WordPress powers over 43.6% of the web, making it a prime target for cyberattacks. With thousands of plugins and themes, vulnerabilities are constantly being discovered and exploited.
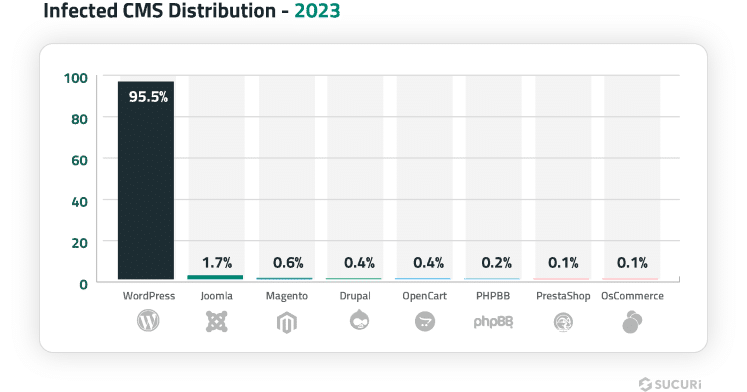
In 2023, a Sucuri study found that 95.5% of all detected infections were on WordPress sites — up from 83% in 2017. While other CMS platforms like Joomla (1.7%) and Magento (0.6%) also have security risks, WordPress dominates in both usage and attacks.
A major reason for this is outdated software. According to Sucuri:
- 39.1% of hacked CMS sites were running outdated versions at the time of infection.
- 13.97% of compromised sites had at least one vulnerable plugin or theme, making plugins and themes the weakest links.
- 49.21% of infected sites contained backdoors, such as fake plugins or injected admin users, allowing hackers to regain access even after cleanup.
The good news is that WordPress has improved significantly in recent years. Features like auto-updates have helped reduce vulnerabilities in the core CMS. However, poor security practices — such as using nulled plugins, weak passwords, and outdated themes — continue to put sites at risk.
As the WordPress Security developer documentation puts it:
Security is not about perfectly secure systems. Such a thing might be impractical or impossible to maintain. What security is, though, is risk reduction — not risk elimination. It’s about employing the appropriate controls available to you, within reason, to improve your overall posture and reduce the odds of making yourself a target.
With all this in mind, the real question is: How can you avoid these risks? While no system is 100% secure, choosing the right hosting provider is one of the most effective ways to protect your site.
Now, let’s go over the most effective ways to secure your WordPress site and prevent hacks.
1. Invest in secure WordPress hosting
A secure WordPress site starts with a secure hosting provider. No matter how many security plugins you install or how carefully you manage updates, your site is at risk if your hosting environment is vulnerable.
Many website owners focus on locking down WordPress itself, but often overlook where their site actually lives.
A poor hosting environment leaves you exposed to DDoS attacks, malware infections, weak firewalls, and outdated server software — all of which hackers actively exploit. On the other hand, a secure WordPress host removes much of the security burden from you by proactively blocking malicious traffic, scanning for threats, and applying security patches automatically.
A well-protected hosting platform should include:
- Enterprise-grade firewalls and DDoS protection to filter out harmful traffic before it ever reaches your site.
- Automated malware scanning and removal to catch infections before they spread.
- Secure server isolation, so if one site is compromised, it doesn’t affect others.
- Automatic software updates and patching, ensuring your server environment is always up to date.
- Daily backups and rollback options, so even if something goes wrong, you can restore your site instantly.
Most WordPress hacks don’t happen because of sophisticated exploits. They happen because outdated plugins, weak passwords, and poor server security leave the door wide open. And when hackers probe for weaknesses, they often start with the server itself.
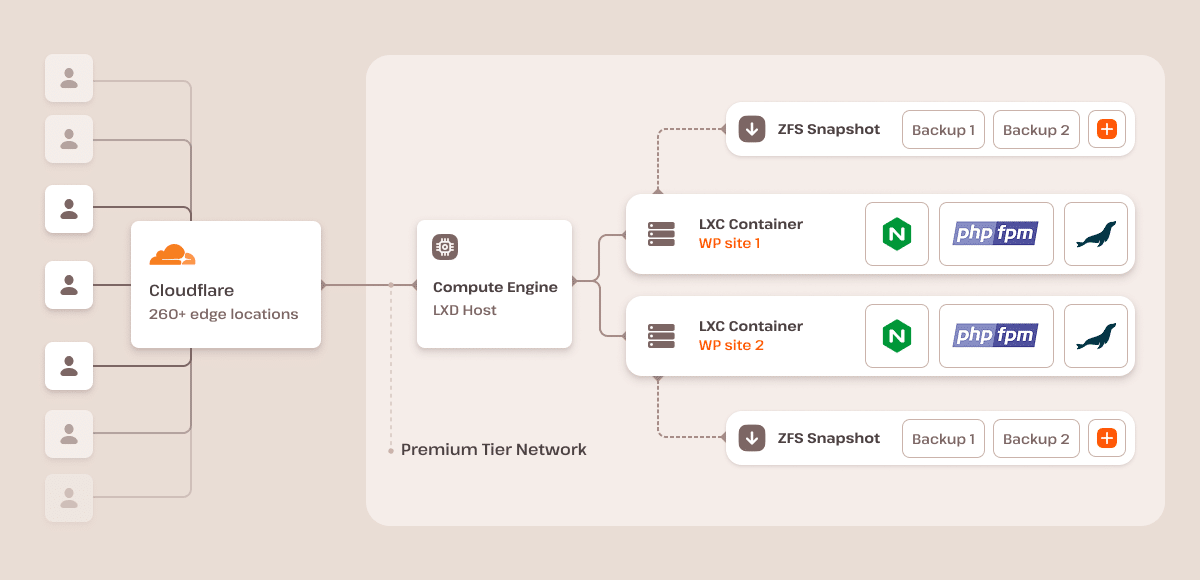
At Kinsta, security is built into the infrastructure
From the moment a site is deployed on our platform, it benefits from enterprise-level security protections that work quietly in the background, blocking malicious traffic, stopping brute-force attacks, and keeping core software up to date without site owners having to lift a finger.
Additionally, every site is completely isolated using Linux container technology, meaning one compromised site can’t affect others. This level of isolation is rarely found in traditional shared hosting, where multiple sites on the same server share resources and risks.
In addition to the robust security measures already mentioned, Kinsta also provides:
- Cloudflare’s enterprise-grade firewall, filtering out harmful traffic, blocking malicious bots, and mitigating brute-force attacks before they even reach your site.
- DDoS protection, ensuring your site remains online even when targeted by high-volume attacks.
- Automatic updates for plugins and themes, ensuring your site stays up-to-date with the latest security patches and features.
- Free SSL encryption, protecting all data exchanged between your site and visitors, with automatic renewal of SSL certificates to prevent security lapses.
- Daily automated backups, storing full-site snapshots for two weeks, allowing instant restoration in case of an attack or accidental data loss.
- Real-time uptime monitoring, with checks every three minutes — that’s 480 daily checks to catch issues before they become major problems.
- 24/7/365 support, providing real-time assistance in 10 languages whenever you need it, ensuring your site is always running smoothly and securely.
Security isn’t just about reacting to threats — it’s about preventing them before they happen. Kinsta’s security-first approach means that WordPress site owners can stop worrying about malware, DDoS attacks, and server vulnerabilities, and instead focus on what matters — growing their business.
2. Use the latest PHP version
PHP is the backbone of your WordPress site, so using the latest version on your server is essential for security, performance, and stability.
Each major PHP release receives active support for two years, during which security vulnerabilities and bugs are regularly patched. Once a version reaches the end of its life, it no longer receives updates, leaving any site running on it exposed to unpatched security flaws.
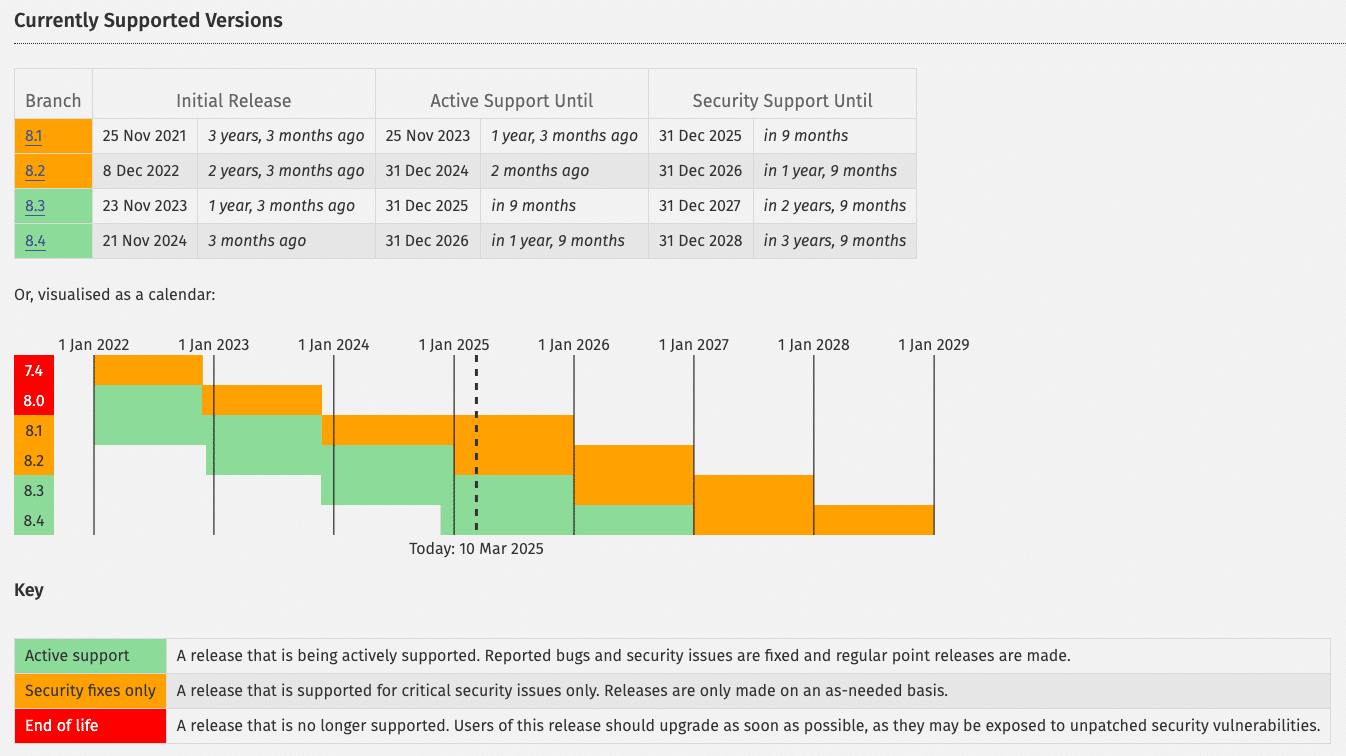
And yet, many WordPress sites still rely on outdated versions. According to the official WordPress Stats page, only 49.4% of WordPress sites run on PHP 8.1 or higher. This means over half of all sites are operating on PHP versions that are no longer supported. In fact, PHP 7.4, which lost security support at the end of 2022, still powers 31% of all WordPress sites. That’s a worrying statistic for security.
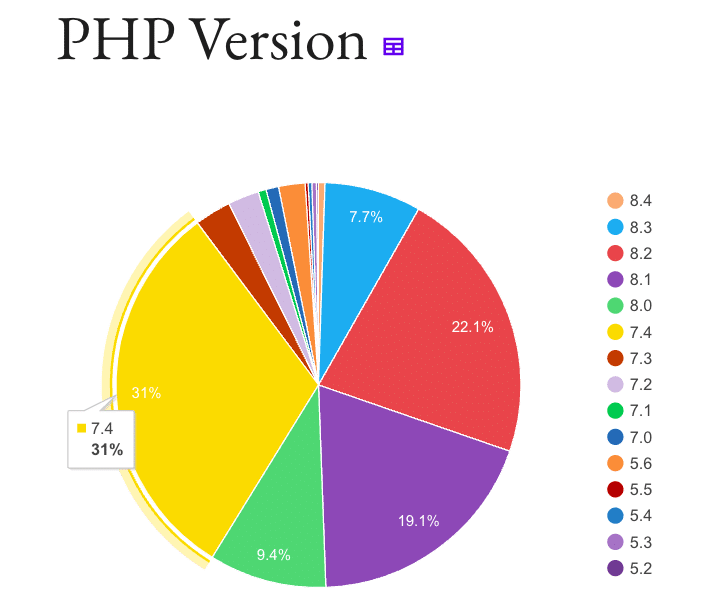
If you’re unsure which PHP version your site is using, you can check it in your hosting dashboard or use the WordPress Site Health tool, which provides a breakdown of its current setup.
Here at Kinsta, we strongly recommend running PHP 8.1 and above for optimal security and performance. However, we understand that a large portion of WordPress users — around 40.4% — still rely on older versions like PHP 7.4 and 8.0.
To ensure these users can continue to benefit from our secure hosting environment, we still support these versions while encouraging customers to transition to newer releases.
Switching between PHP versions is effortless. In the MyKinsta dashboard, simply go to the Tools tab, navigate to PHP Settings, and click the Change button to update your site’s PHP version instantly.
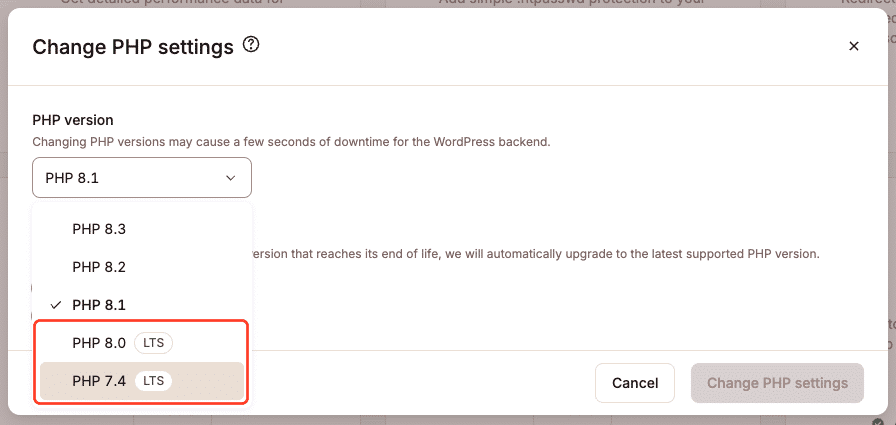
To make things even easier, Kinsta offers automatic PHP upgrades. If your site is running on a PHP version that is reaching end-of-life, our system automatically updates it to the latest supported version. This ensures that your site stays secure and fully optimized without requiring any manual intervention.
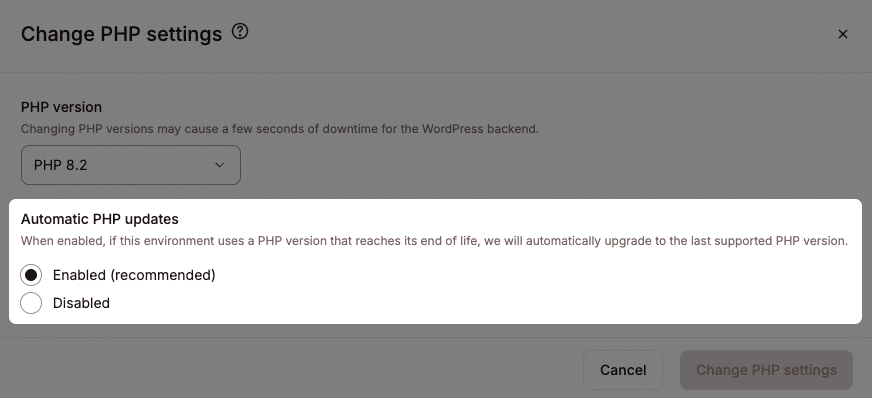
If you’re on a WordPress host that uses cPanel, you can typically switch PHP versions by selecting the Select PHP Version option under the Software category.
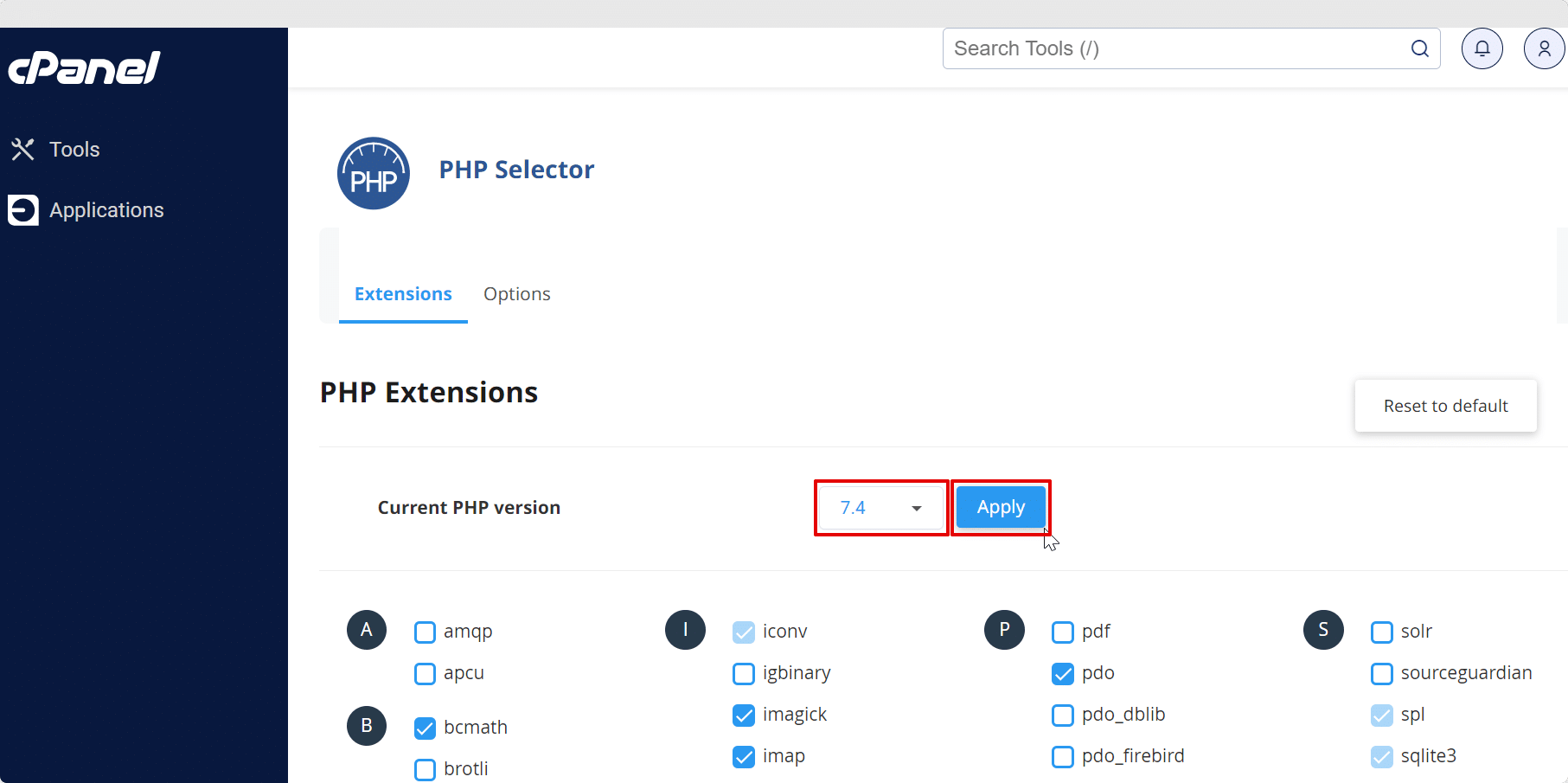
3. Always use the latest version of WordPress, plugins, and themes
Another very important way to harden your WordPress security is to always keep it up to date. This includes WordPress core, plugins, and themes (both those from the WordPress repository and premium).
These updates aren’t just about new features — they often contain critical security patches that fix vulnerabilities before hackers can exploit them.
In the early years of WordPress, the core software faced more security threats because updates weren’t always applied on time. WordPress took a major step toward improving security with the release of version 3.7, which introduced automatic updates for minor releases, including security and maintenance updates.
This significantly reduced the number of attacks on outdated core WordPress versions. However, while core WordPress is now more secure, plugins and themes have become the biggest attack surface.
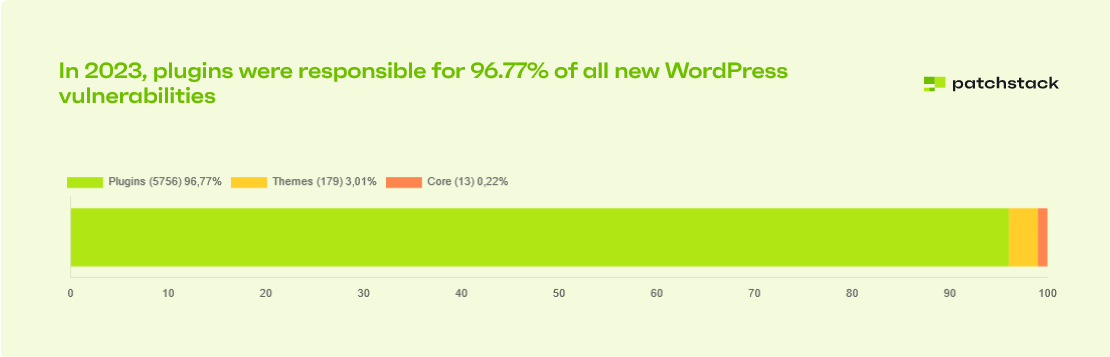
According to Patchstack, 96.77% of all new WordPress vulnerabilities in 2023 came from plugins, while themes accounted for just 3.01%, and core WordPress vulnerabilities were less than 1%.
This means the real security risk isn’t WordPress itself — it’s the third-party plugins and themes that extend its functionality.
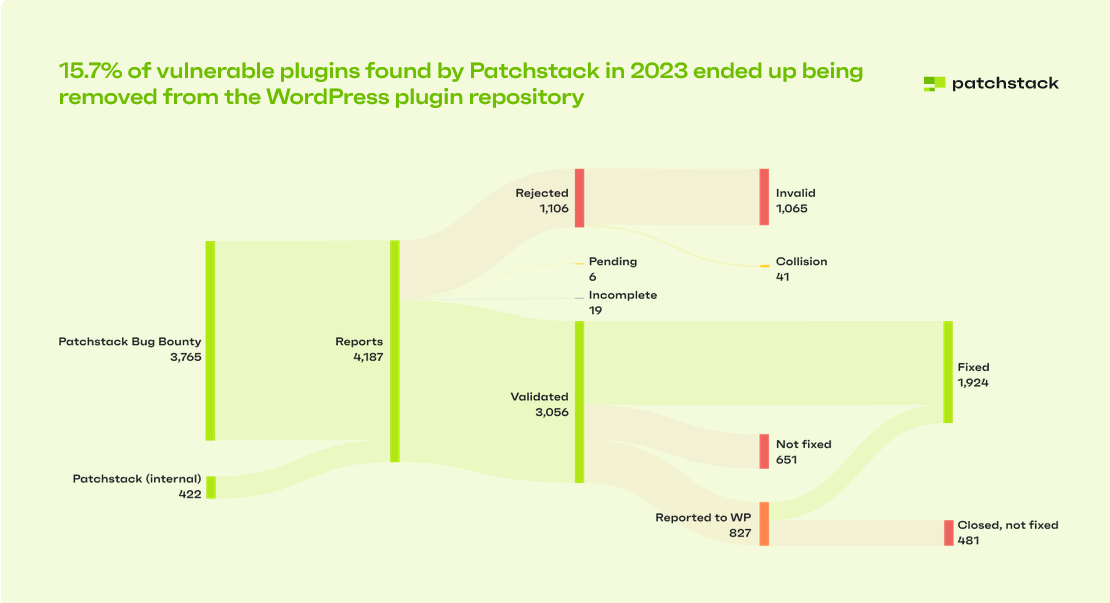
The risk is even greater when plugins are abandoned. In 2023, Patchstack reported 827 vulnerable plugins and themes to the WordPress team. Of these, 481 components were removed from the plugin repository due to abandonment — a 450% increase from 2022, when only 147 plugins and themes were flagged and 87 were removed.
This means thousands of WordPress sites were running plugins that no longer received updates and were easy targets for attackers.
Plugins and themes are the biggest sources of WordPress vulnerabilities, so keeping them updated should be a top priority. However, manually checking for updates across multiple plugins, themes, and sites can be overwhelming.
At Kinsta, we’ve made this process effortless with Kinsta Automatic Updates. This feature ensures that all plugins and themes — whether active or inactive — are updated daily. Any newly installed plugin or theme is also automatically added to Kinsta’s update system, ensuring you stay protected against vulnerabilities without needing to take action.
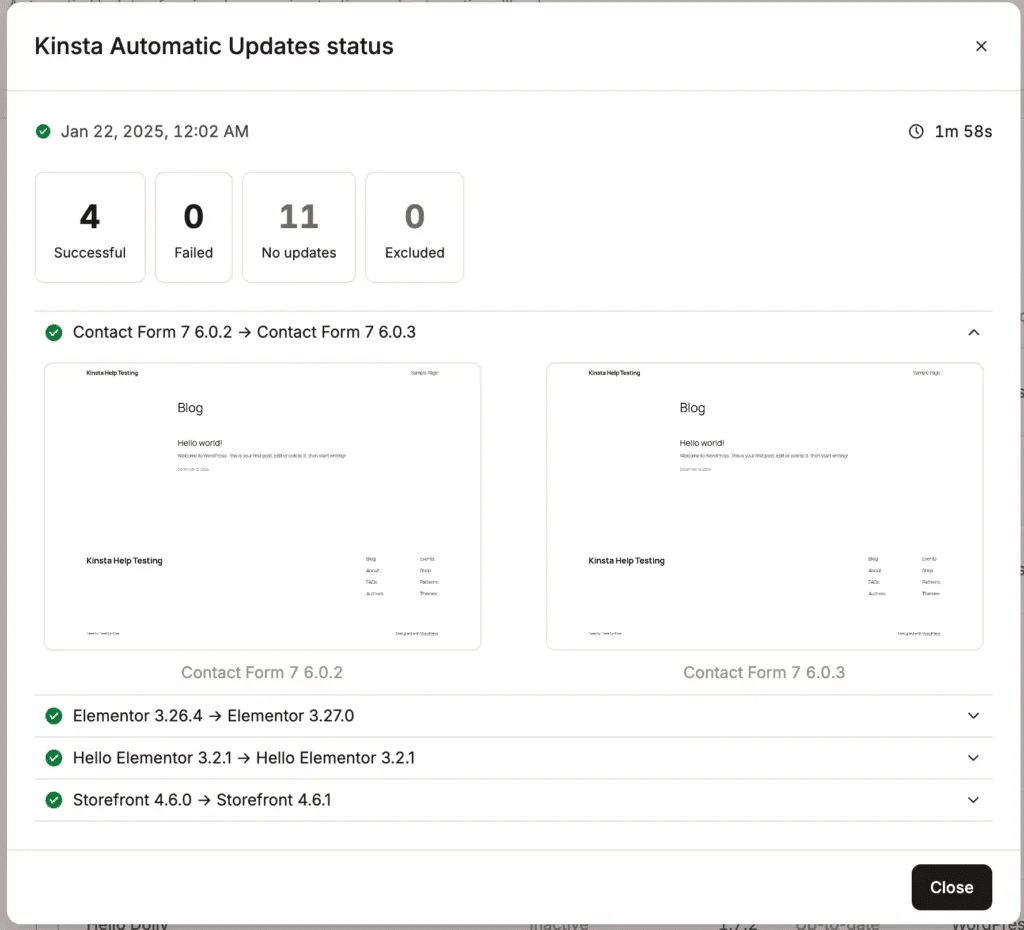
To prevent unexpected issues after updates, Kinsta runs visual regression testing on your site. This means we compare screenshots of your pages before and after an update to detect significant changes. You can read more about this feature and how it works in our documentation.
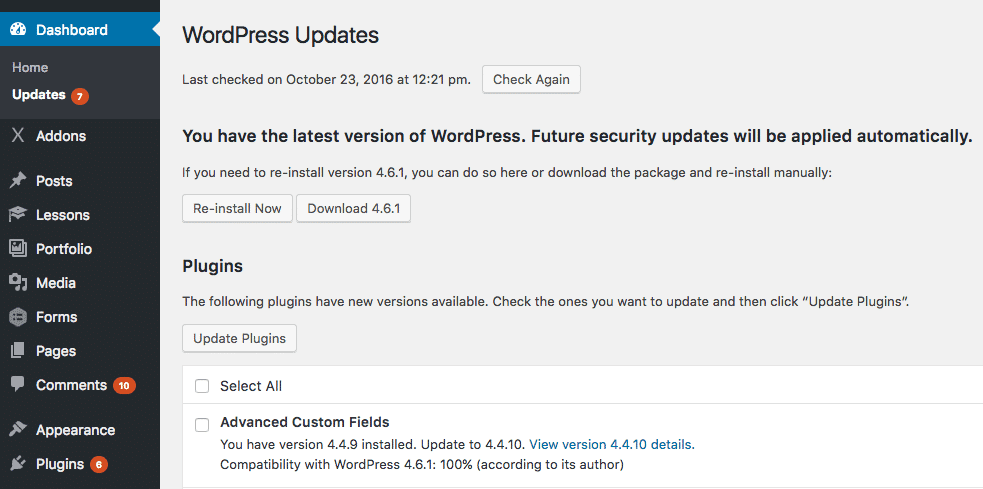
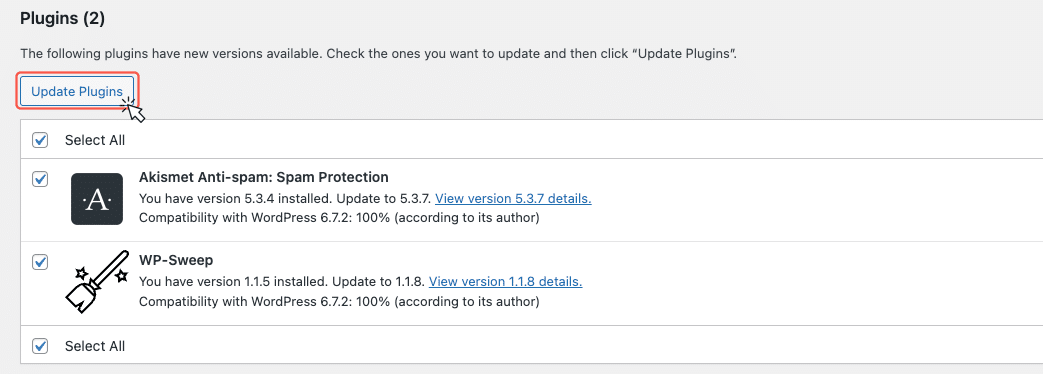
For users who prefer manual control, you can update plugins and themes directly through the MyKinsta dashboard or via the WordPress Updates section in your admin panel. Simply select the plugins you want to update and click Update Plugins.
It’s also important to be selective about which plugins you install. Patchstack has proven that many plugins in the WordPress repository are no longer maintained.
Before installing a plugin, check the Last Updated date and read user reviews. If a plugin hasn’t been updated in a long time or has poor ratings, it’s best to look for an alternative.
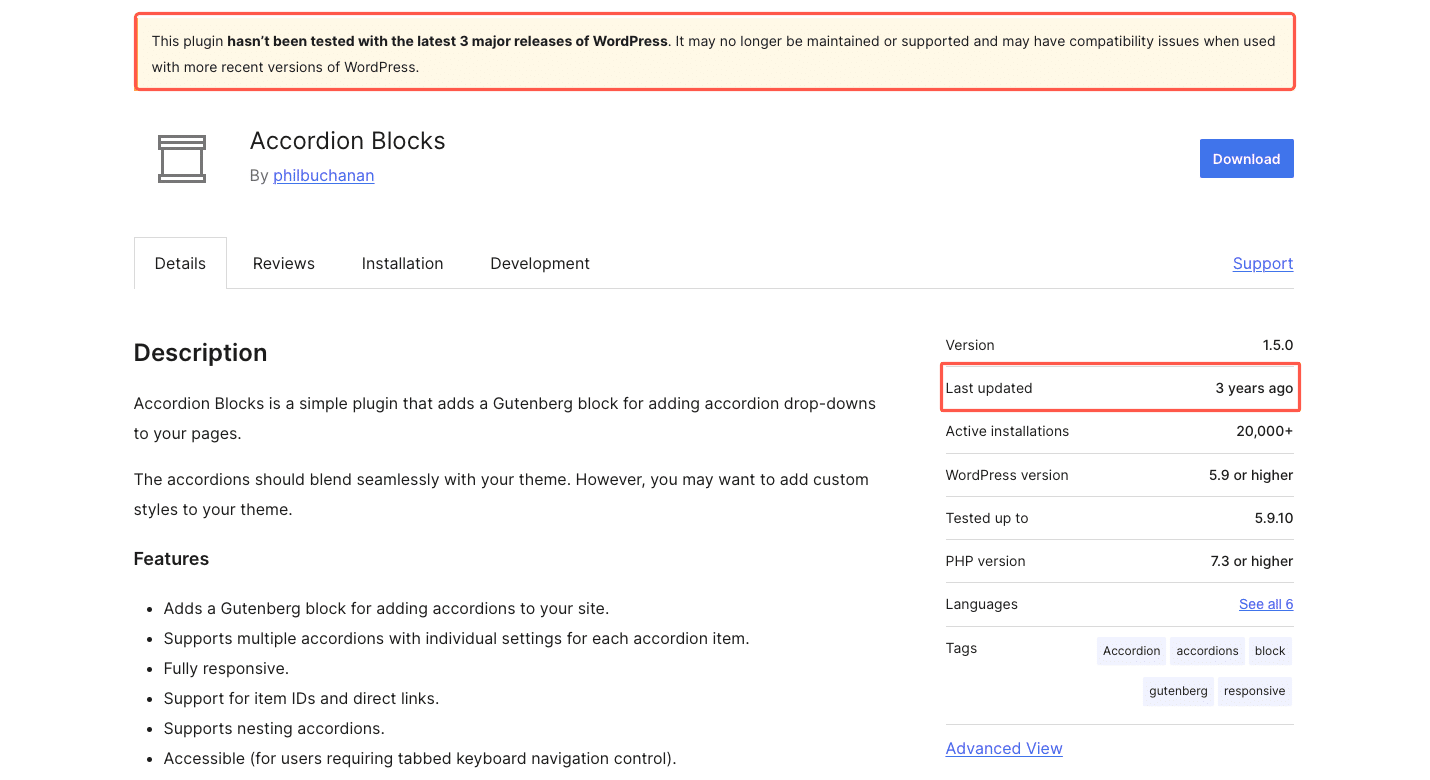
As seen in the image above, WordPress also flags outdated plugins with a warning at the top of their listing, making it easier to spot potential risks.
To stay ahead of WordPress security threats, resources like WPScan, which tracks over 10,000 vulnerabilities in WordPress core, plugins, and themes, and the Official WordPress Security Archive, which logs all security-related changes, help you stay informed about the latest risks.
You can dramatically reduce your site’s security risks by keeping WordPress, plugins, and themes updated, using a reliable update system, and being cautious about plugin selection.
4. Hide your WordPress version
Hiding your WordPress version is another way to reduce potential security risks. If hackers can see you’re running an outdated WordPress version, it makes your site a target for attacks that exploit known vulnerabilities.
By default, WordPress displays its version number in your site’s HTML source code.
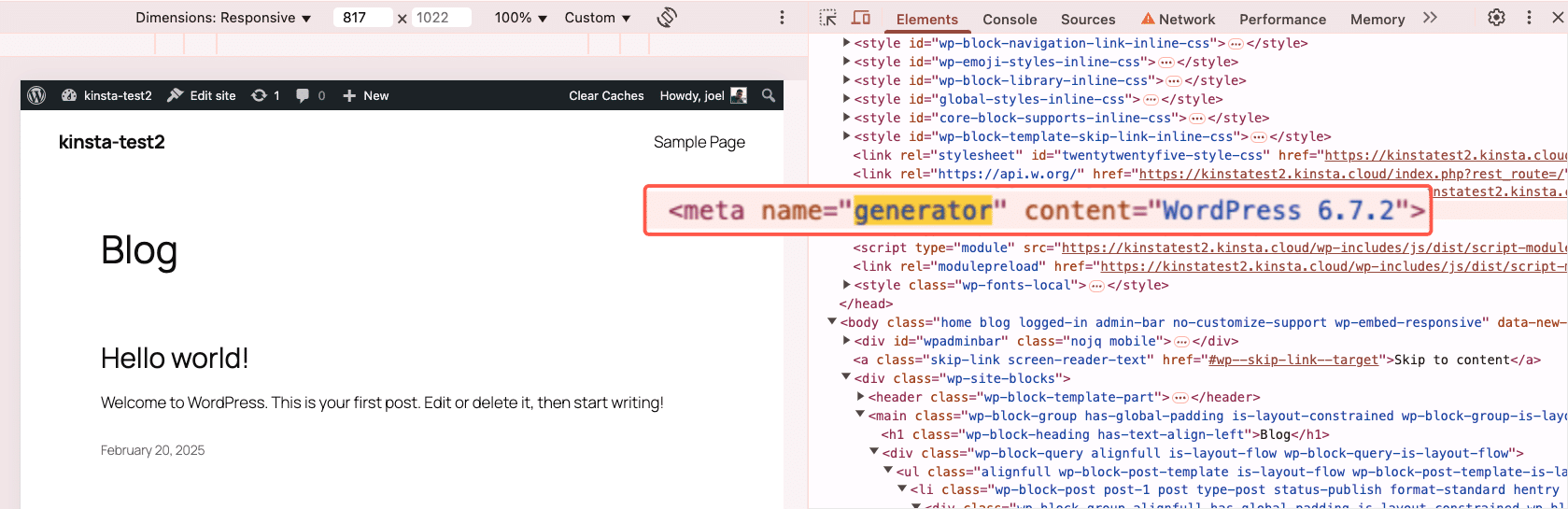
While the best approach is to always keep WordPress updated, you can remove the version number from the source code by adding this snippet to your theme’s functions.php file:
function wp_version_remove_version() {
return '';
}
add_filter('the_generator', 'wp_version_remove_version');For a simpler solution, the Perfmatters plugin allows you to hide the WordPress version with a single click, along with other performance and security optimizations.
5. Lock down your WordPress admin
While WordPress security by obscurity isn’t a foolproof solution, making it harder for hackers to find and exploit your admin panel reduces your exposure to brute-force attacks and malicious bots.
Hackers often target wp-admin because it’s the gateway to your site. If they can access your admin area, they can take full control — injecting malware, modifying files, or even locking you out.
Strengthening access to your WordPress dashboard adds an extra layer of security, ensuring that attackers cannot access your site even if a vulnerability exists elsewhere.
The most effective ways to secure your WordPress admin include:
- Changing the default login URL so attackers and bots can’t easily find it.
- Limiting login attempts to block brute-force attacks.
- Adding HTTP authentication to require an extra username and password before loading the login page.
- Restricting admin access to specific IPs using a firewall or web server rules.
These methods work together to prevent unauthorized login attempts and reduce the risk of admin panel exploits. Let’s review them one by one.
Changing your WordPress login URL
By default, WordPress sites use domain.com/wp-admin or domain.com/wp-login.php as their login URLs. The problem is that hackers and bots know this, too. They constantly scan sites, looking for login pages to attack.
Changing your login URL does not make your site invulnerable, but it makes it a much harder target, significantly reducing automated attacks.
To change your login URL, you can use free plugins like WPS Hide Login or premium solutions like Perfmatters. These plugins allow you to set a custom login path, making it much harder for attackers to find your admin login page. Just be sure to choose a unique URL that’s not commonly guessed by bots.
Limiting Login Attempts
Even with a hidden login URL, attackers may still try to guess passwords through brute-force attacks, where they attempt thousands of username-password combinations until they find the right one. By default, WordPress doesn’t limit login attempts, meaning bots can keep trying indefinitely.
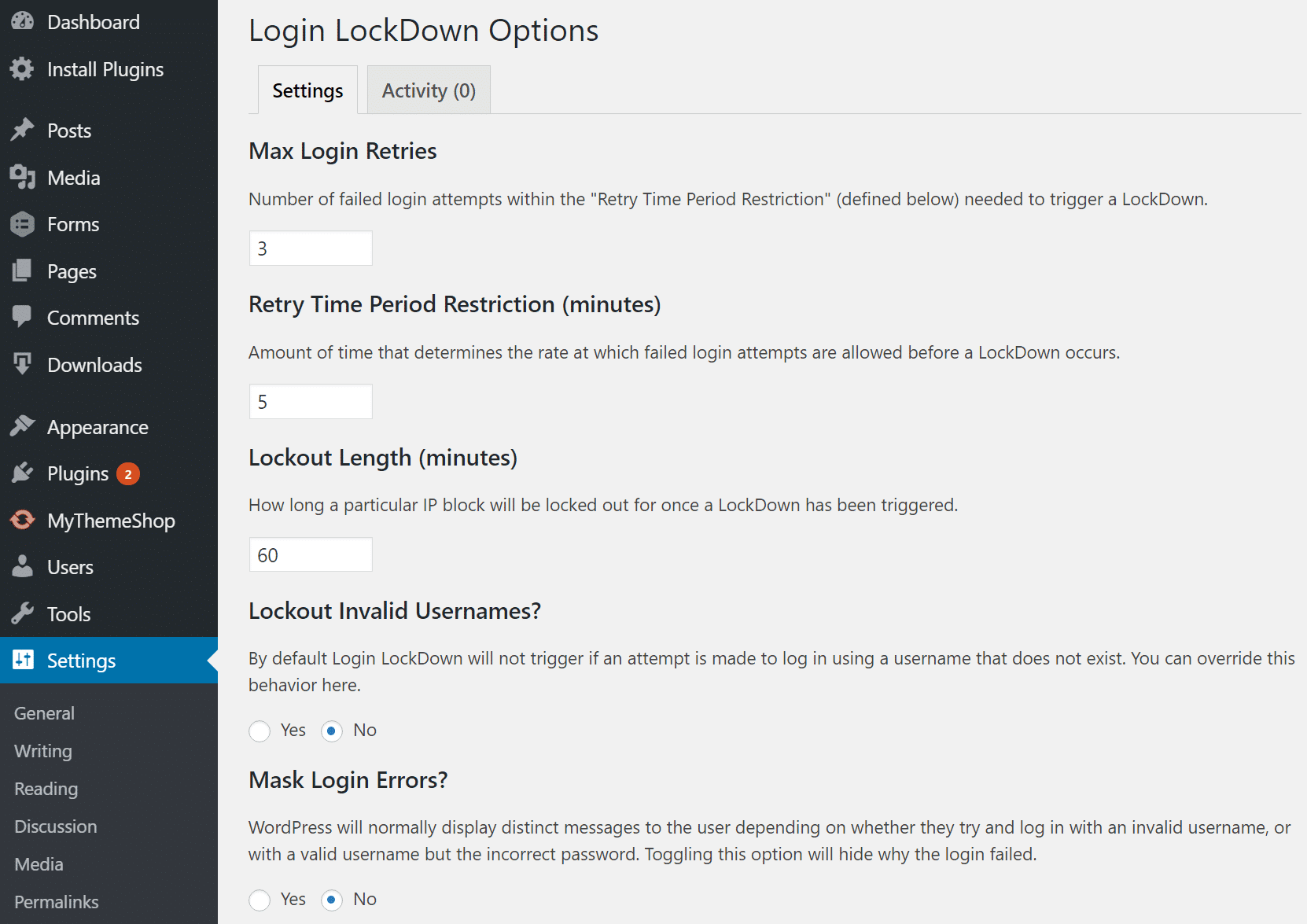
You can block these attacks by limiting the number of failed login attempts before an IP address is temporarily locked out. The Limit Login Attempts Reloaded plugin is a simple way to do this — it lets you configure lockout durations, set login attempt limits, and even allowlist or blocklist IPs.
For an alternative, Login Lockdown & Protection records IP addresses and timestamps of failed login attempts, blocking access if too many attempts occur in a short period. This helps prevent automated attacks while keeping legitimate users from getting locked out too easily.
Adding HTTP authentication for an extra layer of security
Another effective way to secure your login page is by adding an extra layer of password protection before anyone can even access it. This means that before someone sees the WordPress login screen, they first have to enter a username and password.
This method is highly effective but isn’t ideal for e-commerce or membership sites since users need to log in frequently. However, it can significantly reduce unauthorized login attempts for blogs, corporate sites, or personal projects.
Many hosting providers offer built-in tools for this. For example, Kinsta provides a Password protection feature in the MyKinsta dashboard under the Tools page.
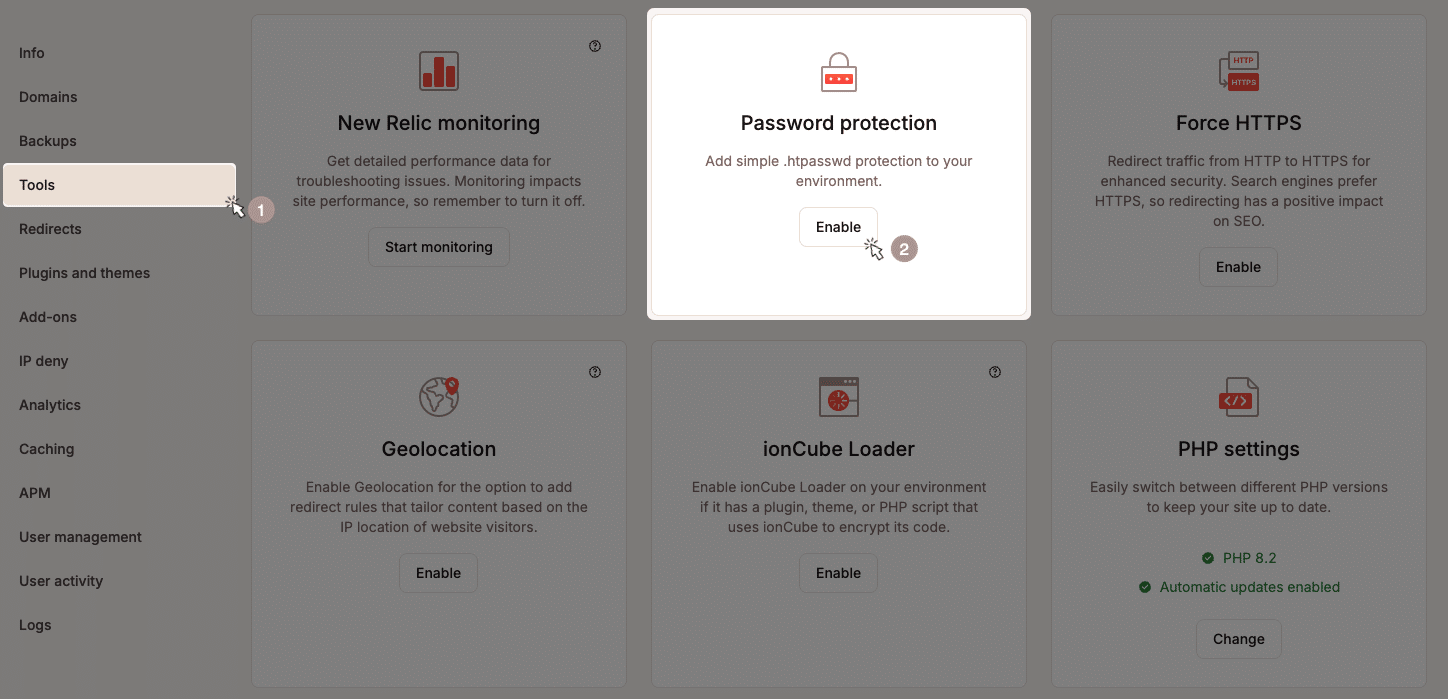
This feature enables HTTP authentication with just a few clicks, requiring users to enter an extra username and password before accessing the WordPress login page.
For Apache servers, this can be set up manually by creating a .htpasswd file. You can use this handy generator tool, and then upload the file to a directory under your wp-admin folder, such as:
home/user/.htpasswds/public_html/wp-admin/htpasswd/Then, create a .htaccess file with the following code and upload it to your /wp-admin/ directory. Make sure you update the directory path and username.
AuthName "Admins Only"
AuthUserFile /home/yourdirectory/.htpasswds/public_html/wp-admin/htpasswd
AuthType basic
require user yourusernameThe one caveat to doing it this way is that it breaks AJAX (admin-ajax) on the frontend of your site. Some third-party plugins require this. Therefore, you also need to add the following code to the above .htaccess file.
<Files admin-ajax.php>
Order allow,deny
Allow from all
Satisfy any
</Files>If you are running Nginx, you can also restrict access with HTTP basic authentication. Check out this tutorial.
Restricting Admin access by IP address
Hackers often use brute-force attacks to target the WordPress login page, trying thousands of password combinations until they break in. But if they can’t even reach the login screen, their attacks become useless.
You can do this by restricting access to specific IP addresses. This ensures that only users from approved locations can log in, blocking everyone else — even if they have the correct credentials.
If you use a Web Application Firewall (WAF) such as Cloudflare, its Zone Lockdown feature allows you to limit access to /wp-admin/ and /wp-login.php/ to only approved IP addresses.
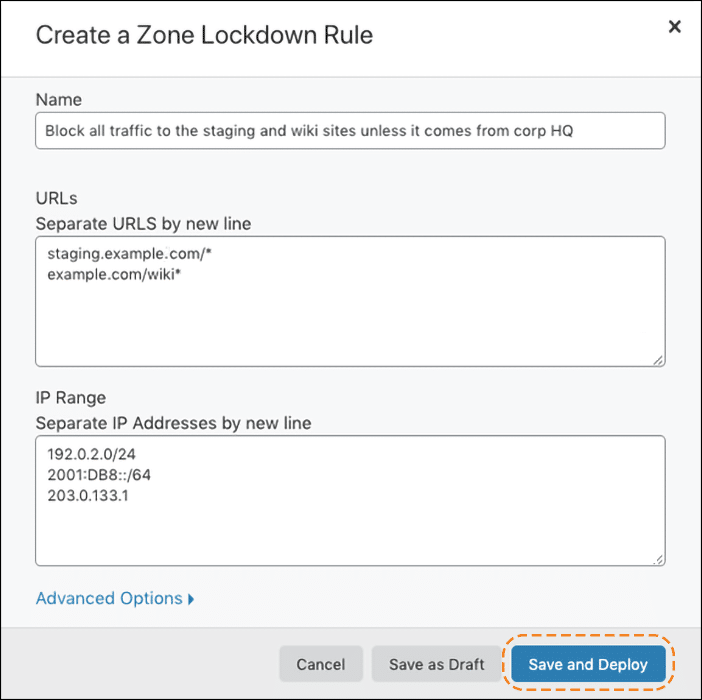
However, Cloudflare now recommends using custom WAF rules instead, as they provide more flexibility.
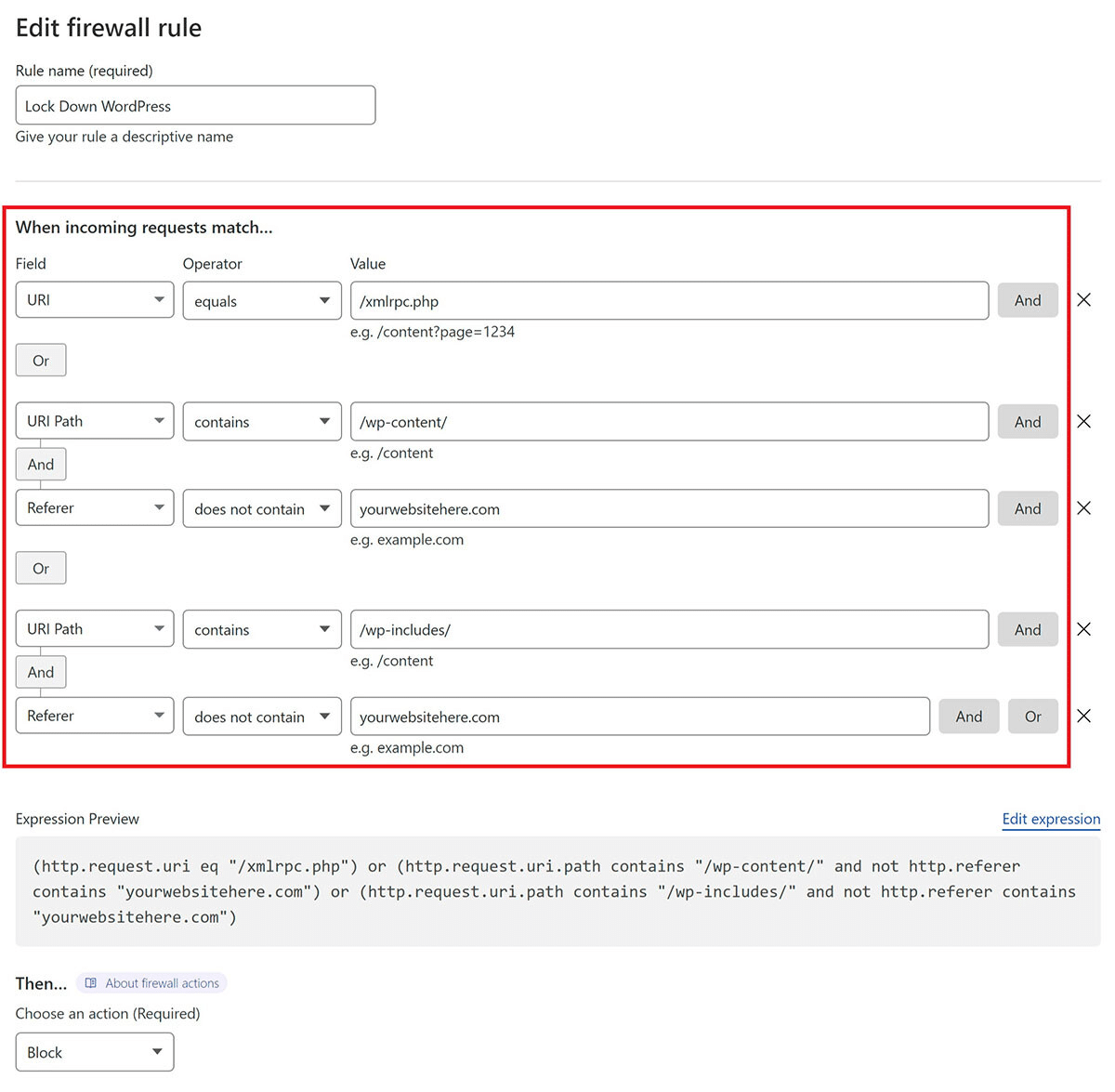
For Sucuri users, the firewall automatically restricts access to admin pages unless an IP is allowlisted. If you’re blocked, you can manually add your current IP to the allowlist from the Sucuri dashboard.
If you manage your own server and have a static IP address, you can manually restrict access via .htaccess (Apache) or Nginx configuration by specifying allowed IPs. However, this is only practical for users who don’t frequently change networks.
Again, this method is not ideal for e-commerce sites or membership platforms, as they rely on frequent access to the backend from multiple users. Blocking access by IP could prevent legitimate customers or team members from managing their accounts, making other security measures — such as two-factor authentication (2FA) and strong password policies — a better choice for those types of sites.
6. Use strong usernames and passwords
Weak credentials remain one of the easiest ways for hackers to break into a WordPress site. Every year, security reports show that millions of people still use passwords like “123456,” “password,” or “qwerty,” all of which can be cracked in seconds. Hackers rely on brute-force attacks, using automated scripts to guess login credentials rapidly.
To protect your site, always use long, complex passwords with a mix of uppercase and lowercase letters, numbers, and symbols. Managing strong passwords is easier than ever with tools like Google Password Manager, which suggests and securely stores passwords for you.
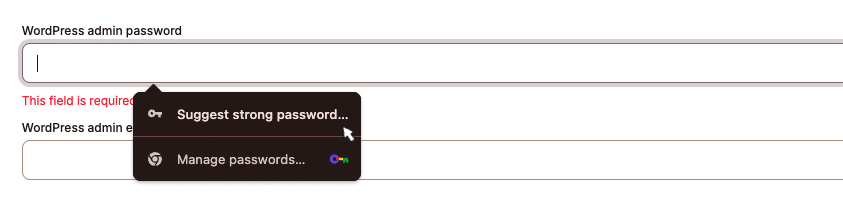
If you use Kinsta, our platform automatically generates strong passwords when setting up a new WordPress account. You can store them securely in a password manager like 1Password or LastPass, ensuring you never have to reuse passwords across different sites.

Another critical step is avoiding the default “admin” username. Hackers frequently target this username in brute-force attacks. Instead, create a unique administrator username and delete the default “admin” user. You can do this under Users > Add New in your WordPress dashboard.
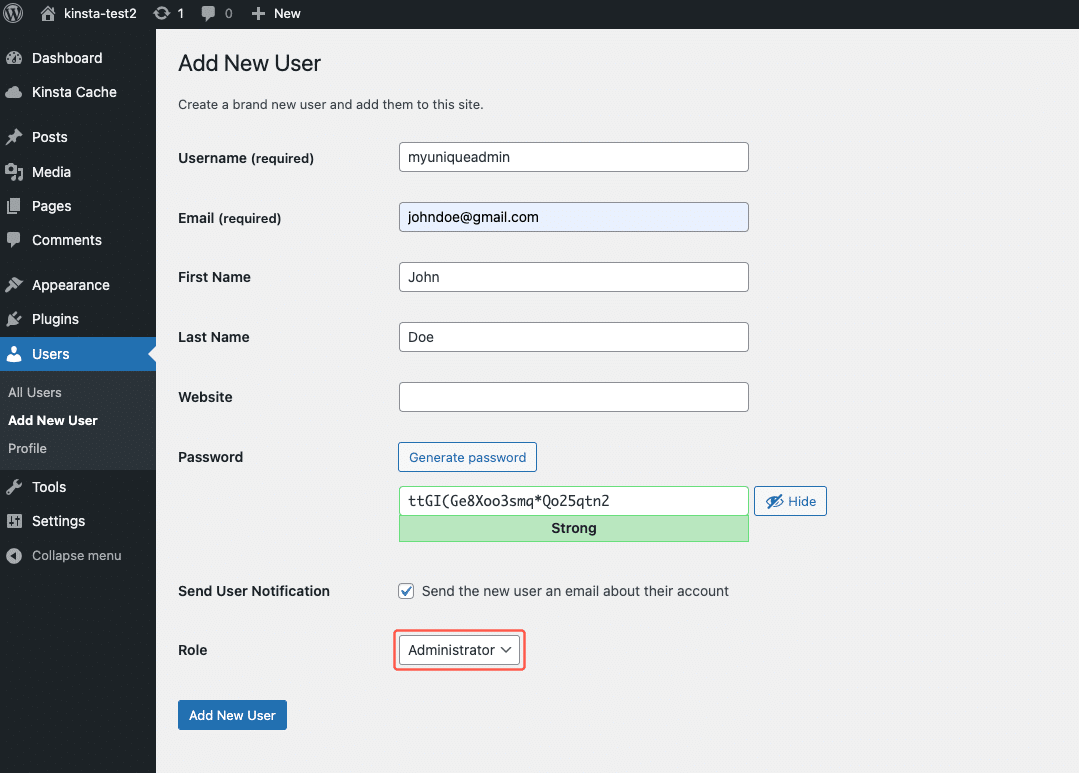
Once the new account is set up, delete the old one and reassign content to your new administrator account.
If you manage the database directly, you can rename your admin username in phpMyAdmin with the following command (always back up your database before making changes):
UPDATE wp_users SET user_login = 'newcomplexadminuser' WHERE user_login = 'admin';7. Enable two-factor authentication (2FA)
No matter how strong your password is, there’s always a risk of it being stolen or guessed. Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification before granting access.
This typically involves entering a one-time code generated by an authenticator app, SMS message, or security key. Since attackers rarely have access to both your password and your 2FA device, enabling 2FA is one of the most effective ways to prevent unauthorized logins.
There are two key areas where two-factor authentication should be enabled:
- Your hosting account: If someone gains access to your hosting provider’s dashboard, they could change passwords, modify DNS settings, or even delete your site. At Kinsta, we provide 2FA for MyKinsta, requiring a one-time code from an authenticator app like Google Authenticator to ensure only authorized users can access hosting accounts.
- Your WordPress login page: While WordPress doesn’t include built-in 2FA, you can enable it using plugins such as Google Authenticator or Two Factor Authentication. These plugins integrate with authenticator apps, requiring you to enter a one-time security code when logging in.
Once set up, your WordPress login page prompts you for an additional security code, significantly reducing the risk of unauthorized access — even if someone steals your password.
8. Use HTTPS for encrypted connections with an SSL certificate
One of the most overlooked ways to harden your WordPress security is to install an SSL certificate and run your site over HTTPS (Hypertext Transfer Protocol Secure).
HTTPS encrypts the data exchanged between your website and its visitors, preventing attackers from intercepting sensitive information. While many people assume SSL certificates are only necessary for e-commerce sites, the reality is that any website that collects login credentials, user data, or even just traffic analytics benefits from encryption.
Many hosting providers, including Kinsta, automatically issue free SSL certificates with wildcard support through our Cloudflare integration, making it easier than ever to secure your site.
If your site is still running on HTTP, here’s why you should switch immediately:
- Security: Without HTTPS, login credentials and user data are sent in plain text, making them easy targets for hackers. HTTPS encrypts this information, preventing man-in-the-middle attacks and securing all interactions on your site.
- SEO: Google has confirmed that HTTPS is a ranking factor. While it may be minor, a secure connection signals trustworthiness, potentially improving search visibility.
- Trust and credibility: Visitors look for security indicators like the padlock icon. According to an old survey by GlobalSign, 84% of shoppers abandon a purchase if data is sent over an unsecured connection, and 29% actively check for HTTPS before engaging with a site.
- Browser warnings: Chrome and other browsers now flag HTTP sites as “Not Secure,” discouraging visitors from continuing. Chrome also includes an option (Always use secure connections) to warn users before visiting sites that don’t support HTTPS.
- Referral data: HTTPS preserves referral data in Google Analytics, while HTTP traffic often gets misclassified as direct traffic, making it harder to track sources.
- Performance: HTTPS enables HTTP/2, improving site speed with better multiplexing and compression. TLS 1.3 further optimizes performance by reducing handshake times. If your site is hosted on Kinsta, both are supported across all servers, and HTTP/3 is fully supported thanks to our Cloudflare integration, ensuring even faster and more reliable connections.
To enforce HTTPS on your WordPress site, you can define SSL enforcement in your wp-config.php file by adding the following line:
define('FORCE_SSL_ADMIN', true);If you’re still running on HTTP, now is the time to migrate. Switching to HTTPS is no longer optional — it’s an essential step for security, SEO, and user trust. If you need help, check out our WordPress HTTPS migration guide to ensure a smooth transition.
9. Add the latest HTTP security headers
Another way to strengthen your WordPress security is by implementing HTTP security headers. These instruct browsers on how to handle your site’s content, helping to prevent attacks like XSS (Cross-Site Scripting), clickjacking, and protocol downgrade attacks. They’re typically configured at the server level. The most important ones include:
- Content-Security-Policy (CSP): Restricts which resources (scripts, styles, images) can load on your site to prevent malicious injections.
- Strict-Transport-Security (HSTS): Forces browsers to always use HTTPS, ensuring secure connections.
- X-Frame-Options: Prevents your site from being embedded in iframes, protecting against clickjacking.
- X-Content-Type-Options: Stops browsers from MIME-sniffing, reducing the risk of certain types of attacks.
To check which security headers are active on your WordPress site, open Chrome DevTools, go to the Network tab, and look at the response headers of your site’s initial request.
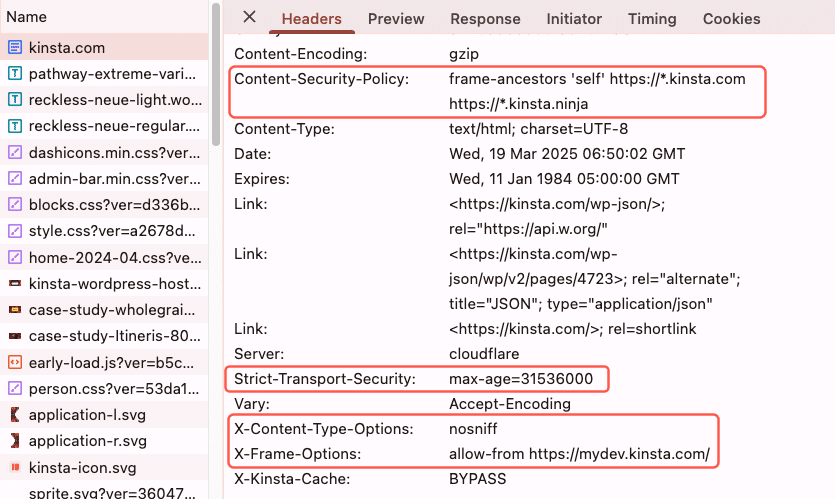
You can also scan your site using the free tool securityheaders.io to see which headers are in place and which are missing.
10. Always use secure connections
We can’t stress enough how important it is to use secure connections! Ensure that your WordPress host takes precautions, such as offering SFTP or SSH, as they encrypt data during transmission, preventing attackers from intercepting sensitive information. It is a more secure method than standard FTP.
At Kinsta, we support only SFTP connections to keep your data safe, and unlike most hosts that use port 22, each site at Kinsta has a randomized port for added security. You can find your SFTP details in the MyKinsta dashboard.
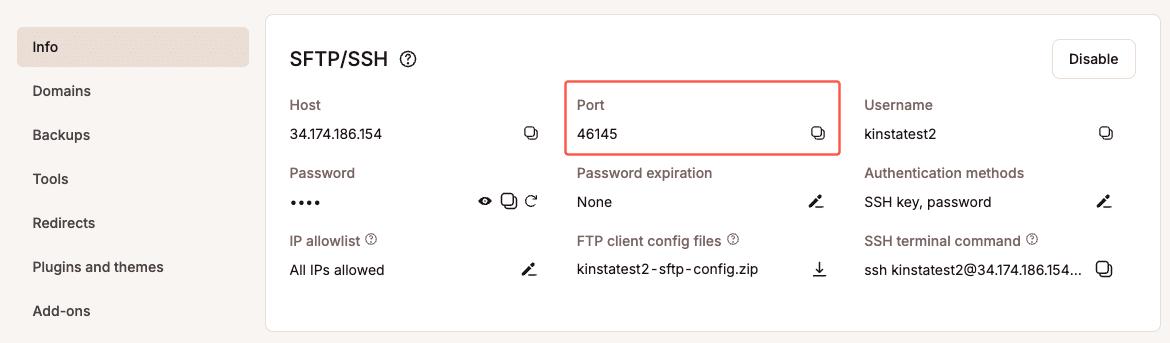
Beyond server security, securing your home network is just as important. A compromised home router could expose critical data about your WordPress sites. To reduce risk:
- Disable remote management (VPN) unless absolutely necessary.
- Use a non-default private IP range instead of 192.168.1.1 (like 10.9.8.7 instead).
- Enable strong encryption on your WiFi network.
- Allowlist IP addresses to restrict access to trusted devices.
- Keep your router firmware up to date to patch vulnerabilities.
Also, be cautious when logging into WordPress from public networks. Free WiFi at cafés or airports is not secure, and hackers can easily intercept traffic. If you must access your site on a public network, use a trusted VPN service like ExpressVPN or NordVPN to encrypt your connection and hide your IP from potential attackers.
11. Disable file editing in your WordPress dashboard
WordPress allows administrators to edit theme and plugin files directly from the dashboard using either the Theme File Editor or Plugin File Editor.
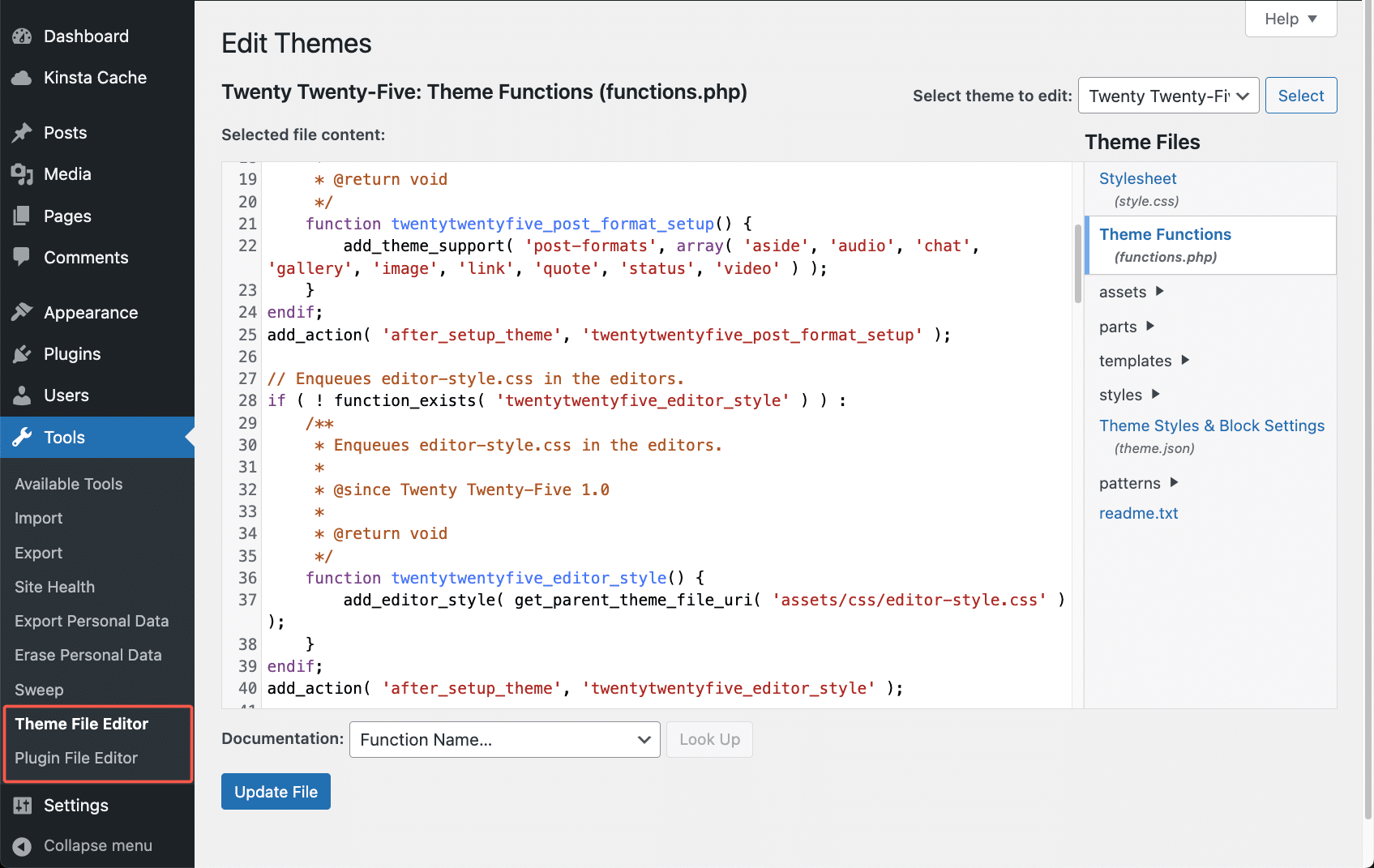
While this feature may seem convenient, it can pose a serious security risk — especially on sites with multiple users. If an attacker gains access to an admin account, the first thing they might do is modify PHP files to inject malicious code.
Even for site owners, editing files directly in the dashboard is risky. A small coding error could lead to the white screen of death, making your site inaccessible. It’s always safer to edit files locally and upload them via SFTP, preferably on a staging environment first.
To disable file editing and prevent unauthorized modifications, add the following line to your wp-config.php file:
define('DISALLOW_FILE_EDIT', true);For added security, consider disabling file modifications entirely, which prevents plugin and theme installations or updates through the dashboard:
define('DISALLOW_FILE_MODS', true);12. Harden your wp-config.php file
Your wp-config.php file is one of the most critical components of your WordPress installation. It stores database login credentials, authentication keys, and other sensitive information, making it a primary target for attackers. Securing this file is an essential step in protecting your site.
Here are three ways to protect your wp-config.php file:
- Move wp-config.php: By default, wp-config.php is located in the root directory of your WordPress installation (
/public_html/). Moving it to a non-www-accessible directory adds an extra layer of protection. While this method works for many hosting providers, Kinsta clients should not attempt it, as our security restrictions already prevent unauthorized access towp-config.php. - Update WordPress security keys: WordPress security keys (
AUTH_KEY,SECURE_AUTH_KEY,LOGGED_IN_KEY,NONCE_KEY) encrypt information stored in cookies, making your site more secure. If your site has gone through multiple migrations or ownership changes, it’s a good idea to generate new security keys. You can use the WordPress secret-key generator to create fresh keys and update them inwp-config.php. - Change file permissions: The default file permission for
wp-config.phpis usually 644, which allows other users on the same server to read it. For better security and according to the WordPress documentation, change its permissions to 440 or 400, restricting access to only the file owner. This can be done through an FTP client or command line. If you’re unsure, check with your hosting provider to confirm the best settings for your environment.
13. Check file and server permissions
Proper file and server permissions are essential for securing your WordPress site. If permissions are too loose, unauthorized users could gain access and modify files. If they are too strict, critical site functions may break. Striking the right balance ensures security while maintaining functionality.
File permissions determine who can read, write, or execute files, while directory permissions control access to folders and the ability to modify contents. For WordPress, the recommended permissions are:
- Files: Should be set to 644 or 640, except for
wp-config.php, which should be 440 or 400 to prevent unauthorized access. - Directories: Should be 755 or 750 to allow WordPress to function properly while restricting unnecessary access.
- Never use 777 permissions, even for upload directories, as this allows unrestricted access, making your site vulnerable.
You can check and adjust file permissions using an FTP client or a security plugin like Solid Security, which scans your site for incorrect permissions.
For a detailed guide on changing file permissions, refer to the official WordPress documentation to ensure your settings follow best security practices.
14. Harden database security
Securing your WordPress database adds an extra layer of protection against attacks. One simple way to do this is by using a unique database name instead of the default format, which often includes the site’s name, making it easier for hackers to identify.
For example, if your site is called Volleyball Tricks, your database might be named wp_volleyballtricks by default. Changing it to something less predictable makes it harder to target.
Another important step is modifying the default database table prefix from wp_ to something more obscure, like 39xw_, which helps prevent automated attacks that target standard table structures. This can be done during WordPress installation or changed later with the right precautions.
If you need guidance, this step-by-step guide explains how to change the WordPress table prefix manually or using plugins.
15. Disable XML-RPC
XML-RPC has become a common target for brute-force attacks in recent years. One of its hidden vulnerabilities is the system.multicall method, which allows multiple commands to be executed within a single HTTP request.
While this was originally intended as a useful feature, attackers exploit it to send thousands of login attempts at once, making brute-force attacks more efficient.
Some plugins, like Jetpack, still rely on XML-RPC, but most WordPress sites don’t need it. If you’re unsure whether XML-RPC is enabled on your site, you can use the XML-RPC Validator tool. Running your site through the tool confirms whether XML-RPC is active.
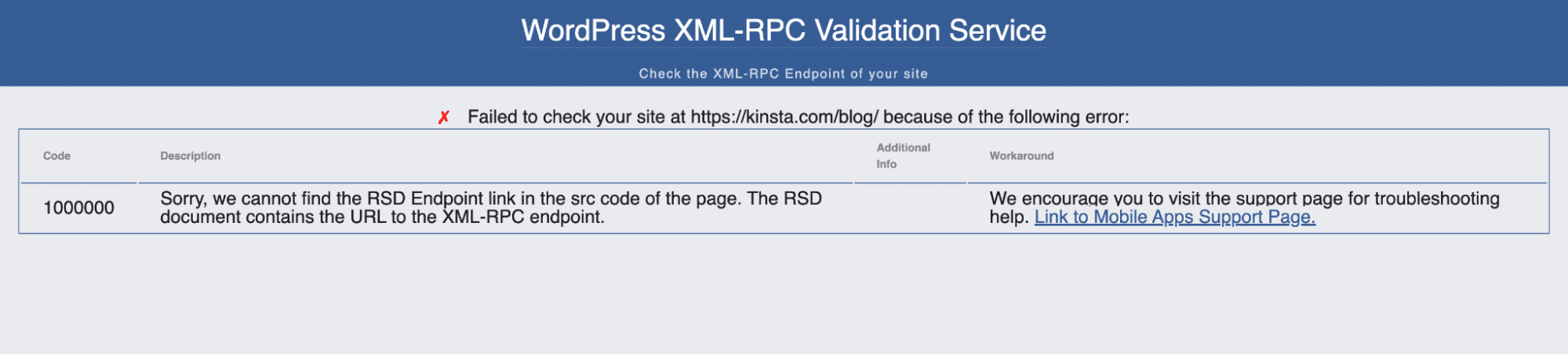
If you don’t need XML-RPC, disabling it can improve your site’s security. You can:
- Install the Disable XML-RPC-API plugin to turn it off completely.
- Use the Perfmatters plugin to disable XML-RPC while also improving site performance.
For Kinsta customers, there’s no need to take any action. When an XML-RPC attack is detected, a security rule is automatically added to the Nginx config, blocking the request and returning a 403 error.
location ~* ^/xmlrpc.php$ {
return 403;
}If your site doesn’t rely on XML-RPC, disabling it is an easy way to reduce your attack surface and improve WordPress security.
16. Prevent hotlinking
Hotlinking occurs when another website directly links to your images, using your bandwidth instead of hosting the file on their own server. While this might seem harmless, it can lead to increased server costs and slower site performance, especially if a high-traffic site is linking to multiple images.
A well-known example is when The Huffington Post hotlinked a cartoon from The Oatmeal, causing excessive bandwidth usage and racking up over $1,000 in additional hosting costs.
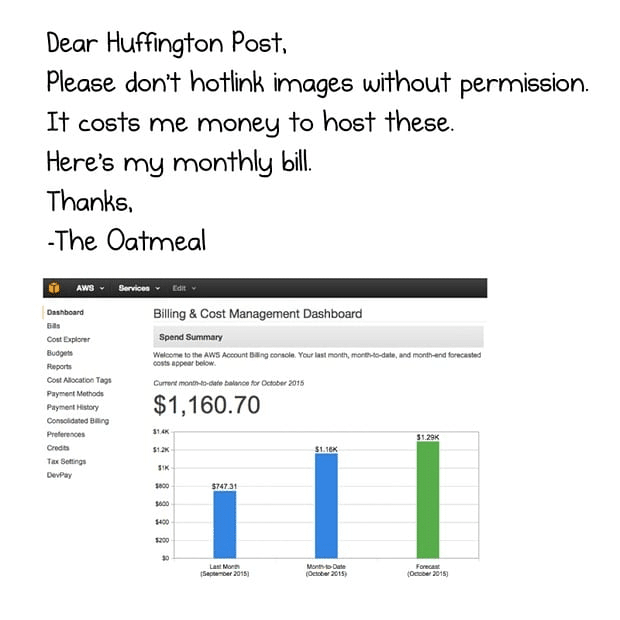
To prevent hotlinking, you can configure your server settings or CDN to block unauthorized image requests:
- Apache: Add a rule in your
.htaccessfile to restrict image requests to your own domain. - NGINX: Modify your configuration file to block requests from external sources.
- CDN protection: Most CDNs, including Cloudflare and KeyCDN, offer built-in hotlink protection that can be enabled in their settings.
17. Use WordPress security plugins
There are many WordPress security plugins designed to help protect your site from threats. While a secure hosting environment is the first line of defense, adding an extra layer of security with a plugin can help monitor, detect, and prevent potential vulnerabilities.
Some of the most popular security plugins include:
- Sucuri Security
- WordFence Security
- MalCare Security
- SecuPress
- Solid Security (Formerly iThemes Security)
Each of these plugins offers different security features, such as:
- Enforcing strong passwords and password expiration policies
- Logging user actions to track changes and suspicious behavior
- Scanning for malware and file modifications
- Implementing two-factor authentication (2FA)
- Adding reCAPTCHA protection for login forms
- Setting up firewalls, IP allowlisting, and blocklisting
- Monitoring DNS changes and blocking malicious networks
One particularly useful feature found in many security plugins is a checksum utility, which scans WordPress core files and checks them against the official versions from WordPress.org. If unauthorized modifications are detected, this may indicate a hack or malicious code injection.
Make sure to read our thorough guide on file integrity monitoring.
For multisite or multi-author WordPress setups, WP Security Audit Log is another great plugin that provides a detailed activity log, tracking changes to logins, passwords, themes, widgets, posts, and WordPress updates. It allows administrators to monitor user activity in real time, improving security and accountability.
At Kinsta, every site is protected by Cloudflare and Kinsta firewalls, with real-time security monitoring and malware removal at no cost. We check site uptime every three minutes and respond immediately to any issues, ensuring a secure and resilient hosting environment.
18. Always take backups
No matter how many security measures you put in place, no site is 100% safe. Backups are your last line of defense in case of hacks, accidental deletions, or major site failures. Yet, many site owners neglect regular backups — only realizing their importance when disaster strikes.
Most managed hosting for WordPress providers offer built-in backups. At Kinsta, backups are handled at the server level, with six different types, including automated daily backups and one-click restore options in MyKinsta, ensuring your site can be quickly recovered if anything goes wrong.
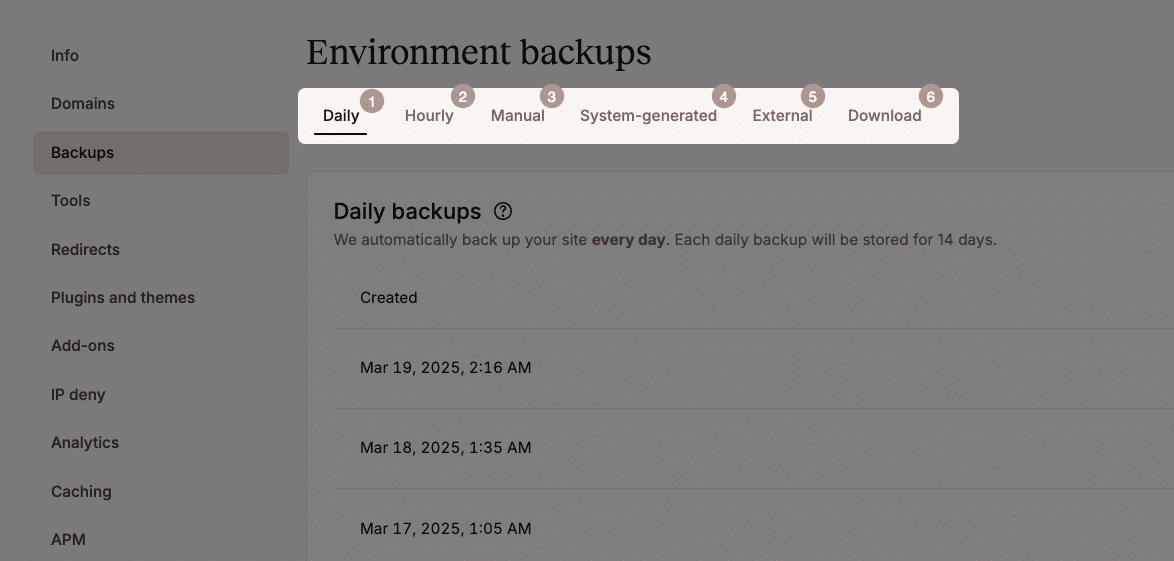
If your hosting provider doesn’t offer backups, there are several backup services and plugins available:
- Backup services like VaultPress, CodeGuard, and BlogVault store backups securely in the cloud.
- Backup plugins like UpdraftPlus, BackupBuddy, and WP Time Capsule allow you to save backups to external storage like Google Drive, Amazon S3, or Dropbox.
19. DDoS protection
DDoS (Distributed Denial of Service) attacks flood a website with massive amounts of traffic, overwhelming its resources and causing downtime. Unlike traditional hacks, DDoS attacks don’t compromise data or inject malware, but they can take a site offline for hours or even days, leading to lost revenue and frustrated visitors.
One of the most effective ways to protect against DDoS attacks is by using a third-party security service like Cloudflare or Sucuri. These services act as a protective shield, filtering out malicious traffic before it reaches your server. They also hide your origin IP address to make it harder for attackers to target your site directly.
For Kinsta users, DDoS protection is built in through our free Cloudflare integration, which automatically detects and mitigates all types of DDoS attacks, including UDP, ICMP, SYN/ACK floods, DNS amplification, and Layer 7 attacks.
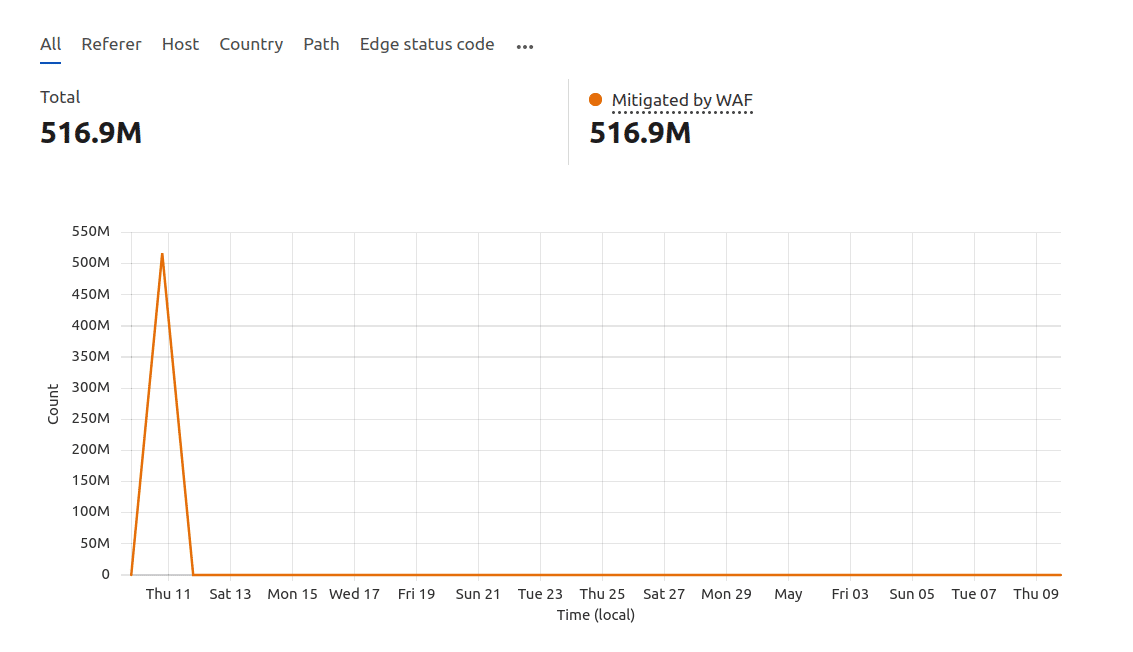
A real-world example of DDoS protection in action: A financial company migrated to Kinsta while facing a massive DDoS attack. Immediately after going live, their site was bombarded with millions of requests, causing disruptions.
Our SysOps team quickly worked with Cloudflare to block suspicious traffic. Within 27 minutes, over 516 million malicious requests were mitigated, ensuring the site remained online.
If you rely on your website for business, investing in a strong DDoS protection system is crucial to prevent downtime and keep your site running smoothly.
Summary
As you can see, there are numerous ways to harden your WordPress security. Using strong passwords, keeping core and plugins updated, and choosing a secure managed WordPress host all play a key role in keeping your site safe.
Like we said, your web host plays a crucial role, and at Kinsta, security is built into our infrastructure. With our Cloudflare integration, every site benefits from automatic DDoS mitigation, an enterprise-level firewall, and real-time malware scanning with free malware removal. Our dual firewall system blocks threats before they reach your site, while daily automated backups and proactive uptime monitoring ensure your site stays online and secure.
For many of you, your WordPress site is your source of income, so taking action now on security best practices is essential. Protect your site with hosting that does the heavy lifting for you. Switch to Kinsta today and get your first month free.
Have any important WordPress security tips we missed? Let us know in the comments!