It’s no small surprise that security has become a significant concern for web developers and site owners. As the internet exploded in popularity and became the new go-to method of communication, research, and shopping, website security checks are critical to thwarting the spread of malware and spam.
Whether you run a tiny personal blog or a huge multinational online store, the threat of getting hacked is always present. Some people will deface your site and embed malware in it, attempt to steal your or your customers’ data, and delete important content on your server. You need to protect yourself and your sensitive information.
Let’s figure out exactly how secure your site is right now. We’ll also offer a few tips on removing the low-hanging fruit malware authors take advantage of. WordPress is secure out of the box, but it takes a little work to patch it up entirely.
Check Out Our Video Guide to Carrying Out a Website Security Check
Website Security Check: Why Does It Matter?
You might think that your website is so small and unimportant that no one would bother targeting it. Or maybe you’ve just never thought about security before and figure it doesn’t matter enough to bother with.
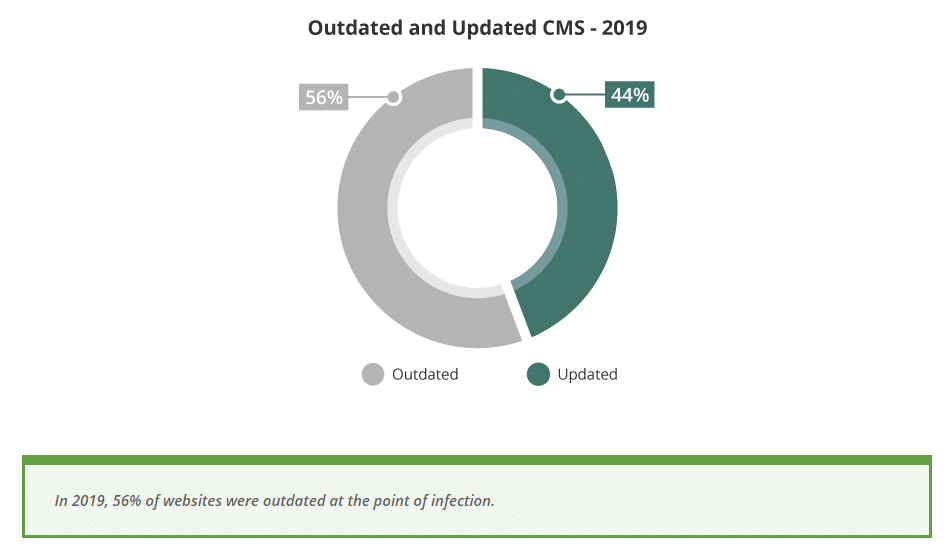
Thinking like that is why, in 2013, more than 70% of WordPress installations were vulnerable to attacks. Many of these attacks were due to outdated software — because most people either don’t know enough or don’t care enough to secure their sites, which led to a massive wave of hackers targeting WordPress installations.
So what could happen if your site experiences an unwanted intrusion? It’s not just a simple annoyance easily solved by changing your password.
- Your site could have code injected into it that causes visitors to infect themselves with malware, which could be extremely difficult to locate and remove.
- Your critical pages may be defaced, blanked, or stuffed with links to illegal sites.
- It can result in the deletion of content like blog posts and pages.
- Sensitive info such as login or credit card info belonging to you, your users, or your customers may be stolen and sold online.
- Attacks could spread to other websites on your server.
- If Google detects any malware on your site, it will block its access and remove it from search results, destroying your search engine optimization (SEO) efforts.
- The admin account’s username and password could be changed, preventing you from accessing your backend at all.
Hacked sites can be a huge deal if you run an ecommerce store.
And while you may say that your site doesn’t matter enough, not all attacks are targeted. Many WordPress attacks are automated — a bot probes your site for vulnerabilities and initiates an attack without human intervention.
That’s why you need to take steps to secure your site, no matter what.
Why Does WordPress Get Hacked?
Hacking is widespread, but what are the most common vulnerabilities hackers leverage to break into your site?
You may imagine that getting into a website is a challenging process that requires days or weeks of work and vast knowledge about computers, coding, and servers. This situation could be true for targeted attempts to break past the defenses of a large, well-protected site, but the story is very different when it comes to small WordPress domains.
The vast majority of attacks on WordPress are successful due to people using easy-to-guess passwords and not updating their themes and plugins. Hackers break into most such sites using automated programs.
Password-cracking is the simplest form of hacking possible, but it’s so common because it works. Many people leave their WordPress login on the default “admin,” taking out half the guesswork, and then use a simple, guessable password besides.
When that fails, hackers will leverage common vulnerabilities in popular plugins or outdated versions of WordPress. That’s why it’s so important to keep everything updated.
There are many more complicated, complex ways to break into a website. Still, most WordPress attacks make use of the low-hanging fruit of an insecure password and outdated software that makes it extremely easy to get into a site.
How to Perform a Website Security Check
The first step of securing your website: determining how secure your website already is. Are there any glaring vulnerabilities in your backend that you need to patch immediately, or any easy fixes you can make now?
Use an Online Tool
One quick and easy way to check your site for malware and vulnerabilities is to use an online scanner. These remotely scan your site and identify common issues. It’s super convenient since it doesn’t require any software or plugins and only takes a few seconds.
There are dozens of scanners to choose from online, and we’ll list a few others in our tools section below, but for now, let’s pick a popular one that’s easy to use: Sucuri SiteCheck.
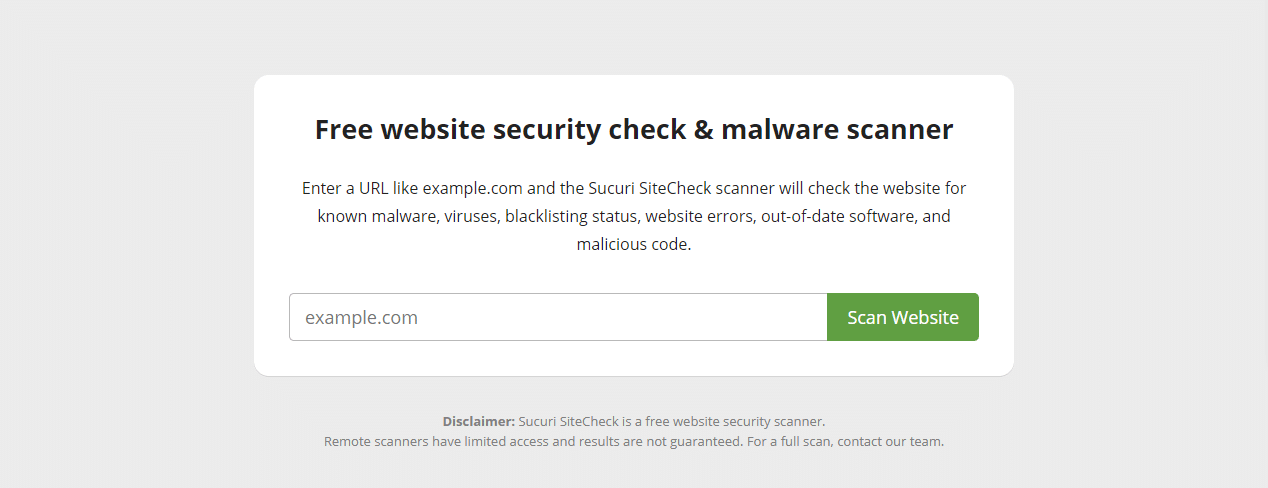
This tool is a good choice since you can install the Sucuri plugin and get right to fixing any issues it detects.
Once you scan your site, Sucuri will check it against blocklists, look for obvious issues like injected spam or out-of-date software, and briefly scan any code it can access for malware. It also offers some suggestions to harden your site against attacks.
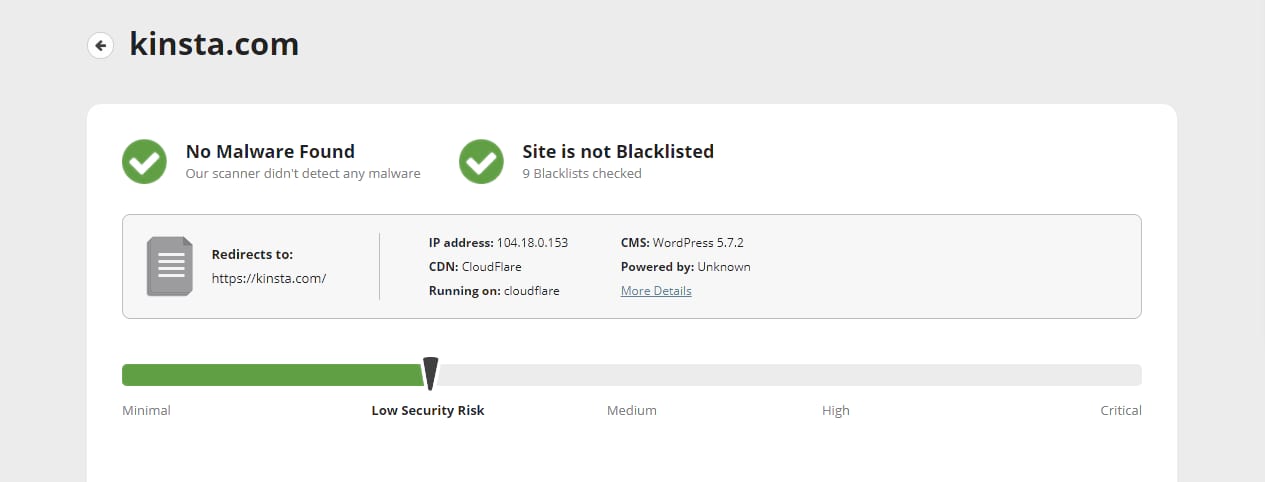
Tools like this are a great launching point for detecting hidden malware and other issues.
Scan Your Website With a WordPress Plugin
While online scanners work well enough, it’s even better to install a plugin that’s capable of digging deep into the root of your code and fishing out vulnerabilities or hard-to-detect malware.
We’ve already mentioned Sucuri as an option. There are also two even more popular security plugins: All in One WP Security & Firewall, and the most downloaded on the repository, Wordfence Security.
Once you’ve installed your plugin of choice, it will likely instruct you to run a scan immediately. The upside of these plugins over remote scanners is that they can remove malware and make changes automatically.
Look for Strange Changes
If you suspect or know that your site has been infected with malware, pinpointing the source can sometimes be challenging. Here are a few unexplained changes you may notice, as well as the files hackers are typically attracted to:
- Sudden links to strange websites you didn’t add yourself
- New articles and pages you didn’t create, or the content of existing pages suddenly changing
- Changes to settings you didn’t make
- A new user, especially one with high-level privileges, you didn’t add
- Plugins or themes you didn’t install
- Malware can often inject malicious code into your files. Check plugin and theme files, the wp-content/uploads folder, WordPress core files located in an incorrect directory, wp-config.php, and .htaccess. You should back up your site and have an understanding of the code before making any sensitive changes.
If you connect to your site with FTP, you can sort by recently modified files for code that shouldn’t be there.
If your site is infected periodically with malware and you can’t find any cause in the files, the issue may be with your server or another site on your server.
Make Sure Everything Is Up to Date
As we’ve already mentioned, out-of-date software is by far the most common vector of infection in WordPress. If there’s only one thing you can do to keep your site safe, it should be to keep WordPress updated.
The easiest way to check the status of all software on your site is to go to Dashboard > Updates, which will alert you if your core, theme, or plugins are out of date.
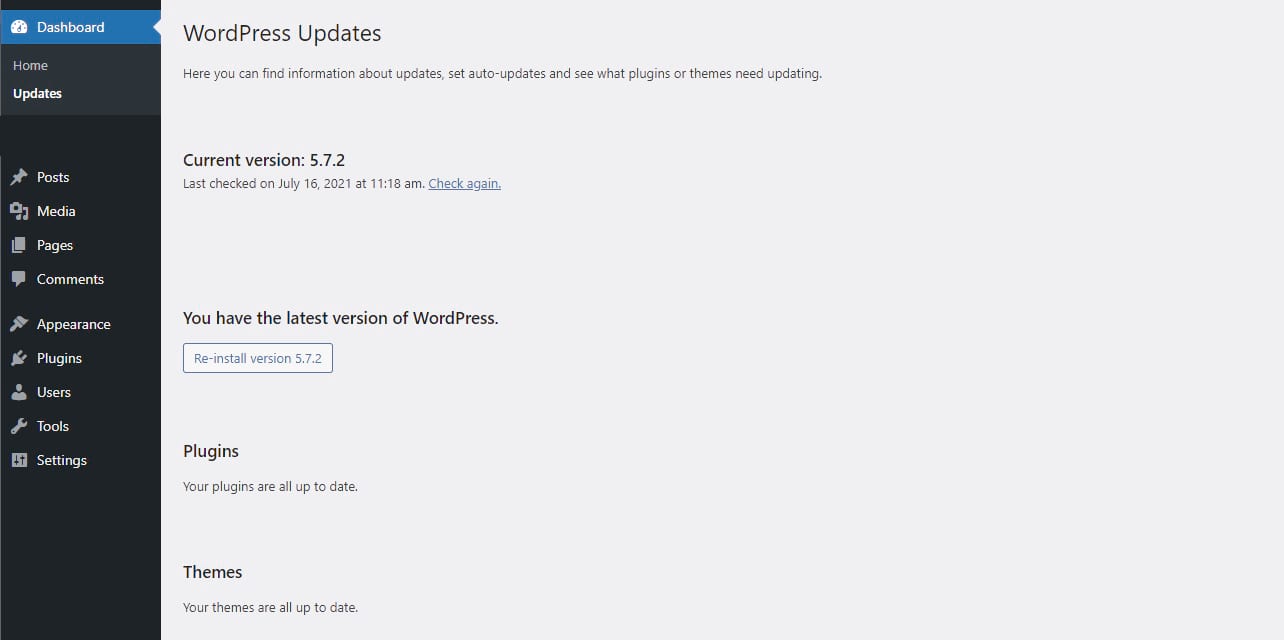
As WordPress now performs automatic updates since version 5.5, nothing should be outdated unless you have an outdated version of WordPress. If you don’t, you can update everything from this screen.
If you know there’s a new version of WordPress, but it isn’t showing up, click the Check again button below Current version.
You can also check your Plugins > Installed Plugins or Appearance > Themes pages for updates.
Secure Accounts and Passwords
A weak password on your main account makes it easy for anyone to break into your site with brute-forcing programs, giving them administrator access and the ability to change anything.
While a complicated password can be arduous to remember, making logging in less convenient, it’s even more inconvenient to have to recover your site from a hack. It’s definitely worth using a more secure password, even if you have to keep it written down.
Your password should use a mix of uppercase and lowercase letters, numbers, and symbols. It would be best if you did not base it on dictionary words or personal, guessable information such as your address or family member’s name.
In the best-case scenario, your password would be a long, tangled string of random characters. We strongly recommend you use a password manager. Use a site like 1Password or LastPass to generate a secure, unguessable password.
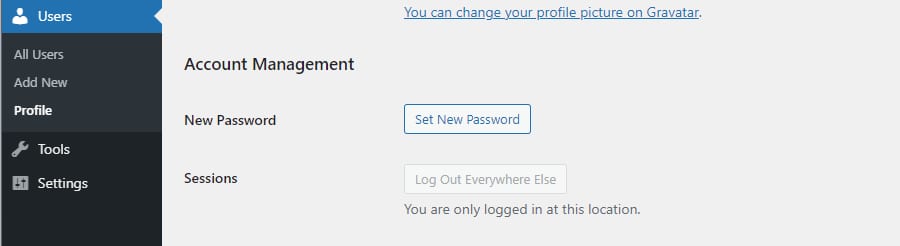
You can update your password and email in WordPress by going to Users > All Users or straight to Users > Profile. Scroll down and find Email under Contact Info, and New Password under Account Management.
While you’re on the Users page, take a look at all your users and make sure there’s no one there who you don’t recognize or has inappropriate permissions. You should immediately remove any unidentified user with admin permissions.
We also encourage you to look at this guide on restricting user permissions so only your account will be able to change sensitive files on your site.
Check Your SSL Certificate
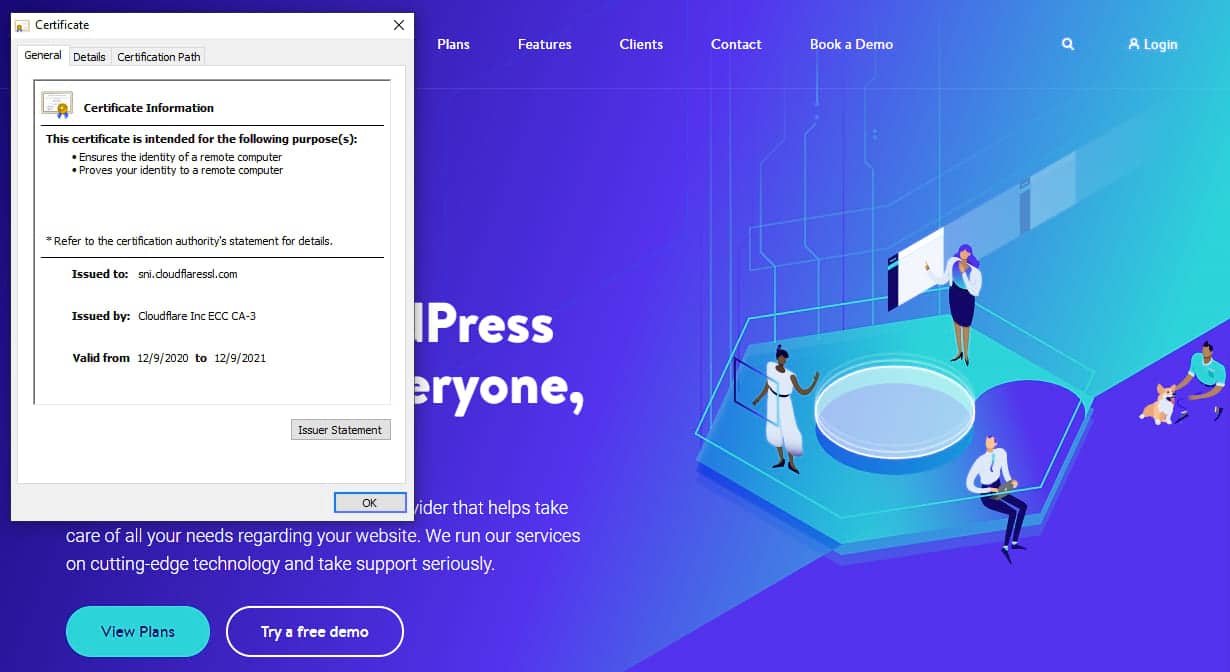
If your SSL certificate is out of date, you’ll usually instantly know; browsers like Google Chrome will block access to your site with a huge warning about the expired certificate. If you’re not sure or already getting this error, check your SSL certificate to see if it’s up to date and whether you’re using the latest version of SSL/TLS.
When you visit a website, you’ll see a lock icon in the address bar on most browsers. If your certificate is expired, this lock may be red or have a slash through it.
Click the lock icon, then click again to see certificate information, including its expiration date.
You can also use an SSL certificate checker to scan your site to make sure your certificate isn’t expired, and there are no vulnerabilities present in your SSL protocol.
Common Vulnerabilities
Many WordPress sites are filled with tiny vectors for attacks that may seem innocuous but can provide more information than you want to share.
Having a visible WordPress version in your frontend tells hackers exactly what vulnerabilities are present on your site. Especially if you’re using an outdated version of WordPress, you may want to hide this information.
You’ll notice file editors under Appearance > Theme Editor and Plugins > Plugin Editor in your backend.
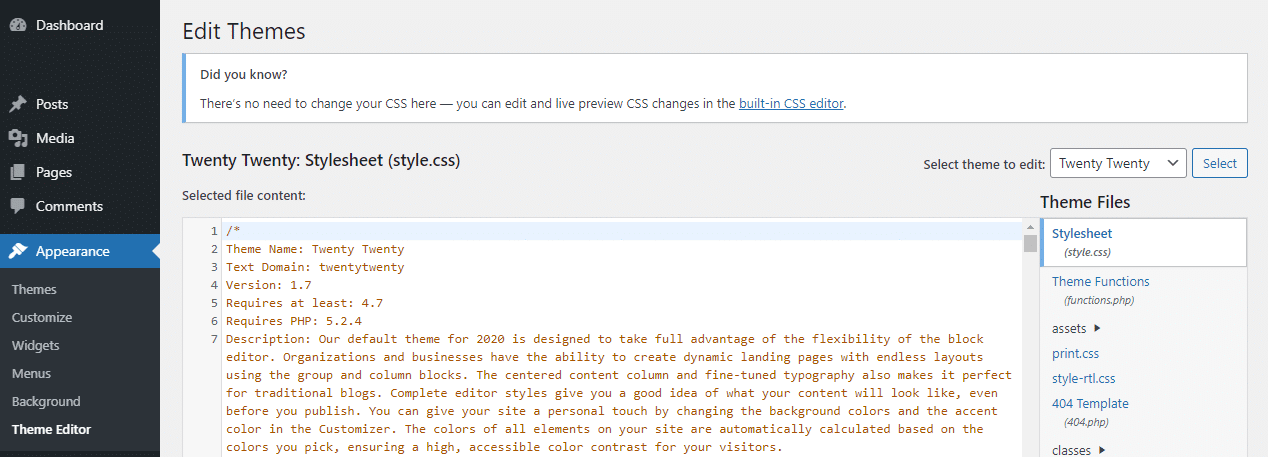
While these tools are very convenient, it also makes it suitable for anyone who hacks your site to break something, so you may want to turn them off. You can do so by adding this function to wp-config.php:
define( 'DISALLOW_FILE_EDIT', true );SQL injections are a common way of breaking into a site. If you have any forms or other user input, restrict the use of special characters and allow only safe, common file types to be uploaded.
Finally, for an extra layer of protection, you can password protect file directories.
How to Secure Your Website: Tips and Tools
If your site has malware, a good security plugin should do the trick in removing it. And we’ve covered above a few vulnerabilities you’ll want to check for.
Check Out Our Video Guide to Securing Your Website
We have a few other quick tips for securing your website and preventing infection before it can happen. You can apply most of these tips in minutes, so they should be easy to set up even if you’re unfamiliar with WordPress and web security.
Choose a Secure Host
When hackers are probing for a way into your site, they’ll often turn to the server to look for exploits. There’s plenty of cheap hosting out there, but they don’t always invest in the most secure servers.
Shared hosting can be a vector for infection. If one website is infected with malware, it can potentially spread to every site on the server. So you could end up with a site full of viruses and SEO spam, and it wouldn’t even be your fault.
That’s why it’s vital to do your research and pick a host that cares about security and invests in secure servers. You’ll still need to put the work in to secure your website, but at the server level, your data is safe.
Turn on Two-Step Authentication (2FA)
Two-step authentication (also known as two-factor authentication or 2FA) adds another login step. Besides username and password, you or anyone pretending to be you will also need another piece of information: a unique additional code.
It could be a numerical code sent to your phone, which can make your WordPress account nearly uncrackable through brute force. Alternatively, it may require email verification or a piece of information only you know.
While there’s no built-in way to enable two-factor authentication, many plugins add the functionality to WordPress.
Kinsta offers two-factor authentication to all customers. If you’re not a Kinsta user, though, the Wordfence security plugin we mentioned earlier comes with 2FA built-in. You can also try other website security tools, like the Two-Factor plugin for email codes or Duo to set up two-factor phone authentication through an app.

Make Backups Every Day
Backing up your site can’t save it from people trying to break in, but if something ever does happen, having a backup will be invaluable. It can mean the difference between losing weeks or even years of work and simply restoring to a backup from before the hack.
If you’re with Kinsta, we’ll cover you with daily automated backups that are stored for two weeks (30 days for those with Kinsta’s Agency Partner Program). In addition, you can create five manual backups and one downloadable backup per week, and there are optional add-ons to back up hourly or export to the cloud.
Plugins like UpdraftPlus can also help. It’s best to choose a service that backs up daily at a minimum to minimize data loss.
Use a Web Application Firewall
A web application firewall, or WAF, uses strict rules to filter incoming traffic, blocklisting IPs known to be associated with hacking or DDoS attacks. It prevents many attacks from ever reaching your server.
While you can apply WAFs at the server level, it’s easiest to purchase a cloud-based service such as one provided by Cloudflare or Sucuri.
Connect Over SSH or SFTP
Sometimes you need to connect to your site with FTP to add or modify files there. It’s always better to use SFTP over FTP; the difference is simple: SFTP is secure, and FTP isn’t.
With FTP, your data isn’t encrypted. If someone manages to intercept the connection between you and your server, they could see everything from your FTP login credentials to any files you upload. Always connect with SFTP.
You might also consider using SSH access, which allows you to connect to a command prompt and manage your site more directly. It’s safe, secure, and can remotely handle simple tasks. Our guide to SSH can help if you’re stuck.
Prevent DDoS Attacks
DDoS attacks slow your website to a crawl by spamming your server with thousands of bogus requests, preventing potential readers or customers from accessing it. Here are a few tips to stop them before they happen:
- Have a plan in place for when a DDoS attack hits. You don’t want to be panicking when you need to alert your web host and stop the attack.
- Use a web application firewall that may be able to detect fake traffic.
- Use specifically tailored anti-DDoS software.
- Disable xmlrpc.php to prevent third-party apps from using your server.
- Disable the REST API for general users.
Prevent Brute Force Attacks
Brute force attacks can be similar to DDoS attacks, but the goal is to guess your admin password and break into the site rather than bring your server down. That said, these can slow your site down as well.
- Again, a WAF can filter out bot traffic and blatant brute force attempts.
- Use two-step authentication on your admin account.
- Set up an activity log and keep an eye on unauthorized login attempts.
- Change the login page URL and limit the number of login attempts.
- Password-protect your login page.
- Use a long, randomly generated password and change it every year or so.
Website Security Tools You Need to Know About
Besides those we’ve already mentioned, here are a few more online security tools that will help you lock down your website:
- Intruder.io: Scan for the latest vulnerabilities.
- SSL Server Test: Developer tool that analyzes your SSL certificate and identifies weaknesses.
- HTML Purifier: Filters out malicious code/XSS, great if you have infected code that you need to clean up.
- Mozilla Observatory: Actionable advice to purge your code of common vulnerabilities.
- sqlmap: A penetration testing tool to identify exploits in your SQL code.
- Detectify: Scan your web apps with the help of ethical hackers.
- WPScan: A CLI-based WordPress scanner.
- SonarQube: Write standards-compliant code free of security vulnerabilities.
Website Security Checklist
Is your website safe from attack? Make sure you’ve ticked almost everything on this checklist:
- Are you using a secure, high-quality hosting environment?
- Have you scanned your site with a plugin or online scanner to check for viruses?
- Have you installed an activity log, and are you monitoring it for unusual changes?
- Are you and any user with high-level privileges using secure passwords and two-factor authentication? Are all emails correct?
- Are WordPress, its themes and plugins, and underlying systems such as PHP up to date?
- Is your SSL certificate secure and up to date?
- Have you checked for unexplainable changes, deletion or addition of content, or links you didn’t add in your webpages, settings, or files?
- Is your login page protected by a password and limited login attempts?
- Have you checked for new users you didn’t add?
- Are forms, comment boxes, and other sources of user input secured? (Disallow special characters and restrict file uploads to known file types.)
- Have you disabled xmlrpc.php and the REST API to prevent DDoS attacks?
- Have you disabled theme and plugin editing in the dashboard?
- Do you have a daily backup service in place?
- Do you have a web application firewall set up?
Summary
Website security is no minor deal, so if you’re not on top of it yet, the time is now to make it a priority. Getting hacked doesn’t just annoy — it can end in damaged SEO, devastating data loss, lost user trust, and malware that comes back again and again.
You don’t need to be a seasoned developer to take a few extra steps to secure your site. And that starts with a proper website security check. Even something as simple as picking a better password or switching to a more secure host could make all the difference.
Need more security tips? Learn about 19 more ways to secure your site. And feel free to share your suggestions in the comments below!


