Microsoft Entra SAML SSO
Microsoft Entra (formerly Azure) is an Identity Provider (IdP) that enables secure single sign-on (SSO), allowing your company’s users to access multiple applications with one login.
With Security Assertion Markup Language (SAML) SSO, employees sign in once using their company credentials (typically email and password). The IdP, such as Microsoft Entra, verifies their identity and grants seamless, secure access to all connected services, without requiring separate logins for each application.
Company owners or IT administrators can link their organization’s email domain (e.g., @mycompany.com) to the IdP so that anyone with a company email address is automatically recognized and can securely sign in to SAML-enabled tools.
Using Kinsta SAML SSO, you can connect Microsoft Entra to MyKinsta by creating a SAML application within Microsoft Entra, verifying your company’s email domain, and adding the required Microsoft Entra details in MyKinsta. This allows your team to log in with their existing company credentials, eliminating the need to create or manage separate MyKinsta accounts.
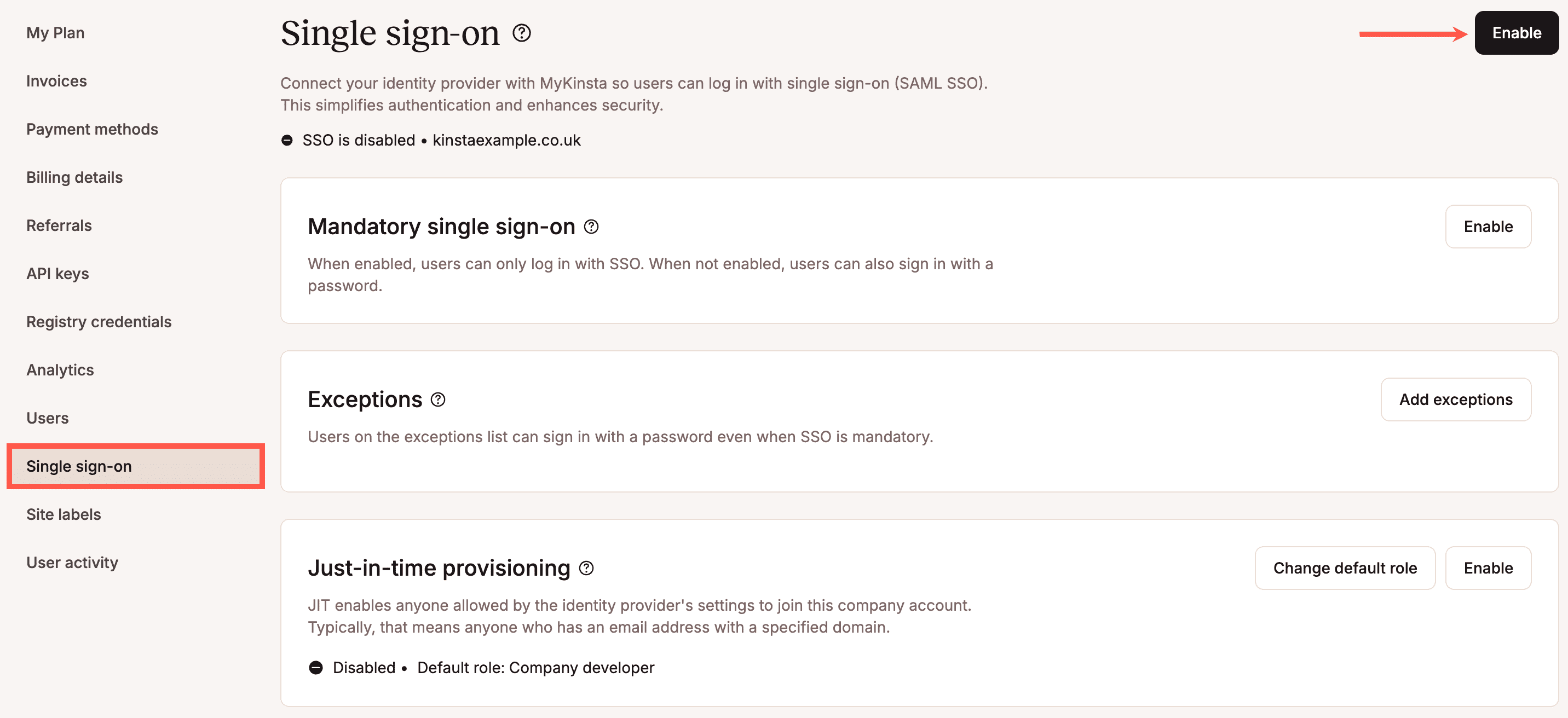
Enable SSO in MyKinsta
When you set up SAML SSO, you can click Save and exit setup at any stage to store your progress and return later.
In MyKinsta, go to your username > Company settings > Single sign-on, and click Enable.
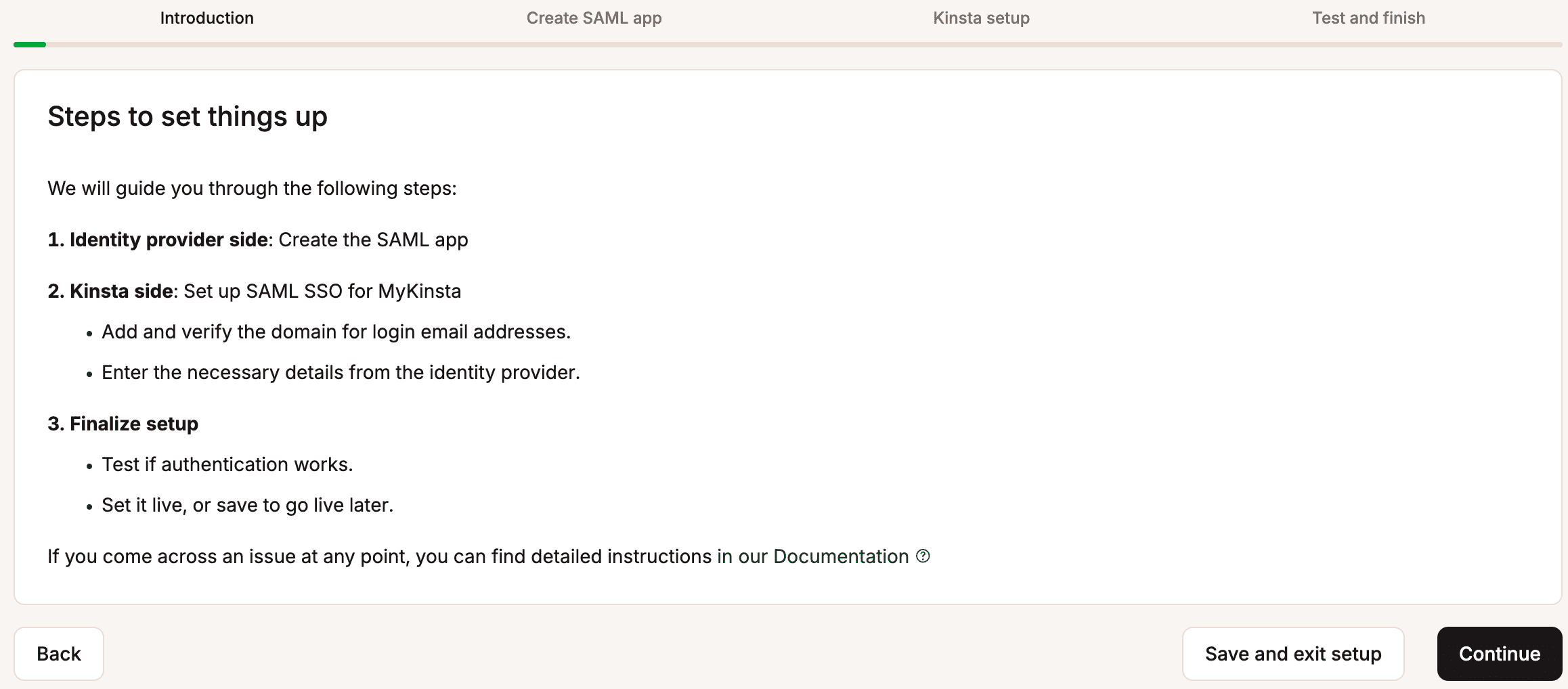
Read through the introduction, which explains how SSO will be set up, and click Continue.
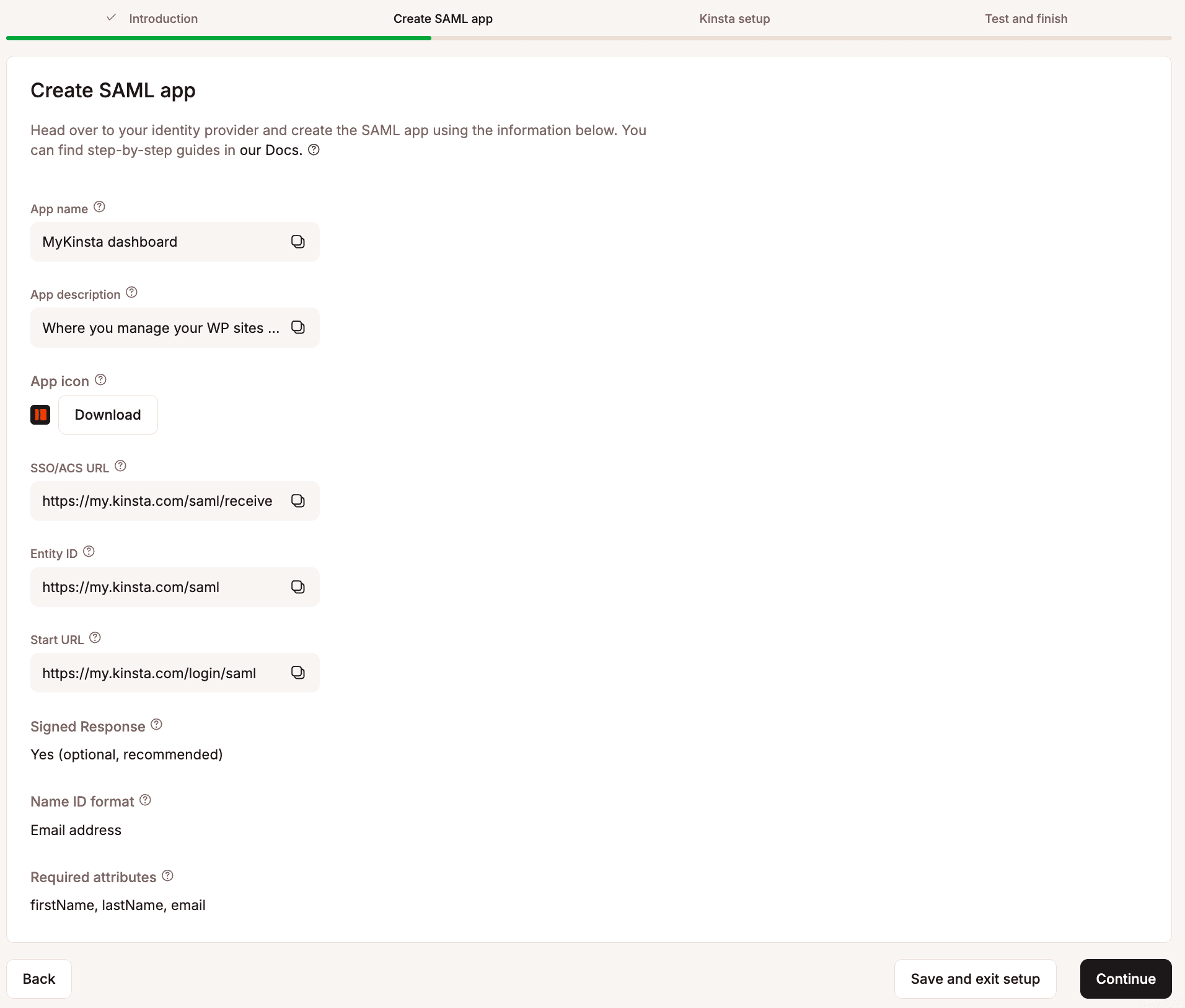
The next page provides all the information you need to set up your SAML app within Microsoft Entra.
Set up the app integration in Microsoft Entra
In MyKinsta, the Create SAML app tab provides all the information you need to set up your SAML app within Microsoft Entra. The following steps explain where to add this information.
Log in to Microsoft Entra as a user with admin access, and within the Microsoft Entra admin center, click Entra ID > Enterprise applications > New application.

Click Create your own application, enter a name for your application, for example, MyKinsta Dashboard, and click Create.

Once the application is created, click Single sign-on and select SAML.

Within Basic SAML Configuration, click Edit.

Complete the Basic SAML Configuration in Microsoft Entra as follows:
- Identifier (Entity ID): Click Add identifier and then copy and paste the Entity ID from MyKinsta.
- Reply URL (Assertion Consumer Service URL): Click Add reply URL and then copy and paste the SSO/ACS URL from MyKinsta.
- Sign on URL: Copy and paste the Start URL from MyKinsta.
Leave all other fields as default and click Save.

Map your Microsoft Entra attributes
Within Microsoft Entra, you must map the firstName, lastName, and email attributes from MyKinsta to the correct fields within Microsoft Entra. For more information about how to do this, refer to the Microsoft Entra documentation.
Assign users to the Microsoft Entra app
In Microsoft Entra, go to Enterprise apps, select the application you set up for the MyKinsta Dashboard, click Users and groups, and then click Add user/group.

Click None selected, select the users or groups you want to grant MyKinsta access via SSO, and then click Select.

Click Assign and then click Assign to People. If you have your users set up in groups, click Assign to Groups. Click Assign on each user or group you want to assign to the Kinsta SAML SSO application and then click Done.
To test authentication, make sure the MyKinsta user account you’re signed in with is assigned.
Kinsta setup
In MyKinsta, on Create SAML app, click Continue so that you are on the Kinsta setup page.
Email domain
In the Domain name, enter the email domain users will use to sign in using SAML SSO, and click Add domain.
Only MyKinsta accounts with an email address matching the verified domain can authenticate via SAML. For example, if SAML is enabled for example.com, only users with an @example.com email address will be able to sign in for that company.
If the domain has already been verified in MyKinsta through DNS management or as a site domain, it will automatically be verified. If it hasn’t, you’ll be prompted to add a TXT record to your DNS management service to confirm domain ownership.
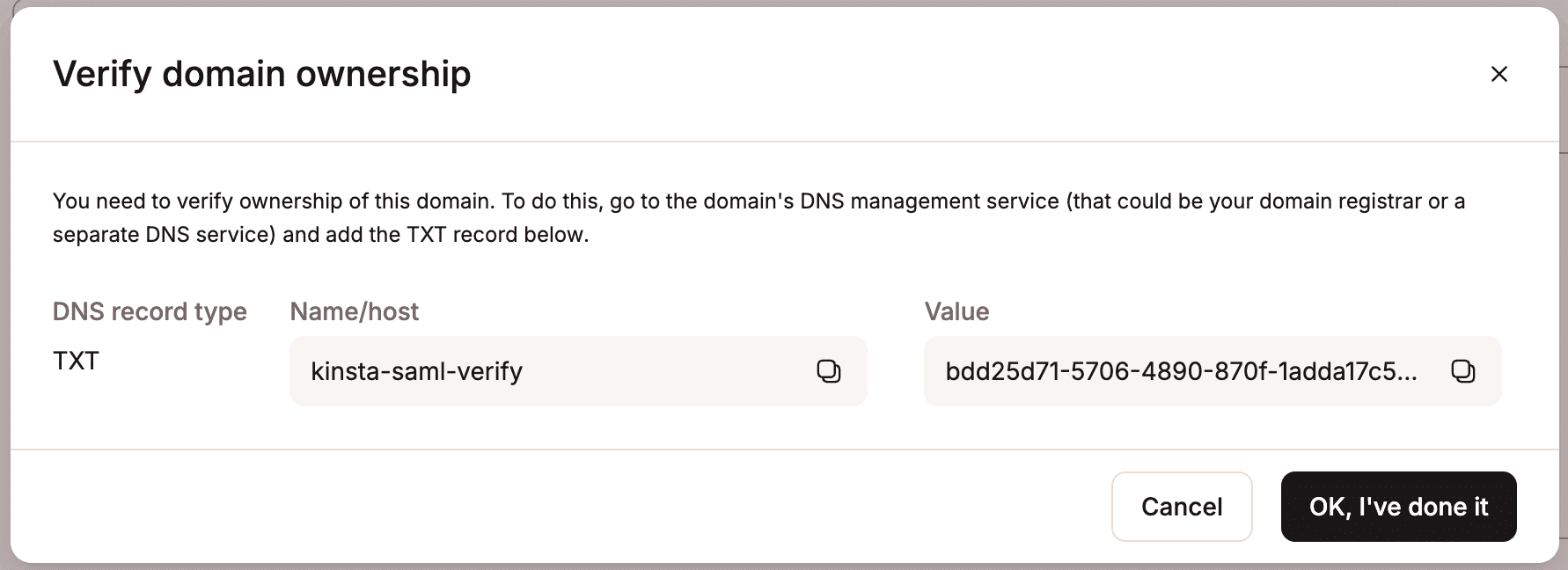
Because DNS changes can take time to propagate, you can click Save and exit setup to store your progress and return later.
Set up Kinsta SAML
In Microsoft Entra, go to Enterprise apps, select the application you set up for the MyKinsta Dashboard, and click Single sign-on.
In MyKinsta, within the Single sign-on Kinsta setup tab, complete the fields as follows:
- SSO URL: Copy and paste the Login URL from the Set up MyKinsta Dashboard section in Microsoft Entra.
- Entity ID: Copy and paste the Microsoft Entra Identifier from the Set up MyKinsta Dashboard section in Microsoft Entra.

- Public certificate: In Microsoft Entra, within SAML Certificates, click Download on Certificate (Base64). Open this file in any text editor, and copy and paste the contents into MyKinsta.

Click Continue.

Test the authentication in MyKinsta
You cannot enable SAML SSO within MyKinsta without first testing the authentication.
In MyKinsta, within the Single sign-on Test and finish tab, click Test authentication.
A notification appears if the test was successful or if the test fails.
If the test fails, click Back and check your SAML settings within Microsoft Entra and within MyKinsta.
If the test is successful and you want to enable SAML, click Save and set changes live.
Your MyKinsta company users will now be able to sign in with SAML SSO or by entering their username and password. Users who sign in through an IdP are not required to complete Kinsta’s 2FA, as authentication is handled directly by the IdP.
If you want to force users to sign on via SAML, you can enable Mandatory SSO and add Exceptions. You can also enable JIT provisioning to allow users authorized by your IdP to access your MyKinsta company without requiring an invitation.

Change the session duration
Your Identity Provider (IdP) determines how long your SSO session remains active and when it expires. If your IdP doesn’t specify a session duration, MyKinsta defaults to a 24-hour session.
When your SSO session expires, you’ll be logged out of SSO. If you’re working within a company that uses SSO, you’ll be prompted to reauthenticate. If you have access to multiple companies in MyKinsta, you’ll remain logged in overall but will need to reauthenticate before accessing any company that requires SSO.
For details on adjusting session duration, refer to the Microsoft Entra Documentation.