While it might not have been a primary concern in the early days of the web, for modern internet users, the ability to reserve the right to withhold personal information is paramount. Hacking is a big (albeit illegal) business too, and it continues to grow.
The Tor Browser is one of the best ways to keep prying eyes at bay.
However, there are lots of use cases for the Tor Browser other than keeping a hacker at arm’s length. For example, you can anonymize your IP in countries that restrict internet access, or navigate to parts of the internet that can’t be reached any other way (which is one reason law enforcement is a key user base for the browser).
This post will look into the Tor Browser and provide some comparisons to other popular solutions. By the end, you’ll have all of the information you need to decide whether Tor is right for your needs.
What Is the Tor Browser and Project?
Tor — shorthand for “The Onion Router” — is more than just a browser. The entire project covers a whole array of tools, networks, and other related services. It’s a non-profit organization that oversees the different elements in the network.

It has ties to other organizations such as the Electronic Frontier Foundation (EFF) and has received support from developers at Mozilla, producers of the open-source browser Firefox. In fact, funding for Tor comes from some sources you wouldn’t expect, such as the U.S. government and Google.
The Tor Project fulfills the role of safeguarding anonymity across the global internet. We’ll talk more about this later on, but for now, just know that the whole network helps to keep anonymous pipelines open for many different users.
While you might find some of those users come to the network in order to conceal illegal activity, there’s a subjective interpretation to this. The “dark web” fills many roles, and in situations where a user must remain anonymous in order to spread a message, the Tor network and browser can be central.
While lots of its services have come and gone, such as Tor Messenger, the browser is a mainstay. In the next section, we’ll talk more about why it’s an important mainstay to know about.
Why We’re Reviewing the Tor Browser
The history of internet privacy and security is long, convoluted, and complex. There’s now enough concern from users about information privacy for the Tor Browser to need to exist.
Leaks from whistleblowers such as Edward Snowden and Wikileaks in the 2010s shows that global web surveillance among countries is high. Initiatives and collaborations such as “Five Eyes,” PRISM, and others worry some users to the point where they may fear for their own safety, making online anonymity a primary concern.
In a nutshell, Tor enables access to the “dark web.” While the dark web gets some bad press (namely due to illegal activity), there is plenty of good too, as we’ll discuss. It exists on “darknets,” which are overlays that you need specific tools or authorization to access. The Tor Browser enables this access to the dark web, although it can also access the regular so-called visible web too.
In fact, there are many other browsers that can access the dark web. However, Tor handily beats the competition due to its array of features — so much so that some alternative browsers will even use Tor as its base.
Let’s talk more about what Tor can do.
Tor Browser’s Key Features
At its core, the Tor Browser is a “modded” version of Firefox. From there, the development team add in a few other specifics to help you access the dark web:
- TorButton. This component handles application-level security and privacy within the Firefox code base. It turns that browser into what Tor offers.
- NoScript. This is a basic JavaScript blocker, that lets Tor restrict access to scripts — hence the name.
- HTTPS Everywhere. This extension is from the EFF. It’s an organization that takes privacy seriously. HTTPS Everywhere defaults all connections to the more secure and encrypted format, rather than the more vulnerable HTTP connection.
As is typical for these types of applications, Tor is open-source and there is no premium version available. This means it’s free for everyone to download and use. There’s even a GitHub repository for those who can’t access the main Tor website.
You could also extend the platform in a similar way to Firefox, but this isn’t recommended. As you’ll discover, using a browser such as Tor is not a standard web experience.
Tor’s Development Tools
Much like its parent browser, Tor provides development tools. In fact, they are the same as Firefox, so if you have familiarity with that browser, you’ll be at home here. You’ll find them through the Tools > Browser Tools > Web Development Tools menu within the Tor toolbar:
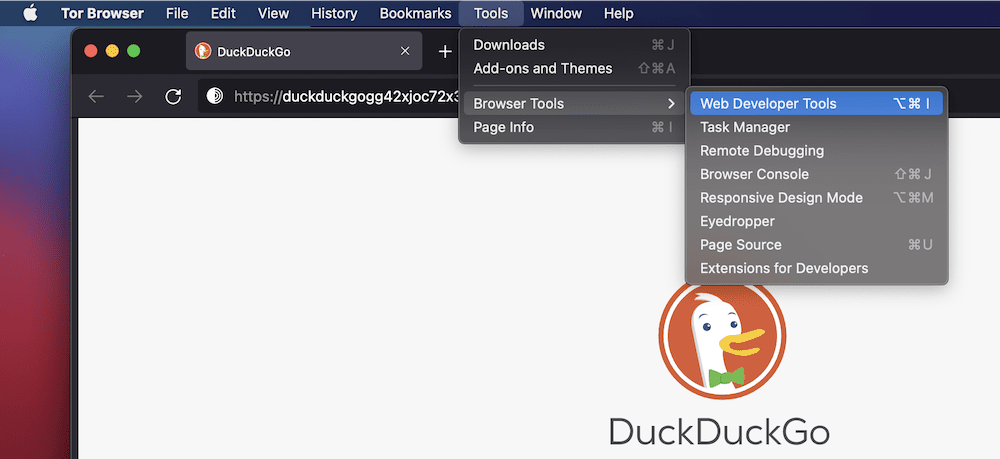
However, we wouldn’t recommend you use them. For starters, Tor’s best use case is not development work, and you’d get by much better with a solution for that with something like Firefox Developer Edition.
Tor Browser’s Focus on Anonymous Browsing
In a technical sense, Tor works just as Firefox does on the frontend. This means you get the experience of a stellar web browser that will receive regular updates and support.
However, under the hood, there is more going on.
The initial development of the Tor Browser comes from the US Navy of all places. The initial idea to protect internal, cross-government communications marries up well with the general need to protect privacy day to day. Any information you send to or from a Tor Browser has automatic encryption.
From there, data transfers across multiple relays within the Onion Router network. The data runs over three relays, each of which is part of a volunteer-led network of machines. This “homogenizes” the user base, meaning that you would only see that a user is running Tor and little else.
Security Levels
The Tor Browser lets you customize its security provision using different levels. There are three you can choose from, and each one chops off some aspect of the functionality:
- Standard: This is the default mode, where all the features and functionality are active.
- Safer. With this mode, you will have to click HTML5 media in order to play it. What’s more, you won’t be able to use JavaScript on non-encrypted sites. You’ll also find that some functionality is disabled for better security.
- Safest: Here, you’ll only be able to view static sites, with further restrictions to some usable functionality. JavaScript is disabled for all sites.
You can change these at any time based on your needs, although for most applications, the Standard tier will work fine.
The Onion Network
The Onion Network is a descriptive name for the way data packets move through encrypted messages. These messages move through several layers, much like an onion, and data travels across four different network nodes.
Each node peels away a layer of encryption, and reveals the next destination for the data. At the end of the chain, the data will present itself at its destination. What’s more, each node will only know the location of the previous and next node. This boosts anonymity and means you’ll have a high level of security regardless of where you are.
Ad Blocking and Extending the Browser
With regards to browser extensions, because Tor is based on Firefox, you can install any and all of them within the Extensions Library. However, almost none of these have support from the Tor Project.
Tor includes all of the extensions that it supports, and the warning in the documentation states that you could break functionality — or worse, compromise your security and privacy.
As for ad blocking, there is no built-in way that Tor achieves this. Some aspects of the NoScript extension will put a halt to certain ads, but this won’t stop them all.
Instead, using the security levels within Tor’s settings will be the best way to stop ads from appearing, as well as where you can adjust many other aspects of a site’s functionality.
Is It Legal To Use the Tor Browser?
For all intents and purposes, the Tor Browser is legal to download, install, and use for every user. We talk about many use cases in this post about legal ways you’d use the functionality Tor offers.
However, it’s also true that many illegal activities take place using Tor — specifically on the dark web. In the US, at least, Tor is legal to use. For some countries that commonly suppress information, such as China or Russia, Tor can’t be used legally.
That said, even in the US, law enforcement tries to shut down certain users — so there is definite pushback at a government level with regards to Tor usage, particularly as it grants greater anonymity.
Drawbacks of Using Tor
As with most things, Tor has both positives and negatives. We’d suggest that it’s the best way to browse the web in an anonymous way, but it’s not a foolproof solution. In fact, the browser can’t prevent end-to-end “correlation.” This is where you can pinpoint the source of a malicious hacking attempt through multiple data points.
What’s more, in certain uncommon scenarios, you may still be exposed to vulnerabilities:
- Some websites can sense that you use Tor and block your access as a result.
- It’s possible for a bad actor to grab a fingerprint of your mouse movements, then use that to further establish your identity.
- Much like a typical Direct Denial of Service (DDoS) attack, a malicious user can overwhelm Tor’s “exit nodes.” In short, these are the end point of the network chain, and it’s what you’ll see when you view a site on the dark web. In some cases, this “sniper attack” can also send you through an exit node that the attacker controls.
So, Tor isn’t a failsafe solution for anonymous browsing. Despite this, Tor is still widely considered the safest and most secure way to browse the dark web.
Using a Virtual Private Network (VPN) With the Tor Browser
While the Tor Browser is legal to use, it does instill fear in some businesses, companies, and agencies because of what it allows users to do. It’s even possible that your Internet Service Provider (ISP) could punish you for using it under their specific terms of service.
To mitigate this, you can use Tor in combination with a Virtual Private Network (VPN). This will obfuscate your location enough that you’ll be able to use Tor with relative anonymity.
There are two ways you can combine the two tools:
- You can run your VPN first, then open Tor within it; or
- You can open Tor first, then connect your VPN.
They sound like the same process, but there are some fundamental differences that bring up some positives and negatives for each.
In most cases, you’ll want to connect your VPN before you run Tor because this way you can access dedicated “Onion” sites.
However, note that either option will expose your browsing information to a third-party. This could be the VPN provider, your ISP, or both. It’s another facet you’ll need to weigh up in order to make the best decision for your privacy needs.
Tor’s Speed and Performance
The focus of the Tor Browser is on security, anonymity, and user safety. None of these involve a focus on speed.
In short, the performance of the Tor Browser with regards to speed is poor (in other words, it’s too slow for the average web surfer). This is important to understand this when considering using Tor because the speed deficit could negatively impact your experience.
Due to the nature of using relays to connect to the web and how this set of connections is almost random every time, you can’t pin down specifics relating to benchmarks. For example, security blog Cloudwards’ own benchmarks show the Tor Browser be uncompetitive compared to other browsers. In fact, it doesn’t score anything at all in a couple of tests.
However, if you look at a site such as HTML5test, you can see that Firefox — the parent browser in this case — performs well.
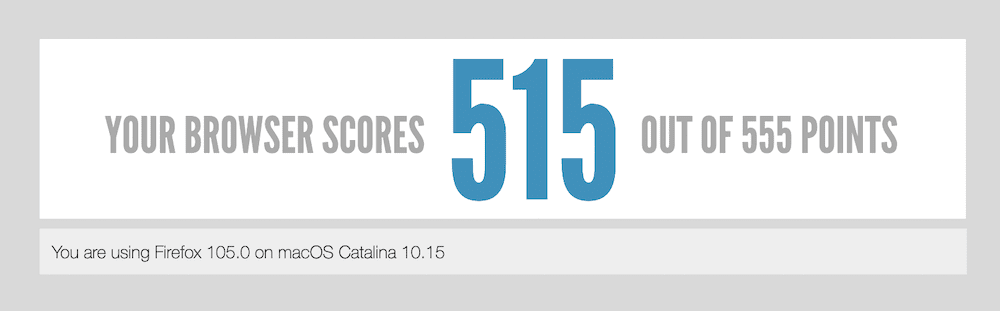
Remember, though, the Tor Browser has greater levels of security and uses a completely different way of accessing the web. What’s more, conducting benchmark tests is not going to give you a real-world view of your own experience of how Tor performs.
How Tor Compares To Other Browsers
In the next few sections, we’re going to look at how Tor compares to other popular browsers. However, this shouldn’t be your primary way to decide whether the Tor Browser is for you. Most commercial web browsers don’t have privacy and security as a primary, marquee feature (although it will be given due attention).
Let’s start with a solution that is in many ways diametrically opposed to the Tor Browser: Google Chrome.
Tor Browser vs Google Chrome
You’ll likely already know about Google Chrome. It has a market share that’s unmatched in its field, which you’d expect given that it’s backed by the search giant, Google.

You can get this browser on almost all devices, and it will even come standard on some phones, such as the Google Pixel.
In fact, you could say that it sets the standard for browsers, especially with regards to the technology it brings to the table:
- It gives you a combined search bar and address bar that can also pick out files and documents from other Google services.
- Speaking of which, there is deep integration with Google Workspace on tap, with document and account sync built in.
- There’s a built-in password manager that stores your credentials in the cloud.
- You also get a huge extension library to tailor your experience to your needs.
It might seem odd to compare Google Chrome to Tor here, but this is worth pointing out: Chrome — and Google itself — are at the forefront of sharing information. Even a cursory search will bring up the company’s practices relating to data harvesting. There have been numerous lawsuits in the past directed at the objectively shady way Google handles data.
In contrast, Tor is so locked down that it can’t compete with any browser on performance. However, this is exactly why it will be of a huge benefit to you if you want to protect your identity and information.
We can’t say that Tor is better than Chrome across the board because the two browsers have different goals. However, you won’t want to use Google Chrome at all if you need to stay anonymous.
Tor Browser vs Brave
The Brave browser is one we cover elsewhere on the Kinsta blog, and it looks to combine a popular core feature set with further privacy and security features that include ad blocking as standard.

The browser’s founders include the inventor of JavaScript and the co-founder of Mozilla (i.e. the Firefox developers.) However, Brave builds on top of Google Chrome rather than Firefox. Here’s what it will offer in addition to the Chrome experience:
- There’s a unique feature that lets you earn cryptocurrency for using the browser. You’ll collect it, and can send it to other content creators.
- Brave builds on the development version of Google Chrome — Chromium. As such, you can add the same extensions as you’ll find in the Chrome Web Store.
- Given the focus on blocking ads and protecting the user, Brave also includes dedicated functionality for this. There’s a password manager, you can control cookies, media autoplay, and more on a per-site basis.
This last point is where we can compare Brave to Tor. In fact, Brave’s private browsing windows use the functionality as the Tor Browser to anonymize your fingerprint. This is a great step, but Brave does have some drawbacks.
For example, you earn cryptocurrency through viewing ads, which is in stark contrast to the fundamental reason to use Brave. This also means you’ll be subject to tracking in order to tally up your ad views.
For a general browsing experience, we’d say Brave is one of the better options, especially given the speed advantage over Tor. The private browsing option is also welcome. However, for security and privacy, Brave might not do enough, and its general feature set contradicts its main goals on a regular basis.
Tor Browser vs Chromium
If you use Brave, Google Chrome, Microsoft Edge, and many other similar browsers, you’ll find they all use Chromium as a base. This is the development and open-source version of these browsers, but this doesn’t always give you bleeding edge functionality.

If you compare Chromium to other browsers that build upon it, you’ll find an anemic feature set. This is because it’s not for public consumption, although some do use it. However, we’d recommend you choose practically any other browser for the following reasons:
- Chromium is essentially a “beta” version of a browser. There’s no install manager, so you’ll need to “compile” the software before you can use it.
- The current version of the browser — all versions, in fact — will only offer nightly builds. This is the “end-of-the-day” version of the browser the developers will upload, which means it could have bugs, errors, or vulnerabilities.
Chromium’s focus is on learning how to develop a web browser, not on privacy or security. We’d argue that using Chromium will offer you the least protection for all the reasons we mention.
Because of this, Tor is a much better bet for your security and privacy.
Tor Browser vs Mozilla Firefox
Among users and developers alike, Firefox is a standout. It holds its ground as a champion of open-source fundamentals, privacy, security, and much more.
Here’s what Firefox will offer you with regards to a secure browsing experience:
- There’s a full-featured private browsing mode, on par with most other browsers.
- Firefox will block a number of web elements by default. This includes cryptomining scripts, social trackers, and third-party tracking cookies.
- Firefox comes with a native password manager to help store every set of credentials you use.
- Firefox will block media that attempts to autoplay, giving you the choice to play it or not.
- The browser also offers an extension library, so you can add HTTPS connections by default, integrate an ad blocker, and more.
When you compare Firefox to Tor, you also have to consider where it sits when you compare it to other browsers. For a core level of privacy and security, we’d choose Firefox over any Chromium-based browser, especially Chrome.
However, Tor does offer much better security and privacy with a side-by-side comparison. This is understandable based on what each browser offers.
We’d say that if you have concerns about day-to-day privacy but still desire a snappy browsing experience, Firefox will fit the bill.
Tor Browser vs Apple Safari
For Apple users, Safari is the default and performs well on all its devices. It’s popular as a “set and forget” type of browser.
However, it might not be the best if you value your privacy and security.
On the whole, Safari is a functional browser that integrates in the best way with other Apple products. This is an advantage for most users and means the primary goal of the browser is met.
However, Safari doesn’t offer some of the elements we’d expect from a secure and private browser:
- There’s no autoplay blocking functionality, which means you’ll need to find an extension (if one exists).
- Safari doesn’t block cryptomining scripts. This might not affect you too much, but it’s nice to know a browser has your back on all sorts of malicious actions.
- Apple is behind when it comes to implementing security functionality into its browser; as such, Safari has a sparse set of options to help protect you. That said, you can still block all cookies, stop sites tracking whether you use Apple Pay, and prevent cross-site tracking too.
- Apple Safari is a proprietary piece of software. This means the code base is not available to look at. While this isn’t necessarily a problem, open-source software has lots more eyes on the core code, meaning developers can contribute to fix bugs and errors faster.
The Tor Browser is also open-source and includes everything Apple Safari lacks. Again, performance is an issue, but the overall goals of both browsers are different.
We wouldn’t say Tor is an “everyday” browser, but it will certainly protect you better than Safari if you need to browser as an anonymous user.
How To Install and Use the Tor Browser
As with any app, you’ll first need to download and install the Tor Browser on your computer. There’s an official page to do this on the Tor Project website.
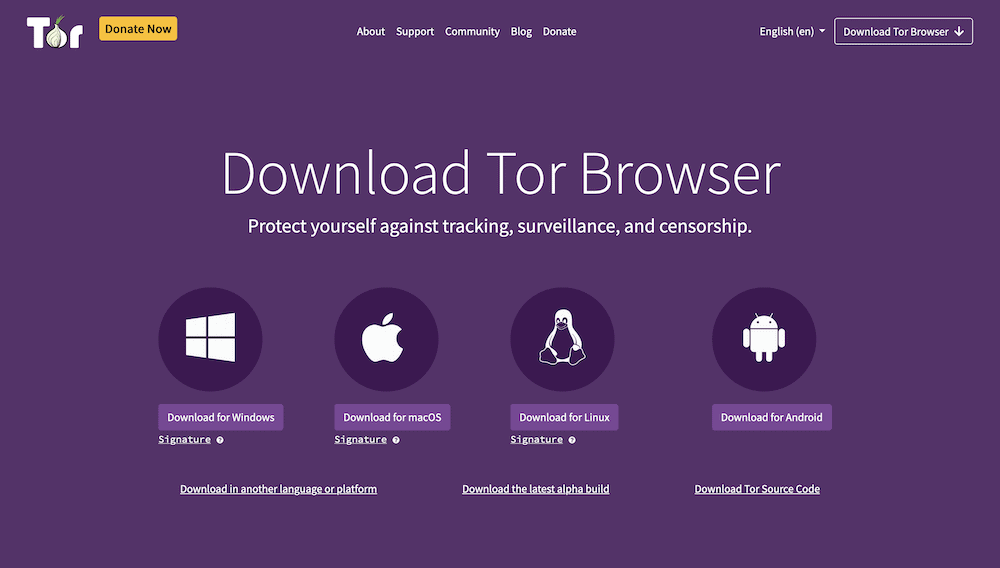
The initial process is as straightforward as any other installation: Download the package, extract it, and go through the remaining installation steps for your operating system (OS).
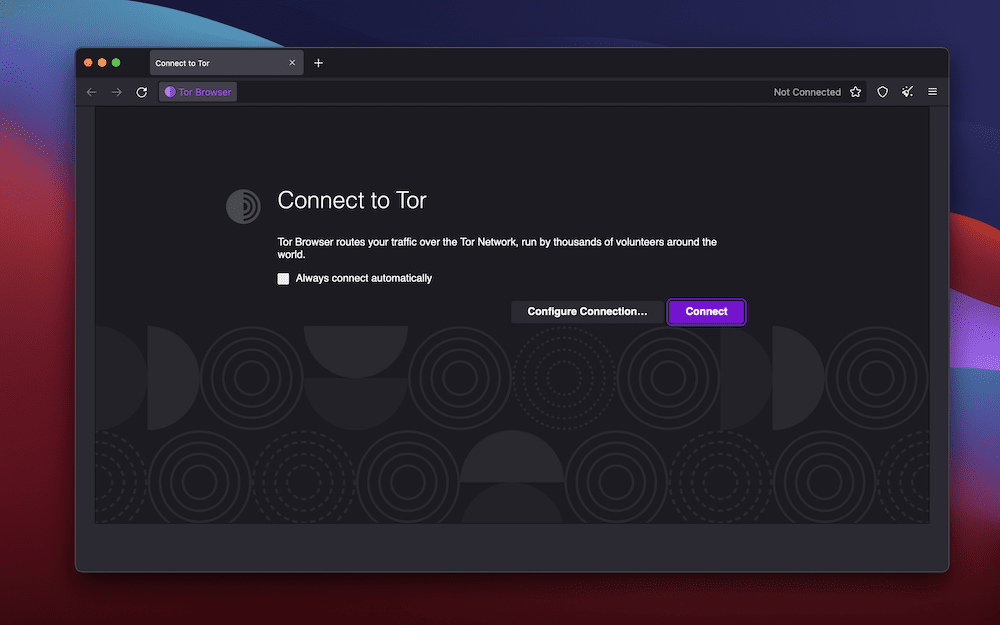
Once you complete this step, you can open the Tor Browser as you would any other application. Doing so will bring up a blank window, complete with buttons to configure your client and connect to the network:
If you click the Connect button, you’ll see the browser look to establish a connection to the Tor Network:
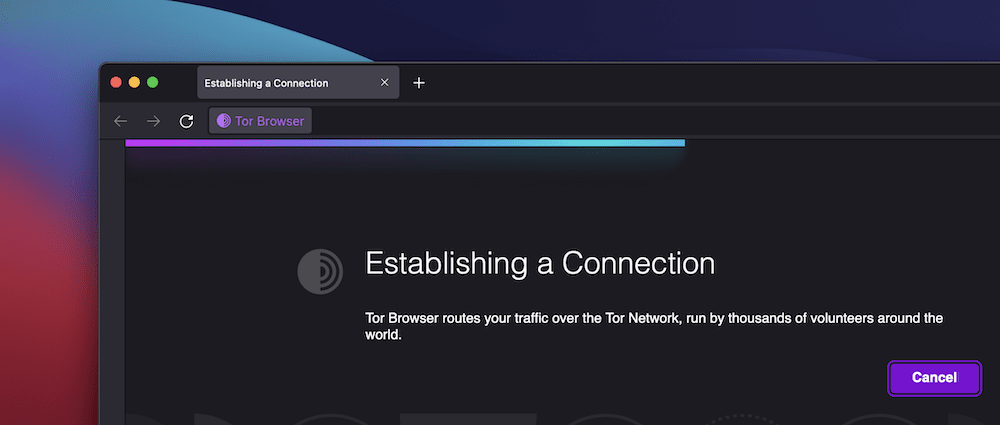
This could take a while depending on various different factors. In general, the Tor experience is slower than average for the reasons we outlined earlier.
Once you do connect, you’ll come to a start screen:
From here, you can begin to browse the web, either using a dedicated URL with the .onion TLD, or the DuckDuckGo search bar.
Without a mirror link for the site you want to view, Tor is much like any other browser, albeit a painfully slow one that is missing some “quality of life” features (which we’ll discuss later on):
However, you can also use an onboarding wizard if this is your first time with Tor.
You can find the link to this wizard in the top-left corner of the start screen. This will bring up a checklist to help you learn to navigate your new browser.

Each panel will tell you more about Tor, but in some cases will also give you access to other configuration screens to make changes:
In fact, there are a few ways to access these settings, which we’ll go into next.
Adjusting the Tor Browser’s Settings
If you need to configure the Tor Browser, you can do so in a few ways. The typical Tor Browser > Preferences link in the toolbar is one method:
However, you can also find the settings using the Onboarding Wizard too:
Regardless, the Connection tab within the Preferences screen will let you change things up if you need to:
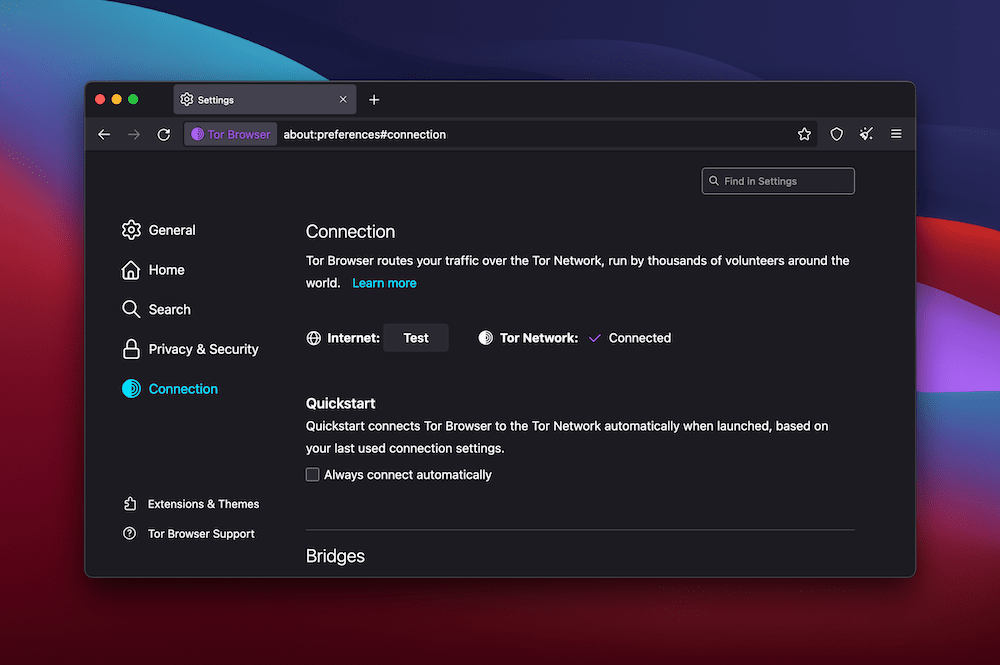
Changing these settings is beyond the scope of this article, but there’s a lot you can do here. For instance, you can test your connection, set up a quick start feature, adjust your proxy settings, and more.
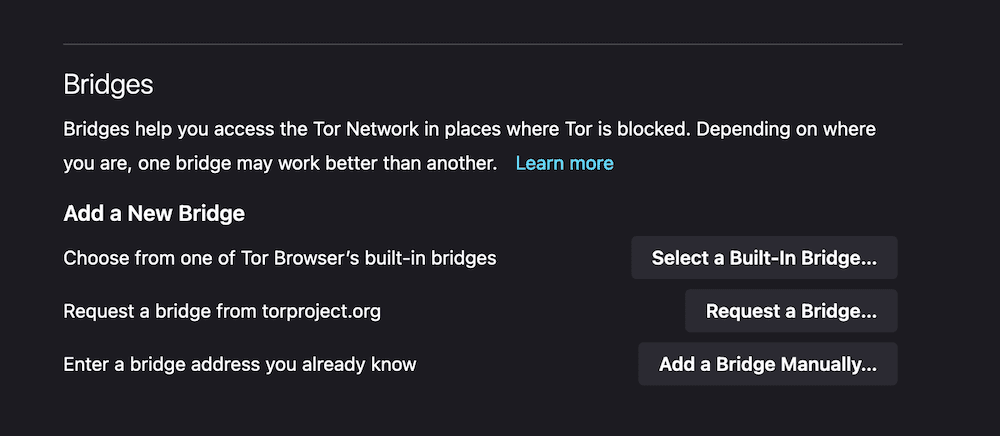
There’s also access to “bridges.” These are ways to connect to Tor where it might otherwise be blocked. If you already know of a bridge, you can enter it in the Bridges section, or you can request one from the Tor Project itself:
Other than this, you’ll want to check over your security settings from the icon in the browser’s toolbar:
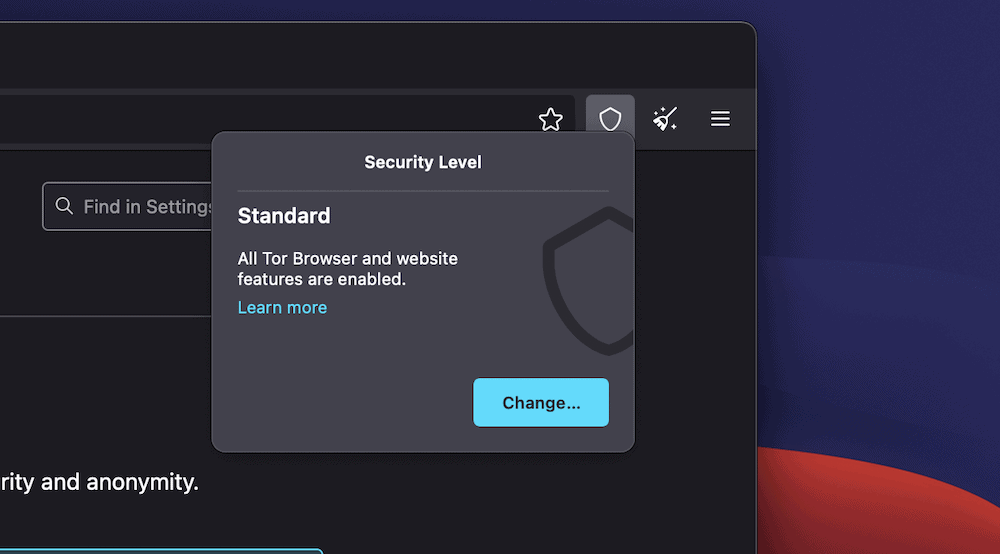
The Change button here will take you to the Privacy and Security section of the Preferences page. This gives you a way to alter your security settings for your specific purpose:
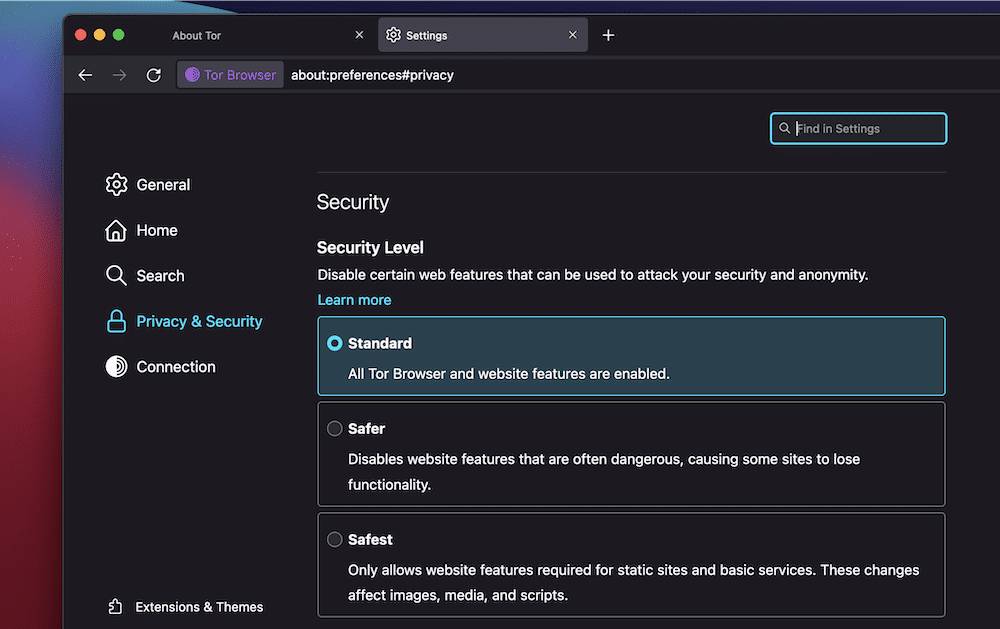
Once you look over the settings and set everything up to your specifications, you’re free to browse the Onion Network.
Summary
There are different levels of privacy and security you can take with regards to your web safety. While most commercial browsers such as Chrome, Firefox, and Safari offer varying degrees of options that relate to privacy and security, none can offer the full set of features you need to traverse the dark web.
In this Tor Browser review, you learned almost everything you need relating to how you can access that dark web and whether this option is a good one for your purposes.
In our opinion, Tor is the best way to get onto the dark web. Other browsers simply don’t have the functionality or backing to keep up yet.
Do you have anything to add to our Tor Browser review? Let us know your thoughts in the comments section below!


