Every day, countless businesses are taking their operations online to attract new customers and scale globally. One of the quickest ways to get a website up and running is through WordPress, which powers over 43% of all sites on the internet.
But with this popularity comes a downside. Bots and hackers are always on the lookout, trying to exploit any vulnerabilities in WordPress sites. These vulnerabilities often arise from installing compromised plugins or themes or using poor hosting that can’t detect or prevent the most common attacks, like Distributed Denial of Service (DDoS) or brute force attempts.
Many business owners fall into the trap of choosing cheap hosting, only to later spend a fortune fending off attacks — attacks that often stem from the inadequate security of their hosting provider.
This is why, as a business, you shouldn’t be swayed by low costs when selecting a host. The focus should be on quality, especially in terms of security. You must dig deeper and ask the right questions or seek detailed information about your host’s security measures before choosing. It’s not enough for a host to promise security. You need to understand how that security is implemented.
That’s where this guide comes in. We’ve created a comprehensive checklist of essential questions you should ask your web host about security before making your decision.
1. Data encryption
Data encryption is critical for safeguarding the information exchanged between your website and its users. Whether it’s customer details, payment information, or confidential business data, ensuring this information is encrypted is non-negotiable.
What to ask:
- Does the hosting provider offer SSL/TLS certificates, and are they included in the hosting package?
- What level of encryption is used for data in transit and at rest?
- How does the host ensure the security of sensitive information (e.g., customer data, financial transactions)?
Why it matters:
SSL/TLS certificates are essential for encrypting data transmitted between your website and its users. They ensure that sensitive information — like credit card numbers or personal details — cannot be intercepted by malicious actors. Without SSL/TLS encryption, your site is vulnerable to man-in-the-middle attacks, where hackers can intercept and manipulate the data flowing to and from your site.
But encryption shouldn’t stop at data in transit. It’s equally important to ensure that your data is encrypted at rest, meaning it’s securely stored on the server, making it inaccessible to unauthorized users even if they gain access to the physical server or the data center.
When choosing a web host, it’s crucial to confirm that they offer SSL/TLS certificates and use strong encryption standards, such as 256-bit Advanced Encryption Standard (AES), to protect your data in transit and at rest.
Ask about their policies and practices for encrypting sensitive information and ensuring your data remains secure, even in worst-case scenarios. Understanding these encryption measures will give you peace of mind, knowing your business and customer data are protected.
How Kinsta handles data encryption
At Kinsta, we protect your data through robust encryption practices, both in transit and at rest.
For example, all verified domains on Kinsta (localhost domains, temporary domains, and custom domains) benefit from our integration with Cloudflare, which includes free SSL certificates with TLS 1.2 and TLS 1.3 enabled — standards that provide strong encryption and are widely supported by all major browsers. This automatic SSL setup means you don’t have to worry about manually configuring your site’s security unless you want to use a custom SSL certificate.
In addition to securing data in transit, Kinsta encrypts all customer data at rest across our powerful cloud infrastructure. Stored data is protected using 256-bit AES encryption, ensuring it remains secure even in the event of physical access to the underlying hardware. Encryption keys are regularly rotated and protected by multiple layers of security controls.
However, it’s important to note that while the disks are encrypted, an attacker who gains access to your website through compromised credentials (like SSH access) or a vulnerability in your site can read unencrypted copies of the files. This makes it crucial to maintain strong security practices at the site level, such as using strong passwords, enabling two-factor authentication, and regularly updating software.
Our commitment to data encryption extends beyond technical measures. Over the years, we have worked hard to become SOC 2 compliant and recently achieved ISO 27001, 27017, and 27018 certifications. See more information in this article’s security audits and compliance section.
2. Firewall and DDoS protection
Your website’s security relies heavily on the strength of its firewall, which serves as the first line of defense against numerous cyber threats, including DDoS attacks.
A robust firewall filters out malicious traffic, prevents unauthorized access, and ensures your site remains available during attempted disruptions. Understanding how your hosting provider implements these protections is crucial for maintaining your site’s security and performance.
What to ask:
- Does your hosting service include a web application firewall (WAF) as part of the package?
- How does your firewall protect against DDoS attacks and other common threats?
Why it matters:
A Web Application Firewall (WAF) protects your site from various threats, including SQL injections, cross-site scripting (XSS), and DDoS attacks. These are the most common and potentially damaging attacks threatening your website.
A well-managed WAF can block these threats before they reach your site, minimizing the risk of a security breach and ensuring your site remains accessible.
DDoS attacks, in particular, aim to overwhelm your site with a massive influx of traffic, rendering it slow or completely unavailable to legitimate users. The impact can be devastating, leading to lost revenue, damaged reputation, and frustrated customers.
A strong firewall not only filters out this malicious traffic but also plays a critical role in defending your site against DDoS attacks, ensuring that your site remains operational even during an attack.
Effective firewall and DDoS protection involves more than just setting up basic defenses. It requires continuous monitoring, automated threat detection, and the ability to absorb and mitigate large-scale attacks.
How Kinsta handles firewall and DDoS protection
At Kinsta, we take a multi-layered approach to keep your website secure, especially from threats like DDoS attacks. Central to our protection strategy is our integration with Cloudflare.
All traffic for sites hosted on Kinsta passes through Cloudflare, where a powerful WAF filters it. The WAF automatically blocks harmful requests, including DDoS attacks, before they can reach your site.
For example, we reported how we managed to serve 75.51 billion requests through Cloudflare in just one month, of which 3.3 billion were mitigated by Cloudflare’s Web Application Firewall (WAF). This shows the effectiveness of Cloudflare’s DDoS protection in filtering out malicious traffic.
Beyond Cloudflare, Kinsta applies additional network-level firewall controls across our optimized server environments. We also operate internal systems that monitor abusive traffic patterns across the platform and automatically block behavior deemed harmful, ensuring platform-wide stability.
Additionally, our SysOps team constantly updates firewall rules based on specific issues or threats. We manage these updates in-house to ensure top-notch security and don’t offer manual control over these rules through customers’ MyKinsta dashboards.
For customers with unique needs, we recommend having their WAF solution in front of our infrastructure using WAF providers like Sucuri and Wordfence.
3. Backup and recovery plans
Backups are your safety net. In the event of a cyberattack, server failure, or accidental data loss, having a reliable backup ensures that you can restore your website quickly and avoid prolonged downtime or permanent loss of important data.
But backups are only as good as the frequency with which they’re made and how easily they can be restored. When choosing a host, it’s important to know what backup and recovery options are available and how they protect your data.
What to ask:
- How often are backups performed, and where are they stored?
- What is the process for restoring data in case of a breach or loss?
- Are backups encrypted and stored off-site to prevent loss in case of a local disaster?
Why it matters:
Frequent, automated backups ensure you don’t lose critical website data due to unexpected issues like a breach, server crash, or user error. Knowing that backups are performed daily or more frequently provides peace of mind that you can restore your site to a recent version without significant data loss.
The location of backup storage is also important. Storing backups in a secure, off-site location means your data remains protected even if there’s a problem with the primary server or data center. Encrypting backups ensures that your sensitive data remains safe even if they’re intercepted.
Finally, ease of restoration is key. If something goes wrong, the ability to quickly and easily restore a backup without technical complications or delays is crucial to minimizing downtime and keeping your site running smoothly.
Having a clear understanding of your web host’s backup and recovery plans helps ensure that, no matter what happens, you can restore your site with minimum disruption.
How we handle backup and recovery at Kinsta
At Kinsta, we understand the critical importance of having reliable backups. That’s why we offer a comprehensive backup solution that ensures you can quickly recover your site in case of an emergency.
We offer the following types of backups:
- Automatic daily backups: We provide automatic daily backups for all WordPress sites hosted on our platform. These backups capture a complete snapshot of your site, including files, databases, redirects, and MyKinsta settings. This means that if something goes wrong, you can easily restore your site to its previous state with just a few clicks in MyKinsta.
- Manual and hourly backups: When making significant changes to your site, you can create up to five manual backups, ensuring you have restore points exactly when you need them. Additionally, we offer an hourly backup add-on for users who need even more frequent restore points — ideal for eCommerce sites or other dynamic environments where data changes often.
- External backups: We offer an external backups add-on that allows you to back up your site to Google Cloud Storage or Amazon S3. This off-site backup option adds an extra layer of security, making it easy to incorporate these backups into your broader disaster recovery strategy.
- Downloadable backups: We also allow you to create and download a backup of your site in a ZIP file once per week. This backup includes your site’s files and database, allowing you to keep a copy offline for extra security.
At Kinsta, we also know the importance of easy backup restoration. In MyKinsta, the process is quick and simple whether you need to restore to your live environment or a staging site. If you ever need to undo a restoration, a new backup is automatically created before the restore, giving you flexibility and control over your site’s state.
Also, depending on your plan, backups are retained for up to 30 days, ensuring you have ample restore points to choose from if something goes wrong. We offer extended retention periods for those on our higher-tier plans, providing even greater peace of mind.
4. Access control and authentication
Controlling who can access your website’s backend and server environment is crucial for maintaining security.
Unauthorized access can lead to data breaches, site defacement, or compromise. Implementing strong access control measures and secure authentication methods is essential to protecting your site.
When evaluating a hosting provider, understanding how they manage access control and authentication can give you confidence that your site is well-protected from unauthorized users.
What to ask:
- What access control measures are in place to prevent unauthorized access to my account and server?
- Does the host support multi-factor authentication (MFA) for accessing the control panel, FTP/SFTP, and SSH?
- How are permissions managed for multiple users or team members?
Why it matters:
Strong access control is the foundation of your website’s security. Without proper access controls, unauthorized users could gain entry to your site’s backend, potentially leading to data theft, unauthorized changes, or even complete site takeover.
Effective access control involves limiting who can access your site and ensuring that those with access use secure, up-to-date authentication methods.
MFA is a key component of secure access control. By requiring a second form of verification — such as a text message code or authentication app — in addition to a password, MFA adds an extra layer of protection against unauthorized access. This is especially important for critical areas like your hosting control panel and FTP/SFTP and SSH access, where a breach could have severe consequences.
Managing permissions effectively is also essential, particularly for sites with multiple users or team members. A well-structured permission system ensures that users only have access to the areas of the site they need, reducing the risk of accidental or malicious changes.
It’s important to understand how your hosting provider handles user permissions and whether they offer tools to help you manage access across your team.
How we handle access control and authentication at Kinsta
Kinsta is a managed WordPress hosting solution that provides a custom-built cPanel alternative for managing your sites. This dashboard offers many features that are not available in the cPanel while being easier to use.
We use Role-Based Access Control (RBAC) in MyKinsta. This means you can assign different access levels to team members based on their roles, ensuring that each person only has access to what they need. For example, a WordPress Site developer might have access only to staging environments, while a Company Administrator can manage the entire company account. This level of control minimizes the chances of unauthorized changes and keeps sensitive areas restricted to the right people.
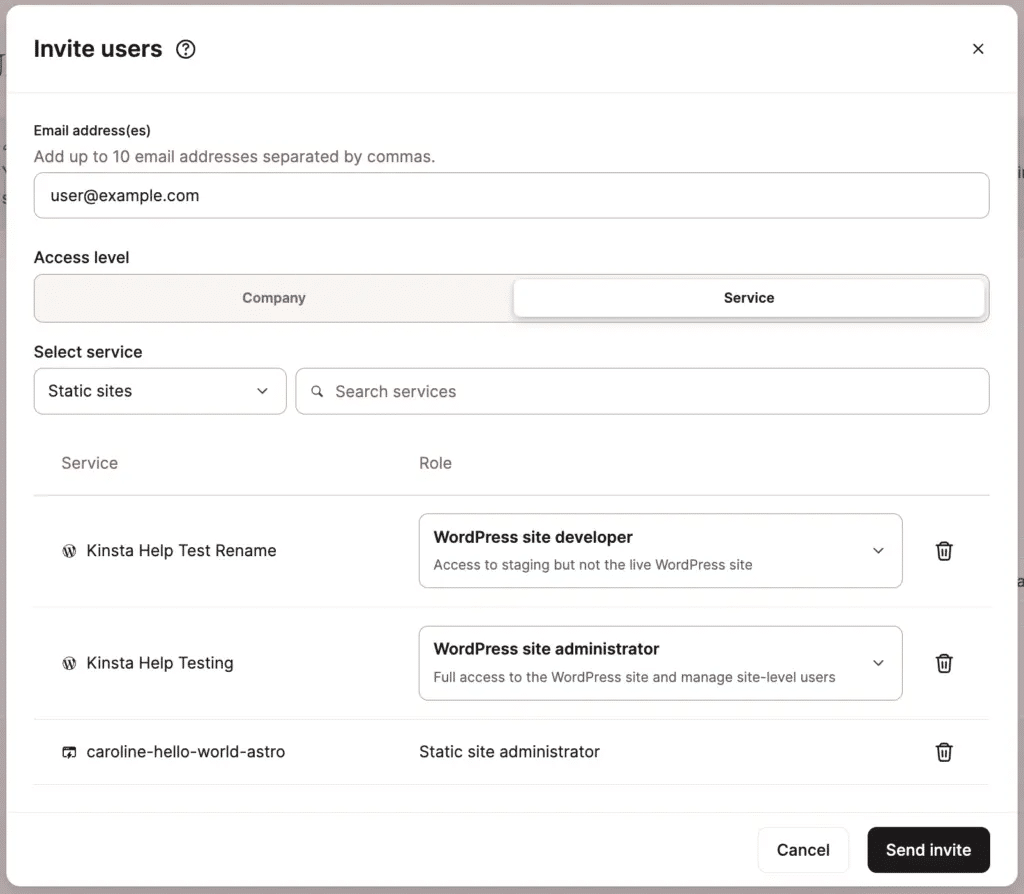
Dashboard security is strengthened by 2FA, which is available to all users in MyKinsta. This extra step, requiring users to verify their identity with a code from an authenticator app, ensures that access to the account is protected even if a user’s password is compromised. It’s a simple yet powerful layer of defense that helps secure your website and account.
Additionally, we support Single Sign-On (SSO) using OAuth 2.0 via GitHub. This allows you to log in to MyKinsta securely with your GitHub credentials, making the login process smoother while maintaining strong security standards.
Kinsta enforces strict internal access controls based on the principle of least privilege. Our internal identity and access management systems ensure team members have only the minimum permissions required to perform their roles, reducing the risk of unauthorized access to customer environments.
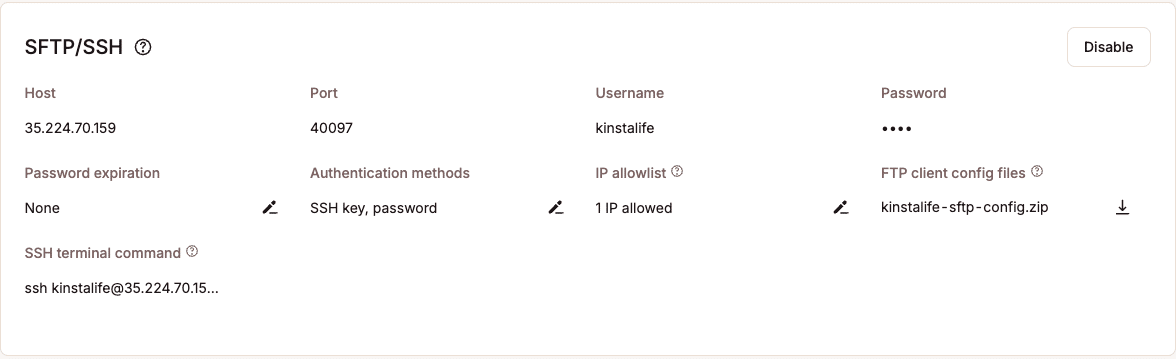
For secure backend access, we provide SSH and SFTP connections, with credentials managed in MyKinsta. You can enhance security by setting password expiration intervals, restricting access by IP address, or enabling SSH key-only access.
Additionally, you can disable SFTP/SSH access when not needed and adjust password controls, giving you full control over how and when access is allowed, ensuring your site’s environment remains secure.
5. Malware detection and removal
With so many plugins, themes, and software components, vulnerabilities can easily appear in a WordPress site, especially when these elements become outdated. This increases the risk of malware (malicious software) infections, leading to serious consequences like data theft, site defacement, or even losing control of your website.
Detecting and removing malware swiftly is critical to maintaining your website’s security and reputation. That’s why it’s essential to understand how your hosting provider handles malware detection and removal.
What to ask:
- Does the hosting provider offer automatic malware scans, and how often are they performed?
- What happens if malware is detected, and how is it removed?
- Can I add additional tools or plugins for enhanced malware protection?
Why it matters:
Malware infections can compromise your site’s security and reputation, leading to loss of customer trust and even search engine penalties. This is why regular, automated malware scans are essential. They help you detect threats early, allowing for prompt action before they cause significant damage. If malware is found, having a clear and efficient removal process is key to quickly restoring your site to a clean state.
Additionally, having the option to add your security tools or plugins can further strengthen your defense.
Knowing how your host handles malware detection and removal will give you peace of mind that your site is continuously monitored for threats and can be quickly cleaned if an infection occurs.
How Kinsta handles malware detection and removal
At Kinsta, we monitor your sites 24/7, scanning for malicious code and potential threats. Our proactive approach ensures we catch malware early before it can cause serious damage. In the event that malware is detected or a site is compromised, we take swift action to clean up the infection.
Our security pledge guarantees that if your WordPress site is hacked while hosted with us, we’ll work with you for free to remove the malware and restore your site. This includes a deep scan of your site’s files, identification of the source of the infection, and removing any affected plugins or themes.
Our container-based hosting infrastructure also prevents cross-contamination between sites at the server level, providing additional peace of mind that your other sites remain unaffected. You can also use popular WordPress security plugins like Sucuri and Wordfence.
6. Uptime monitoring and response
When your website goes down, it can have serious consequences for your business — lost revenue, damaged reputation, and frustrated users. Uptime monitoring is crucial to ensure your site remains online and accessible to visitors.
A hosting provider must offer good uptime performance, robust monitoring systems, and a rapid response plan to address any downtime.
What to ask:
- Does the hosting provider offer 24/7 uptime monitoring?
- How quickly do they respond to downtime, and what is their process for getting the site back online?
- Is there a guaranteed uptime percentage in their service-level agreement (SLA)?
Why it matters:
Website downtime can be costly. When your site is offline, you lose potential sales or engagement, your SEO ranking can also suffer, and your brand’s reputation may suffer. That’s why uptime monitoring is essential.
Continuous monitoring ensures that downtime is immediately detected, allowing the hosting provider to take quick action and minimize the impact.
A good hosting provider will have systems in place to monitor uptime 24/7 and a dedicated team ready to respond to problems. In addition, a guaranteed uptime percentage — such as 99.9% — in a service-level agreement (SLA) assures that the host is committed to keeping your site running smoothly.
Knowing how your provider handles uptime monitoring and their response to downtime is key to ensuring your site’s reliability and availability.
How we handle uptime monitoring at Kinsta
Kinsta prioritizes uptime by monitoring the status of every WordPress site on our platform every three minutes. This frequent monitoring ensures that we detect issues as soon as they arise. If a site fails to load, our engineers are immediately alerted and respond quickly to restore service.
In addition to our internal response, we notify you directly if critical issues persist over consecutive checks. This includes site errors, DNS misconfigurations, SSL certificate problems, and domain expiration. These proactive notifications help you stay informed and act swiftly if needed.
Thanks to the strength of our infrastructure, our platform is backed by a 99.9% uptime guarantee through our Service Level Agreement (SLA).
7. Logging and activity tracking
In addition to uptime monitoring, detailed logging allows you to track every action and event happening on your website. This helps in troubleshooting, auditing, and maintaining the security of your site by keeping a record of user activities, data access, and server performance.
What to ask:
- Does the host offer activity logs to track user actions and data access?
- Can I access server logs for troubleshooting and performance monitoring?
- How long are logs stored, and are they easily accessible?
Why it matters:
Logging is essential for maintaining your site’s security and performance. Activity logs allow you to track who did what and when, which is crucial for detecting unauthorized actions or pinpointing the cause of an issue. Access to server logs is also important for troubleshooting server-level problems, diagnosing errors, and monitoring resource usage.
A good hosting provider will offer easy access to user activity and server logs, ensuring you have the tools to monitor your site’s health and security.
How Kinsta handles logging and activity tracking
Kinsta provides detailed activity logging and server logs to give you full visibility over your site and account. With the activity log, you can track all key actions performed within MyKinsta, like site changes or updates, and see who initiated them and when. This is especially useful for monitoring team activities and quickly identifying any issues.
For troubleshooting, our platform gives you access to important server logs, including error logs and access logs, directly through the MyKinsta dashboard.
These logs help you diagnose issues like PHP errors, cache performance, or server requests, making it easier to resolve problems quickly. Additional logs, like cache-purge and mail logs, are available via SFTP for more advanced diagnostics.
Our platform also sends real-time notifications to inform you of system status, so you’ll always know if platform-wide issues arise.
8. Security audits and compliance
Security audits and compliance checks ensure your website meets industry standards and follows best practices for protecting sensitive data.
Regular security audits identify vulnerabilities and weaknesses in your system, while compliance with security frameworks ensures that your site follows the necessary regulations, especially for businesses handling personal data or financial information.
Knowing how your hosting provider handles security audits and compliance is essential to maintaining a secure and compliant website.
What to ask:
- Does the hosting provider conduct regular security audits on its infrastructure?
- Is the host compliant with industry security standards and regulations (such as SOC 2, GDPR, PCI DSS)?
- What security certifications does the hosting provider have, and how often are they renewed?
Why it matters:
For businesses that handle sensitive data, compliance with regulations like GDPR, PCI DSS, or SOC 2 is essential for avoiding fines and maintaining customer trust.
Hosting providers that conduct regular audits and maintain compliance with industry standards show a commitment to maintaining a secure environment. Certifications like ISO 27001 and SOC 2 demonstrate that the host follows strict security protocols and undergoes regular checks to ensure ongoing security.
By understanding your host’s approach to security audits and compliance, you can rest assured that your website meets both security best practices and regulatory requirements, reducing the risk of breaches and ensuring data protection.
How we handle security audits and compliance at Kinsta
At Kinsta, we take security and compliance seriously, ensuring that our platform meets industry-leading standards. To maintain our compliance with SOC 2 Type II and ISO 27001, we undergo annual security audits conducted by independent agencies, including BARR. These reports, updated annually, demonstrate our commitment to safeguarding your data and infrastructure.
Our compliance doesn’t stop there. We are also certified for ISO 27017 and ISO 27018, reinforcing our adherence to best practices for cloud security and protecting personal data in cloud computing environments.
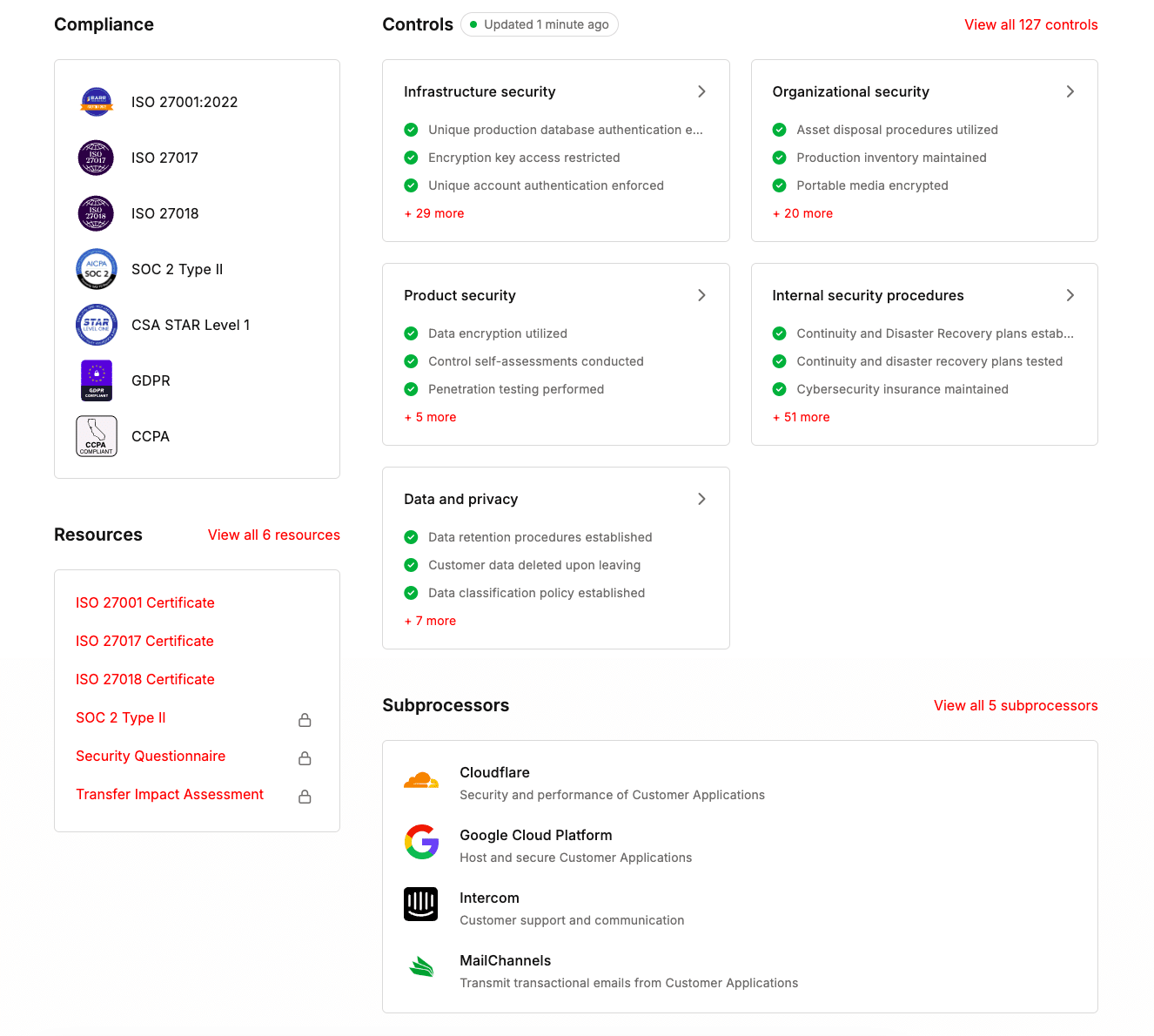
Additionally, we emphasize Data Leak Prevention (DLP) and Data Rights Management. Our system is designed to align with your organization’s Information Security Policy, ensuring that sensitive data is protected against unauthorized access or exposure.
Our Data Processing Addendum (DPA), part of our terms of service, outlines how we handle your data, ensuring compliance with regulations like GDPR and CCPA. This includes how data is processed, stored, and protected, giving you peace of mind that your data is safe and secure.
By leveraging Kinsta’s enterprise-grade security controls and Cloudflare, we ensure that our infrastructure meets the highest security standards. Our infrastructure is independently assessed for compliance with PCI DSS 3.2 requirements, adding another layer of trust and security to our hosting platform.
With these certifications and regular audits in place, we assure you that your site is hosted on a secure, compliant platform that consistently meets the most stringent industry standards.
You can learn more from our trust page.
Summary
This checklist is not exhaustive but covers many essential aspects of hosting security. You can understand how your hosting provider handles security by focusing on key areas like data protection, DDoS prevention, uptime monitoring, and compliance.
Asking these questions helps ensure that your business is protected from common threats and aligned with best practices for data security and privacy.
Being proactive about security will give you confidence that your website is safe, allowing you to focus on growing your business.
If you believe Kinsta meets your security needs and you’d like to learn more about our pricing to find the best plan for your business, contact our sales team.