your site will experience any issues as a result of core vulnerabilities. But if you don’t, you take a risk once an exploit gets out into the wild.
2. Out-of-date plugins or themes
One of the things people love about WordPress is the dizzying array of available plugins and themes. As of this writing, there are about 60,000 in the WordPress repository and thousands of additional premium ones scattered across the web.
While all those options are great for extending your site, each extension is a new potential gateway for a malicious actor. And while most WordPress developers do a good job of following code standards and patching any updates as they become known, there are still a few potential issues:
- A plugin or theme has a vulnerability, and because there aren’t as many eyes on it as the WordPress core software, that vulnerability goes undetected.
- The developer has stopped working on the extension but people are still using it.
- The developer quickly patches the issue, but people just don’t update.
So how big is the issue?
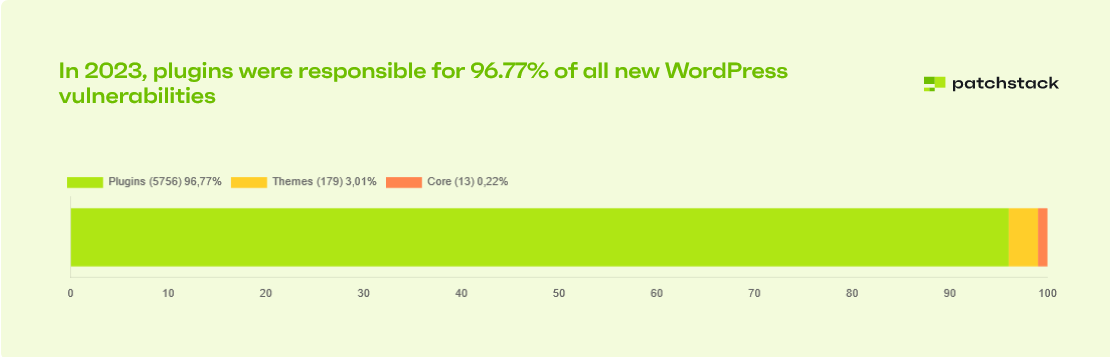
Well, in a state of WordPress security report created by Patchstack, they reported that in 2023, plugins were responsible for 96.77% of all new security vulnerabilities, while themes accounted for 3.01% of these vulnerabilities.
The most common vulnerability type was Cross-Site Scripting (XSS), which made up 53.3% of all new WordPress vulnerabilities. XSS issues often stem from plugins improperly sanitizing or escaping user input, making them an easy target for attackers.
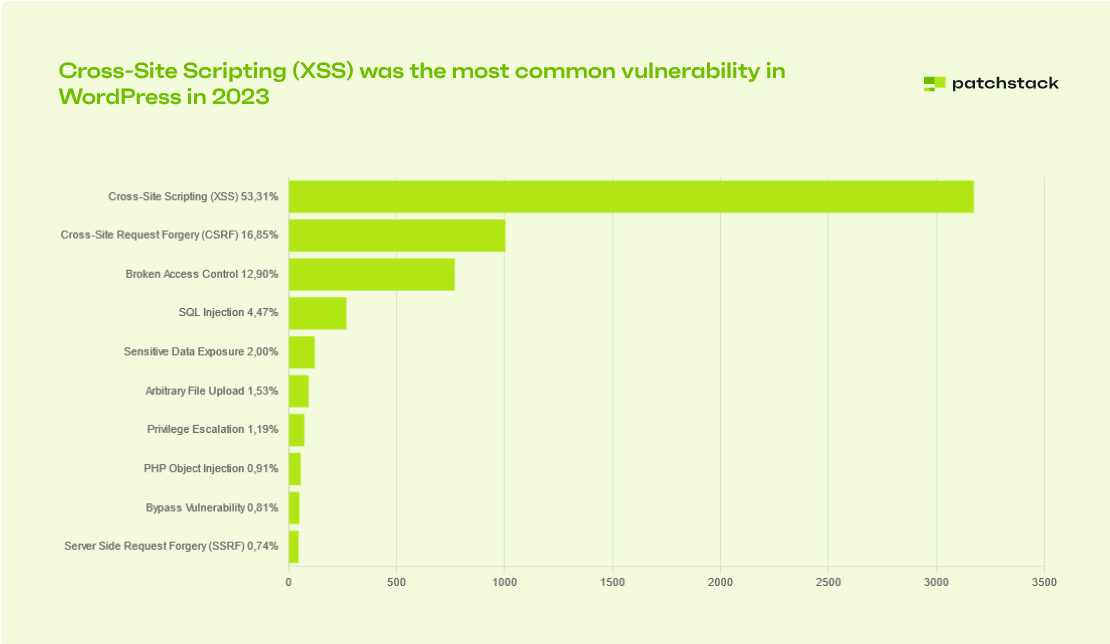
Notably, XSS vulnerabilities have become a bigger concern compared to 2022, when they accounted for 27% of vulnerabilities, trailing behind Cross-Site Request Forgery (CSRF) at 29%.
This rise can be attributed to the growing complexity of plugins and the increasing reliance on interactive features and user-generated content, which create more opportunities for input-handling mistakes.
The Patchstack report also highlighted nine popular plugins with high-severity vulnerabilities (CVSS score of 8.0 or higher, and at least 100,000 installs). Most of these vulnerabilities required no authentication to exploit, except for the WPvivid Backup and Migration plugin, which needed a Subscriber role for its privilege escalation vulnerability.
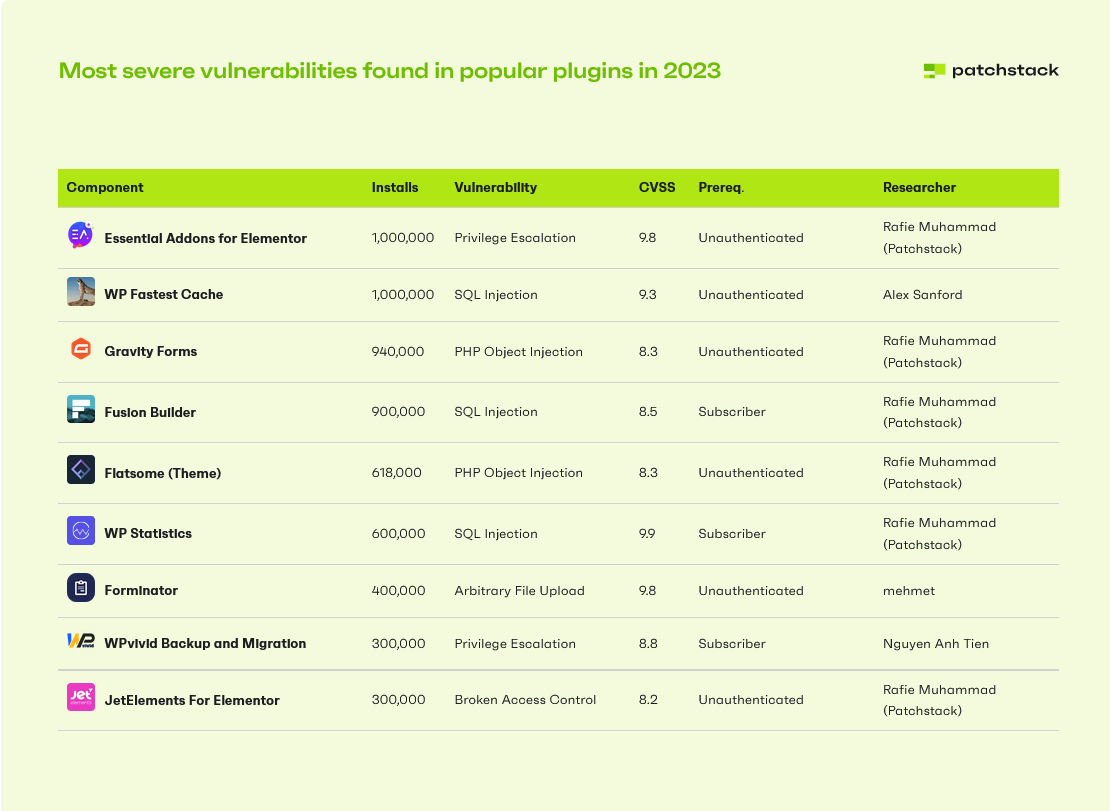
Here’s the kicker, though:
The vendors of the plugins were extremely responsive and timely in addressing and fixing the security issues — site owners just hadn’t updated the plugins to protect their sites.
Takeaway: WordPress themes and plugins introduce a wildcard and can open your site to malicious actors. Much of this risk can be mitigated by following best practices, though. Keep your extensions updated and only install extensions from reputable sources.
We also have to mention these GPL clubs you might see floating around the internet where you can get any premium WordPress plugin or theme for just a couple dollars. While WordPress is licensed under GPL, which is awesome and one reason we love it, buyer beware. These are sometimes also referred to as nulled plugins.
Buying plugins from GPL clubs mean you’re trusting a third-party to grab the latest updates from the developer and a lot of times you won’t get support. Getting plugin updates from the developer is the safest route. Also, we are all about supporting developers and their hard work!
3. Compromised login credentials for WordPress, FTP, or hosting
Ok, this one isn’t really WordPress’ fault. But a non-trivial percentage of hacks are from malicious actors getting their hands on WordPress login credentials, or the login credentials for webmasters’ hosting or FTP accounts.
In 2023, Wordfence blocked over 100 billion credential-stuffing attacks from over 74 million unique IP addresses. These attacks often succeed because of the widespread reuse of passwords leaked from data breaches.
While the chances of any individual site being compromised are low, attackers use botnets or compromised servers to launch large-scale attacks, making it challenging to trace their origins.
WordPress helps mitigate this risk by automatically generating secure passwords, but it’s ultimately up to users to:
- Use strong, unique passwords for all accounts.
- Regularly update passwords.
- Avoid reusing credentials across multiple sites.
Takeaway: Taking basic steps to keep account credentials secure can prevent malicious actors from walking right in. Use/enforce strong passwords for all WordPress accounts and limit login attempts to prevent brute force attacks (Kinsta hosting does this by default 👍).
For hosting accounts, use two-factor authentication if available and never store your FTP password in plaintext (like some FTP programs do).
If you have a choice between FTP and SFTP (SSH File Transfer Protocol), always use SFTP (learn the difference between FTP and SFTP so you can understand why). If your host only uses FTP, we recommend inquiring about SFTP support or switching to a host that supports SFTP. This ensures that no clear text passwords or file data is ever transferred. Here at Kinsta, we only support SFTP for file transfers.
4. Supply chain attacks
Recently, there have been instances where hackers gain access to sites through a sneaky trick called a supply chain attack. Essentially, the malicious actor:
- Purchase a previously high-quality plugin listed at WordPress.org
- Add a backdoor into the plugin’s code
- Wait for people to update the plugin and then inject the backdoor
For example, in June 2024, the plugin Social Warfare was injected with malicious code, along with several others, such as Blaze Widget and Contact Form 7 Multi-Step Addon. These plugins were compromised to create unauthorized admin accounts and inject SEO spam, causing serious security breaches before being delisted from the WordPress.org repository.
Wordfence has a deeper explanation if you’re interested. While these types of attacks are by no means widespread, they are harder to prevent because they result from doing something you should be doing (keeping a plugin updated).
With that being said, the WordPress.org team usually quickly spots these issues and removes the plugin from the directory.
Takeaway: This one can be hard to prevent because it’s a good thing to always update to the latest version. To help, security plugins like Wordfence can alert you when a plugin is removed from WordPress.org so that you quickly address it. And a good backup strategy can help you roll back without any permanent damage.
5. Poor hosting environment and out-of-date technology
Your hosting environment and the technologies powering your site play a critical role in its security. For instance, PHP 8.x offers significant security enhancements over earlier versions, yet only ~56% of WordPress sites are using PHP 8 or higher.
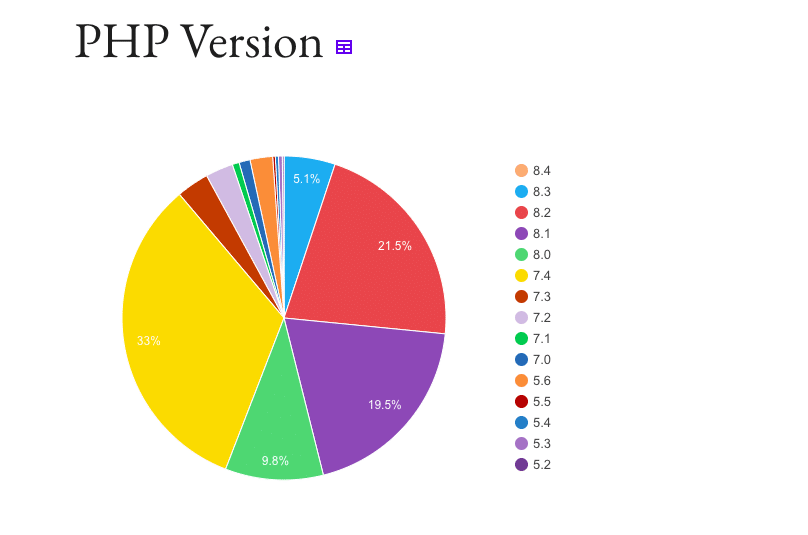
PHP 7.4 officially lost security support at the end of 2022, and earlier PHP 7 versions have been unsupported for even longer. Despite this, a substantial 33% of WordPress sites are still running PHP 7.4, and ~12% run on lower versions, leaving them vulnerable to unpatched security issues.
Switching to supported PHP versions is crucial not only for accessing the latest features and updates but also for ensuring robust security. Beyond keeping your PHP version current, choosing secure WordPress hosting can help mitigate many potential vulnerabilities automatically by providing:
- Web application firewalls like Cloudflare (all sites on Kinsta are protected by our Cloudflare integration) and Sucuri
- Automatic updates for security releases
- Two-factor authentication
- Automatic backups
Takeaway: Using a secure hosting environment and recent versions of important technologies like PHP helps further ensure that your WordPress site stays safe.
Who’s Responsible For Keeping WordPress Secure?
Now you might be wondering, who’s responsible for combating all the issues above?
Officially, that responsibility falls to the WordPress Security Team (though individual contributors and developers from around the world also play a huge role in keeping WordPress secure).
The WordPress Security Team is “50 experts including lead developers and security researchers”. About half of these experts work at Automattic. Others work in web security, and the team also consults with security researchers and hosting companies.
If you’re interested in a detailed look at how the WordPress Security Team functions, you can watch Aaron Campbell’s 48-minute talk from WordCamp Europe 2017. But in general, the WordPress Security Team:
- Detects and patches bugs and potential issues using, in part, tools like HackerOne’s bug bounties
- Consults on all WordPress core releases
The WordPress Security Team has a policy of disclosure which means that, once they’ve successfully patched the bug and released the security fix, they publicly disclose the issue (this is part of why so many sites were defaced in 2017 – they still hadn’t applied the update even after the security team publicly disclosed the bug).
What the WordPress Security Team does not do is check all the themes and plugins at WordPress.org. The themes and plugins at WordPress.org are manually reviewed by volunteers. But that review is not “a guarantee that they are free from security vulnerabilities”.
So – Is WordPress Secure If You Follow Best Practices?
If you look at all the data and facts above, you’ll see this general trend:
While no content management system is 100% secure, WordPress has a quality security apparatus in place for the core software and most of the hacks are a direct result of webmasters not following basic security best practices.
If you do things like…
- Keep your core WordPress software, plugins, and themes updated.
- Choose plugins and themes wisely and only install extensions from reputable developers/source. Beware of GPL clubs and nulled plugins/themes.
- If you have a choice between FTP and SFTP, always use SFTP.
- Use strong passwords for WordPress, as well as your hosting and SFTP accounts (and two-factor authentication if available).
- Don’t use “admin” for your username.
- Set up a firewall in front of your site. All Kinsta sites are protected by our free Cloudflare integration, which includes an enterprise-level firewall with DDoS protection built in. If you’re not hosted on Kinsta, adding Cloudflare or Sucuri’s WAF can make your site more secure.
- Keep your own computer free from viruses.
- Change your WordPress login URL to reduce brute-forcing.
- Use a TLS certificate (HTTPS) so all communication with your WordPress site (such as logging into your dashboard) is encrypted. Kinsta provides free HTTPS certificates!
- Utilize SSH keys. This provides a more secure way of logging into a server and eliminate the need for a password.
- Pick a host with a secure environment and use the latest technologies like PHP 8+.
…then WordPress is secure and your site should remain hack-free both now and in the future. If you’re a Kinsta client, you also don’t need to worry. If by an off chance your site is hacked, we’ll fix it for free!


